Risk Register analysis
(→Strong points) |
(→How Risk register is used ?) |
||
| (105 intermediate revisions by one user not shown) | |||
| Line 1: | Line 1: | ||
Developed by Dorothea Georgiadou | Developed by Dorothea Georgiadou | ||
| − | In an age where the economic, social, and political environment is constantly shifting, there is an urgent need to study the risks that may threaten the success of a project. It is particularly important to study the risks that may adversely affect the project and lead to events that might have as a | + | In an age where the economic, social, and political environment is constantly shifting, there is an urgent need to study the risks that may threaten the success of a project. It is particularly important to study the risks that may adversely affect the project and lead to events that might have as a consequence the exceeding of the agreed budget and time. For this reason, the risk management planning should identify and describe in detail the potential risks by providing the needed information for the actions that should be done for eliminating their negative impact. The high uncertainty that exists in projects necessitates the use of a management tool that will control the risks. <ref name="Pmi"> Project Mangement Institute. "Practice standard for project risk management." Project Management Institute, 2009. </ref> In this article the risk management framework ‘’Risk register’’ is explained. The risk register is a tool that covers and studies many aspects of risk management processes. More specifically, the aim of this article is to explain how this tool can be used to document the outcomes of the risk management processes. <ref name="sag"> Risk register developement and implementation for construction projects, Ivana Burcar Dunović, Mladen Radujković, Mladen Vukomanović, 2013, Retrieved from: https://doi.org/10.14256/JCE.722.2012 </ref> The article provides a description of the tool along with the reasons that it should be used. It is a framework that aims to record the information from the processes related to the identification, assessment, responding, and monitoring of potential risks. <ref name="sag"> Risk register developement and implementation for construction projects, Ivana Burcar Dunović, Mladen Radujković, Mladen Vukomanović, 2013 </ref>. Finally, the article analyzes along with the benefits also the limitations of this risk management tool. |
| − | == Why use | + | |
| − | In an ever-changing environment, a projects’ success is associated with a high level of uncertainty | + | == Why use Risk Register? == |
| + | In an ever-changing environment, a projects’ success is associated with a high level of uncertainty. In the ''‘Practice Standard for Project Risk Management’'', risk management is an approach that plays a vital role in the strategic and decision-making processes since adjustments in the project management planning can be done after the identification of the projects’ challenges. The risk register framework is used to support the risk management process in order to eliminate the negative impact that the various threats might have on a project. Threats could come from the external and internal environment of the company. The external risks are associated with the economic, social, political, and technological environment, while the internal threats include risks that are related to human actions and estimations. <ref name="Pmi" /> <ref name="sag"> Risk register developement and implementation for construction projects, Ivana Burcar Dunović, Mladen Radujković, Mladen Vukomanović, 2013 </ref>. For example, it is possible for people to make wrong estimations because of inexperience and underestimation of some threats. This high level of uncertainty makes it increasingly necessary to use a model that assists the risk management process in a more effective way. <ref name="Pmi" /> <ref name="sag"> Risk register developement and implementation for construction projects, Ivana Burcar Dunović, Mladen Radujković, Mladen Vukomanović, 2013 </ref>. | ||
=== The role of Risk Register === | === The role of Risk Register === | ||
| − | In ''‘Practice Standard for Project Risk Management’'', the risk register is defined as the framework that is used in project risk management for the documentation of the identified risks. | + | In ''‘Practice Standard for Project Risk Management’'', the risk register is defined as the framework that is used in project risk management for the documentation of the identified risks. It records all the needed information that will be the steppingstone to overcome the risks that might menace projects' success. <ref name="Pmi" /> It is worth noting that based on ''‘PRINCE2’'', the risks are divided into threats and opportunities. Threats are the risks that could have negative consequences for the project, while opportunities could bring positive outcomes to the company. <ref name="PRINCE"> Project Management: "Managing Successful Projects with PRINCE2" 6th Edition (2017) Retrieved from: https://ebookcentral-proquest-com.proxy.findit.dtu.dk/lib/DTUDK/detail.action?docID=4863041</ref> The article is mainly focused on the documentation of the various threats in the risk register. The importance of the tool is highlighted in the fact that it can assist project managers with tackling potential threats and to have a better and clearer overview of the internal and external risks that might negatively affect the success of the project. <ref name="oo"> What Is a Risk Register in Project Management? Retrieved from: https://www.wrike.com/blog/what-is-a-risk-register-project-management/, Accessed on 20/02/2021 </ref> The aim of the risk register is to record information related to the identification, assessment, evaluation of importance, and managing of the potential risks. <ref name="Pmi" /> <ref name="PRINCE" /> More specifically, the uncertainty that exists in projects makes it necessary to use a model that provides various information for the events that could threaten the projects. <ref name="Pmi" /> |
| − | In the ''‘PMBOK guide ’ ''it is outlined that the tool risk register can be used in different phases of a project. Firstly, it can be used at a very early stage of a project in order to provide information for the risks that might be a threat. Secondly, as the project continues, new threats are recorded and documented in the risk register. In other words, it is used to update the new risks and inform the | + | In the ''‘PMBOK guide ’ ''it is outlined that the tool risk register can be used in different phases of a project. Firstly, it can be used at a very early stage of a project in order to provide information for the risks that might be a threat. Secondly, as the project continues, new threats are recorded and documented in the risk register. In other words, it is used to update the new risks and inform the risk owners how they should monitor the new threats. Finally, it documents all the risks that have been recorded after the completion of a project. <ref name="ot"> Project Management Institute, Project Management: A guide to the Project Management Body of Knowledge (PMBOK guide) 6th Edition (2017), Retrieved from:https://app-knovel-com.proxy.findit.dtu.dk/web/toc.v/cid:kpGPMBKP02/viewerType:toc/root_slug:viewerType%3Atoc/url_slug:root_slug%3Aguide-project-management?kpromoter=federation </ref> |
=== Elements of Risk Register=== | === Elements of Risk Register=== | ||
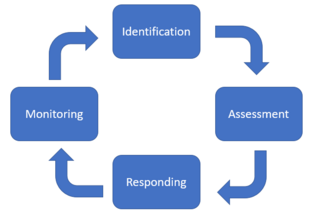
| − | As can be seen in figure 1, the implementation of the risk register model follows four processes. Firstly, the risks have to be identified. Secondly, they have to be assessed based on their impact and probability. After risk assessment, it is important to define the actions that must be taken, in order to manage the risks. The final process of the risk register model follows, deals with the ways the risks can be monitored. <ref name="Pmi" /> | + | As can be seen in figure 1, the implementation of the risk register model follows four processes. Firstly, the risks have to be identified. Secondly, they have to be assessed based on their impact and probability. After risk assessment, it is important to define the actions that must be taken, in order to manage the risks. The final process of the risk register model follows, deals with the ways the risks can be monitored. <ref name="Pmi" /> <ref name="ot" /> <ref name="PRINCE"/> The outcome of the previously mentioned processes is the input for the risk register framework. |
| − | [[File:Screenshot 2021-02-25 221935.png|center|thumb|310px|Figure 1: Implementation steps of Risk Register (own figure, based on <ref name="Pmi" /> and <ref name="PRINCE"/>) ]] | + | [[File:Screenshot 2021-02-25 221935.png|center|thumb|310px|Figure 1: Implementation steps of Risk Register (own figure, based on <ref name="Pmi" />,<ref name="ot" /> and <ref name="PRINCE"/>) ]] |
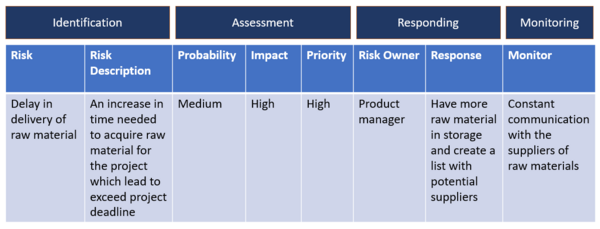
| − | Risk register has the form of a table where each column represents different characteristics of the potential risks.<ref name="latvia"> Project Risk Register Analysis Based on the Theoretical Analysis of Project Management Notion of Risk, Juris Uzulāns, University of Latvia, 2016 </ref> In order to start building the risk register the first step is the identification of the risks. Once the potential threats are known it is vital to provide a brief description for each one. <ref name="Pmi" /> This helps the project managers not only to clarify the risks but also to understand why they are threatening the project’s success. Secondly, for the assessment of the risks, their probability and impact on the project are examined. Furthermore, in'' ‘Practice Standard for Project Risk Management’'' it is stated that the evaluation of the risk is depending on their impact and their frequency to happen.<ref name="Pmi" /> For instance, the risks that have high impact and probability to occur, are risks with higher importance than the risks with low frequency and impact. The identification of the risks’ importance is an essential element for project managers to know which risks are needed more attention and time for setting up a plan in order to overcome them. <ref name="Pmi" /> Furthermore, based on the ''‘PMBOK guide’'' the risk register also includes information about the person who must tackle every risk and the actions that he has to take to eliminate its negative consequences. <ref name="ot" /> | + | Risk register has the form of a table where each column represents different characteristics of the potential risks.<ref name="latvia"> Project Risk Register Analysis Based on the Theoretical Analysis of Project Management Notion of Risk, Juris Uzulāns, University of Latvia, 2016 Retrieved from: https://doi.org/10.1515/eb-2016-0020 </ref> In order to start building the risk register the first step is the identification of the risks. Once the potential threats are known it is vital to provide a brief description for each one. <ref name="Pmi" /> This helps the project managers not only to clarify the risks but also to understand why they are threatening the project’s success. Secondly, for the assessment of the risks, their probability and impact on the project are examined. Furthermore, in'' ‘Practice Standard for Project Risk Management’'' it is stated that the evaluation of the risk is depending on their impact and their frequency to happen.<ref name="Pmi" /> For instance, the risks that have high impact and probability to occur, are risks with higher importance than the risks with low frequency and impact. The identification of the risks’ importance is an essential element for project managers to know which risks are needed more attention and time for setting up a plan in order to overcome them. <ref name="Pmi" /> Furthermore, based on the ''‘PMBOK guide’'' the risk register also includes information about the person who must tackle every risk and the actions that he has to take to eliminate its negative consequences. <ref name="ot" /> Finally, the risks should be monitored in order to prevent unexpected events. <ref name="Pmi" /> The above elements are demanding high attention as they are mainly focused on dominant areas of the risk management process which are the identification of the threats, the evaluation of their importance, the course of action that should be taken to respond and control them. Figure 2 illustrates the risk register table based on the discussion above. |
| − | + | ||
| − | ==How Risk | + | [[File:table1111.png|center|thumb|600px|Figure 2: Risk Register table (own figure, based on the discussion above)]] |
| + | |||
| + | ==How Risk Register is used ? == | ||
In order to have an in-depth understanding of the risk register, it is of utmost importance to analyse the way that it can be used. The tool aims to eliminate the negative impacts of the various threats by identifying, assessing, evaluating, and monitoring them. The following sections provide a guidance on how the four processes of risk register can be implemented. | In order to have an in-depth understanding of the risk register, it is of utmost importance to analyse the way that it can be used. The tool aims to eliminate the negative impacts of the various threats by identifying, assessing, evaluating, and monitoring them. The following sections provide a guidance on how the four processes of risk register can be implemented. | ||
| − | === 1. How to identify the risks | + | === 1. How to identify the risks === |
As a first step, the risks have to be identified by using the right techniques. Once this is complete, a short description of the risks that have been identified through the risk management process is provided. | As a first step, the risks have to be identified by using the right techniques. Once this is complete, a short description of the risks that have been identified through the risk management process is provided. | ||
''' 1.1 Risk identification ''' | ''' 1.1 Risk identification ''' | ||
| − | As it is quoted in ''‘Practice Standard for Project Risk Management’'', ''‘’ A risk cannot be managed unless it is first identified.’’'' <ref name="Pmi" /> The identified risks are the first information that will be used in the risk register. <ref name="Pmi" /> | + | As it is quoted in ''‘Practice Standard for Project Risk Management’'', ''‘’ A risk cannot be managed unless it is first identified.’’'' <ref name="Pmi" /> (p.25) The identified risks are the first information that will be used in the risk register. <ref name="Pmi" /> <ref name="ot" /> It is worth noting that the risk identification process is continuous because as time passes, the number of information increases. In other words, new risks will become knowable by repeating the risk identification process in different phases of a project. <ref name="Pmi" /> |
| − | In this article, three methods are used for the risk identification process and all of them are following the ''‘Practice Standard for Project Risk Management’'' <ref name="Pmi" />: | + | In this article, three methods are used for the risk identification process and all of them are following the ''‘Practice Standard for Project Risk Management’'' <ref name="Pmi" /> (p.28): |
| − | *'''''Historical review''''': This technique is used as an analysis of events that happened in the past. When this method | + | *'''''Historical review''''': This technique is used as an analysis of events that happened in the past. When this method is used it is vital to make sure that the events that are under observation are correlated with risks that happened before in this project or in different projects from the same or different company. This method demands attention as there is the risk to compare data and risks from projects that are not closely connected to the project. |
* '''''Current Assessment''''': In this method, the risk identification process is focused on analysing the project’s uncertainty based on the information that is known in this specific period of time. | * '''''Current Assessment''''': In this method, the risk identification process is focused on analysing the project’s uncertainty based on the information that is known in this specific period of time. | ||
*''''' Creativity Techniques''''': This approach is based on the creativity of the people who participate in the project. To be more specific, stakeholders have the chance to work individually or with other people in order to identify risks by using creative methods and thinking outside of the box. | *''''' Creativity Techniques''''': This approach is based on the creativity of the people who participate in the project. To be more specific, stakeholders have the chance to work individually or with other people in order to identify risks by using creative methods and thinking outside of the box. | ||
| − | All of the techniques mentioned above have both strong points and limitations. This means that if they are used separately, they might lead to inadequate results. Thus, the combination of the three techniques can guarantee more accurate results. <ref name="Pmi" /> | + | All of the techniques mentioned above have both strong points and limitations. This means that if they are used separately, they might lead to inadequate results. Thus, the combination of the three techniques can guarantee more accurate results. <ref name="Pmi" /> (p.28) |
''' 1.2 Risk description''' | ''' 1.2 Risk description''' | ||
| − | The description of the identified risks is a very important component of the risk identification process. It is a way to make sure that the risks are well communicated and understood among all the stakeholders. <ref name="ppp"> | + | The description of the identified risks is a very important component of the risk identification process. It is a way to make sure that the risks are well communicated and understood among all the stakeholders. <ref name="ppp"> Guide to Using a Risk Register, Stephanie Ray, https://www.projectmanager.com/blog/guide-using-risk-register Accessed on 19/02/2020 </ref> For instance, in a construction problem, it is identified that a potential risk could be a shock in the economy. A potential explanation is that a shock in the economy could increase the price of raw materials and as a result the project might exceed the agreed budget. As it could be observed, the description of this risk could give a better insight into what this change might impact. |
=== 2. How to assess the risks === | === 2. How to assess the risks === | ||
The assessment of the various risks could be applied by using two methods, namely, the qualitative and quantitative risk analysis. Both methods are used to evaluate risks’ importance to the project. This includes an analysis of the probability that each risk has to occur and the impact that they might have on the project. <ref name="Pmi" /> In this article, the assessment of the identified risks is following the ''‘’ Practice Standard for Project Risk Management‘’ '' and the''‘’ PMBOK guide ‘’ ''. | The assessment of the various risks could be applied by using two methods, namely, the qualitative and quantitative risk analysis. Both methods are used to evaluate risks’ importance to the project. This includes an analysis of the probability that each risk has to occur and the impact that they might have on the project. <ref name="Pmi" /> In this article, the assessment of the identified risks is following the ''‘’ Practice Standard for Project Risk Management‘’ '' and the''‘’ PMBOK guide ‘’ ''. | ||
| − | * '''Qualitative risk analysis''' | + | * '''Qualitative risk analysis''' <ref name="Pmi" /> <ref name="ot" /> |
| − | In qualitative risk analysis, the risks are evaluated and ranked based on their probability, impact, and some other characteristics that have been defined before the implementation of the analysis. This analysis is implemented regularly as new threats might need to be identified. | + | In qualitative risk analysis, the risks are evaluated and ranked based on their probability, impact, and some other characteristics that have been defined before the implementation of the analysis. This analysis is implemented regularly as new threats might need to be identified. The basic components of qualitative risk analysis are the high or low probability of a risk to happen and the consequences that it might have in ''‘’ one or more project objectives such as schedule, cost, quality, or performance.’’'' <ref name="ot" /> (p.423) Additionally, in qualitative risk analysis the risks can be grouped based on various criteria. For example, they can be grouped by risks that might exceed projects’ deadlines. This way, the project management team could monitor the risks in a more effective way since not only they will know the project areas they need to pay more attention to, but they will also have a quicker response managing the threats of the several categories. |
| − | * '''Quantitative risk analysis''' | + | * '''Quantitative risk analysis''' <ref name="Pmi" /> <ref name="ot" /> |
| − | The quantitative risk analysis is used to calculate risks’ effects on the project. While this numerical analysis is not considered vital for all the projects, it provides more pragmatistic results. The implementation of the quantitative risk analysis follows on from the qualitative risk analysis. This could be explained by the fact that in the qualitative risk analysis the risks are already prioritized and thus the most vital threats are recognized and could be calculated. The impact and the probability are calculated, and the risk register table can be updated with numerical results. | + | The quantitative risk analysis is used to calculate risks’ effects on the project. While this numerical analysis is not considered vital for all the projects, it provides more pragmatistic results. The implementation of the quantitative risk analysis follows on from the qualitative risk analysis. This could be explained by the fact that in the qualitative risk analysis the risks are already prioritized and thus the most vital threats are recognized and could be calculated. The impact and the probability are calculated, and the risk register table can be updated with numerical results. |
=== 3. How to respond to the risks === | === 3. How to respond to the risks === | ||
| − | It is of utmost importance to tackle the identified risks once they have been assessed. In order to do so, it is necessary to perform a risk management plan which will include the actions for dealing with the risks and the person who is responsible to tackle them. As a first step the risks should be | + | It is of utmost importance to tackle the identified risks once they have been assessed. In order to do so, it is necessary to perform a risk management plan which will include the actions for dealing with the risks and the person who is responsible to tackle them. As a first step the risks should be known by all the stakeholders. Every potential risk is assigned to the right people. These people are called risk owners and they are responsible with controlling and finding solutions for the risks they are assigned with. The risks could harm the project in various ways and for this reason, there should be a plan with responses for all of them.<ref name="Pmi" /> <ref name="ot" /> In the ''‘Practice Standard for Project Risk Management’'' it is written that ''’’ the planning entails agreeing upon the actions to be taken and the potential changes to the budget, schedule, resources, and scope which these actions might cause.’’'' <ref name="Pmi" /> (p.43) Furthermore, the actions that have to be taken for every risk should be developed at the very early stage of its identification. In other words, it is integral to have the strategies and responses in advance so that project’s time schedule will change as little as possible. <ref name="Pmi" /> The risk register includes all the responses and actions on its table. Once new risks are identified risk register is updated with new strategies that the risk owner has to follow. Moreover, throughout the lifecycle of a project, it is possible to make adjustments and corrections to the plans of the previously identified risks. <ref name="ppp" /> |
| − | === 4. How to monitor the risks | + | === 4. How to monitor the risks === |
| − | Risk monitoring is the last process that needs to be implemented in order to fill in the risk register table. This final step is as important as the three steps mentioned above. Risk should be monitored throughout the life cycle of a project. It is a continuous process that includes the actions that have to be taken in order to control not only the risks that already have been identified but also the new threats that have to be tamed. <ref name="Pmi" />. <ref name="ot" /> Additionally, risk monitoring is used to certify that all the risk responses are taken place when there is a need for action. This is a way to appraise the effectiveness of the responses and the risk owner in the risk management process. <ref name="Pmi" /> The process starts by checking the risk register table. The table should include the appropriate responses for every risk, otherwise, it has to be updated with the new actions that have to be taken.<ref name="Pmi" /> Moreover, it is important for the new actions and changes to be well communicated to the stakeholders and to the people responsible for that specific risks. | + | Risk monitoring is the last process that needs to be implemented in order to fill in the risk register table. This final step is as important as the three steps mentioned above. Risk should be monitored throughout the life cycle of a project. It is a continuous process that includes the actions that have to be taken in order to control not only the risks that already have been identified but also the new threats that have to be tamed. <ref name="Pmi" />. <ref name="ot" /> Additionally, risk monitoring is used to certify that all the risk responses are taken place when there is a need for action. This is a way to appraise the effectiveness of the responses and the risk owner in the risk management process. <ref name="Pmi" /> The process starts by checking the risk register table. The table should include the appropriate responses for every risk, otherwise, it has to be updated with the new actions that have to be taken.<ref name="Pmi" /> Moreover, it is important for the new actions and changes to be well communicated to the stakeholders and to the people responsible for that specific risks. The number of information varies at the different stages of a project. More information is available to the project managers as the project continues its processes, which means that changes can be made in the risk register. These changes will be defined during the monitoring process and will be updated and documented in the risk register by providing new information for the actions that have to be changed. <ref name="Pmi" /> |
| − | In this article, three techniques are analyzed for controlling the risks. These techniques are analyzed in the ''‘PMBOK guide ’'' <ref name="ot" /> : | + | In this article, three techniques are analyzed for controlling the risks. These techniques are analyzed in the ''‘PMBOK guide ’'' <ref name="ot" /> (p.456-457) : |
* '''Data analysis''': This technique is used to ensure that the reserves of the project are enough to not threaten its budget and the deadlines. <ref name="ot" /> More specifically, this analysis is checking if the reserves that a project has as a backup is enough to ensure that it will have the resources to manage an unexpected event that will make its budget and time exceed the agreed limits. <ref name="Pmi" /> | * '''Data analysis''': This technique is used to ensure that the reserves of the project are enough to not threaten its budget and the deadlines. <ref name="ot" /> More specifically, this analysis is checking if the reserves that a project has as a backup is enough to ensure that it will have the resources to manage an unexpected event that will make its budget and time exceed the agreed limits. <ref name="Pmi" /> | ||
| − | * '''Audits''': This method applied in order to evaluate the performance of the processes included in the risk management and hence they are recorded in the risk register. | + | * '''Audits''': This method applied in order to evaluate the performance of the processes included in the risk management and hence they are recorded in the risk register. It is worth noting that this way of monitoring risks can be conducted during project meetings when the project team examines the risks. <ref name="ot" /> |
* '''Meetings''': During meetings, the project management team can evaluate the various risks. This is a vital process that examines the overall process of risk management planning. More specifically, the meeting can ensure that all the stakeholders have a clear overview of the risks that need to be tackled. Furthermore, it is possible that some of the identified risks happened in the past, and through the meeting, the project management team can communicate the learning outcomes and mistakes that they should avoid in the future. <ref name="ot" /> | * '''Meetings''': During meetings, the project management team can evaluate the various risks. This is a vital process that examines the overall process of risk management planning. More specifically, the meeting can ensure that all the stakeholders have a clear overview of the risks that need to be tackled. Furthermore, it is possible that some of the identified risks happened in the past, and through the meeting, the project management team can communicate the learning outcomes and mistakes that they should avoid in the future. <ref name="ot" /> | ||
| Line 72: | Line 74: | ||
==Reflections== | ==Reflections== | ||
| − | In this section, the advantages and | + | While many positive outcomes can arise from the use of the risk register framework, there are also some limitations that are worth mentioning. In this section, the advantages and limitations of the risk register framework are discussed. |
| − | === | + | === Advantages === |
| − | + | The risk register is used to document information about the various risks that have been identified not only at the very early stages but also throughout the whole lifecycle of the project. This is an extremely beneficial characteristic of the tool that can be used for the assessment of a project's performance as well as for the strategic and decision-making processes that are related to risk management. <ref name="sag"> Risk register developement and implementation for construction projects, Ivana Burcar Dunović, Mladen Radujković, Mladen Vukomanović, 2013 </ref> More specifically, as the project is developing, the amount of gathered information is growing which means that new risks will be identified to threaten the project's success. The risk register table is storing the information from the risks that already have been identified and evaluated, and once new treats have been found, the table is expanded with the new data. <ref name="sag"> Risk register developement and implementation for construction projects, Ivana Burcar Dunović, Mladen Radujković, Mladen Vukomanović, 2013 </ref> <ref name="Pmi" /> This could be vital for the overall success of the project since the new risk could be well communicated among the stakeholders and thus they will be informed for the new actions they have to take in order to eliminate the negative impact of the threats. Additionally, the table includes information that is the output of the qualitative risk analysis. <ref name="Pmi" /> <ref name="ot"> Project Management Institute, Project Management: A guide to the Project Management Body of Knowledge (PMBOK guide) 6th Edition (2017), Retrieved from:https://app-knovel-com.proxy.findit.dtu.dk/web/toc.v/cid:kpGPMBKP02/viewerType:toc/root_slug:viewerType%3Atoc/url_slug:root_slug%3Aguide-project-management?kpromoter=federation </ref> In other words, in the qualitative analysis, it is examined how possible is for a risk to take place and the impact that it will have on the project. This analysis is used to prioritize the risks based on their importance. <ref name="sag"> Risk register developement and implementation for construction projects, Ivana Burcar Dunović, Mladen Radujković, Mladen Vukomanović, 2013 </ref> <ref name="Pmi" /> Once the risks are ranked, the stakeholders are informed of the threats that they have to pay more attention to. This means that they might have to spend more time planning a strategy around these risks as they will have a higher impact. Finally, the risk register is an advantageous tool for complex projects. When a project is very complex, it's important to use tools that could break down the planning processes. Risk register, due to its structure, provides the needed information for every risk from the moment it is identified. <ref name="oo"> What Is a Risk Register in Project Management? Retrieved from: https://www.wrike.com/blog/what-is-a-risk-register-project-management/, Accessed on 20/02/2021 </ref> | |
=== Limitations === | === Limitations === | ||
| − | + | The identified risks are listed based on the critical way of thinking of the people who are associated with the risk evaluation. This could be a limitation since the results on the risk register table might reflect the personal opinion of the people who implemented it and not the reality.<ref name="ot"> Project Management Institute, Project Management: A guide to the Project Management Body of Knowledge (PMBOK guide) 6th Edition (2017), Retrieved from:https://app-knovel-com.proxy.findit.dtu.dk/web/toc.v/cid:kpGPMBKP02/viewerType:toc/root_slug:viewerType%3Atoc/url_slug:root_slug%3Aguide-project-management?kpromoter=federation </ref> <ref name="fd"> Why risk registers don't do enough to help you manage risks, https://www.civilsociety.co.uk/finance/why-risk-registers-don-t-do-enough-to-help-you-manage-risks.html, Accessed on 22/02/2020 </ref> Moreover, the development of the risk register table requires a lot of time in order to insert the data from the four processes. Apart from that since the table is updated when changes are made either to the list of the identified risks or to the actions that have to be taken, it is possible that mistakes might occur when the new data are imported. Hence, the implementation of the documented results of the risk register seeks attention in order to avoid mistakes. However, the risk register is more than important when it comes to analysing the risks. <ref name="sag"> Risk register developement and implementation for construction projects, Ivana Burcar Dunović, Mladen Radujković, Mladen Vukomanović, 2013 </ref> This means that even though it is a time-consuming process, the outcomes of the tool can prevent threats that otherwise could have a negative impact on the project. | |
| − | + | ||
| − | + | It is worth noting, that ignoring the limitations of the risk management tool could have a negative impact on the project. Nevertheless, it is a very important tool that should be applied in the risk management processes most or all of the time. | |
| − | * '' | + | ==Annotated bibliography== |
| + | * '' "Practice standard for project risk management." Project Management Institute, 2009.'' | ||
| + | This book is based on the PMBOK Guide– Fourth Edition. It is a book about the risk management processes that a project has to follow. It analyses the techniques for the identification, assessment, responding, and controlling of the risks. In this book, the reader can find information for the risk register model and how it is involved in all the previously mentioned processes. Although the book provides many details on how to manage risks, it does not illustrate the risk register table. For this reason, the visualization of the table in this article is based on the theoretical outcomes of the book and not on the graphical illustrations included in it. | ||
| − | * | + | * ''Project Management: "Managing Successful Projects with PRINCE2" 6th Edition (2017)'' |
| + | This book is focused on how to manage projects based on PRINCE2 principles. It describes the activities that a project needs based on its implementation stage. Risks analysis is also explained in one of the chapters of the book. In this book, the various stages of the risk management process are explained by providing the needing theory and figures. For example, the article's figure 1 is inspired by one of the illustrations of the book. However, the risk register model is also not illustrated in one of the pages of the book and that could be considered as a negative point. | ||
| − | * | + | * ''Project Management: A guide to the Project Management Body of Knowledge (PMBOK guide) 6th Edition (2017)'' |
| + | The book A guide to the Project Management Body of Knowledge provides detailed information on how to manage projects. The risk register framework is analyzed in the chapters of the book by providing information on the usage of the tool in the various processes of risk management. This book is a very useful guide for project management planning. It provides many details for the implementation and organization of projects. | ||
==References== | ==References== | ||
<references/> | <references/> | ||
Latest revision as of 21:51, 28 February 2021
Developed by Dorothea Georgiadou
In an age where the economic, social, and political environment is constantly shifting, there is an urgent need to study the risks that may threaten the success of a project. It is particularly important to study the risks that may adversely affect the project and lead to events that might have as a consequence the exceeding of the agreed budget and time. For this reason, the risk management planning should identify and describe in detail the potential risks by providing the needed information for the actions that should be done for eliminating their negative impact. The high uncertainty that exists in projects necessitates the use of a management tool that will control the risks. [1] In this article the risk management framework ‘’Risk register’’ is explained. The risk register is a tool that covers and studies many aspects of risk management processes. More specifically, the aim of this article is to explain how this tool can be used to document the outcomes of the risk management processes. [2] The article provides a description of the tool along with the reasons that it should be used. It is a framework that aims to record the information from the processes related to the identification, assessment, responding, and monitoring of potential risks. [2]. Finally, the article analyzes along with the benefits also the limitations of this risk management tool.
Contents |
[edit] Why use Risk Register?
In an ever-changing environment, a projects’ success is associated with a high level of uncertainty. In the ‘Practice Standard for Project Risk Management’, risk management is an approach that plays a vital role in the strategic and decision-making processes since adjustments in the project management planning can be done after the identification of the projects’ challenges. The risk register framework is used to support the risk management process in order to eliminate the negative impact that the various threats might have on a project. Threats could come from the external and internal environment of the company. The external risks are associated with the economic, social, political, and technological environment, while the internal threats include risks that are related to human actions and estimations. [1] [2]. For example, it is possible for people to make wrong estimations because of inexperience and underestimation of some threats. This high level of uncertainty makes it increasingly necessary to use a model that assists the risk management process in a more effective way. [1] [2].
[edit] The role of Risk Register
In ‘Practice Standard for Project Risk Management’, the risk register is defined as the framework that is used in project risk management for the documentation of the identified risks. It records all the needed information that will be the steppingstone to overcome the risks that might menace projects' success. [1] It is worth noting that based on ‘PRINCE2’, the risks are divided into threats and opportunities. Threats are the risks that could have negative consequences for the project, while opportunities could bring positive outcomes to the company. [3] The article is mainly focused on the documentation of the various threats in the risk register. The importance of the tool is highlighted in the fact that it can assist project managers with tackling potential threats and to have a better and clearer overview of the internal and external risks that might negatively affect the success of the project. [4] The aim of the risk register is to record information related to the identification, assessment, evaluation of importance, and managing of the potential risks. [1] [3] More specifically, the uncertainty that exists in projects makes it necessary to use a model that provides various information for the events that could threaten the projects. [1]
In the ‘PMBOK guide ’ it is outlined that the tool risk register can be used in different phases of a project. Firstly, it can be used at a very early stage of a project in order to provide information for the risks that might be a threat. Secondly, as the project continues, new threats are recorded and documented in the risk register. In other words, it is used to update the new risks and inform the risk owners how they should monitor the new threats. Finally, it documents all the risks that have been recorded after the completion of a project. [5]
[edit] Elements of Risk Register
As can be seen in figure 1, the implementation of the risk register model follows four processes. Firstly, the risks have to be identified. Secondly, they have to be assessed based on their impact and probability. After risk assessment, it is important to define the actions that must be taken, in order to manage the risks. The final process of the risk register model follows, deals with the ways the risks can be monitored. [1] [5] [3] The outcome of the previously mentioned processes is the input for the risk register framework.
Risk register has the form of a table where each column represents different characteristics of the potential risks.[6] In order to start building the risk register the first step is the identification of the risks. Once the potential threats are known it is vital to provide a brief description for each one. [1] This helps the project managers not only to clarify the risks but also to understand why they are threatening the project’s success. Secondly, for the assessment of the risks, their probability and impact on the project are examined. Furthermore, in ‘Practice Standard for Project Risk Management’ it is stated that the evaluation of the risk is depending on their impact and their frequency to happen.[1] For instance, the risks that have high impact and probability to occur, are risks with higher importance than the risks with low frequency and impact. The identification of the risks’ importance is an essential element for project managers to know which risks are needed more attention and time for setting up a plan in order to overcome them. [1] Furthermore, based on the ‘PMBOK guide’ the risk register also includes information about the person who must tackle every risk and the actions that he has to take to eliminate its negative consequences. [5] Finally, the risks should be monitored in order to prevent unexpected events. [1] The above elements are demanding high attention as they are mainly focused on dominant areas of the risk management process which are the identification of the threats, the evaluation of their importance, the course of action that should be taken to respond and control them. Figure 2 illustrates the risk register table based on the discussion above.
[edit] How Risk Register is used ?
In order to have an in-depth understanding of the risk register, it is of utmost importance to analyse the way that it can be used. The tool aims to eliminate the negative impacts of the various threats by identifying, assessing, evaluating, and monitoring them. The following sections provide a guidance on how the four processes of risk register can be implemented.
[edit] 1. How to identify the risks
As a first step, the risks have to be identified by using the right techniques. Once this is complete, a short description of the risks that have been identified through the risk management process is provided.
1.1 Risk identification
As it is quoted in ‘Practice Standard for Project Risk Management’, ‘’ A risk cannot be managed unless it is first identified.’’ [1] (p.25) The identified risks are the first information that will be used in the risk register. [1] [5] It is worth noting that the risk identification process is continuous because as time passes, the number of information increases. In other words, new risks will become knowable by repeating the risk identification process in different phases of a project. [1]
In this article, three methods are used for the risk identification process and all of them are following the ‘Practice Standard for Project Risk Management’ [1] (p.28):
- Historical review: This technique is used as an analysis of events that happened in the past. When this method is used it is vital to make sure that the events that are under observation are correlated with risks that happened before in this project or in different projects from the same or different company. This method demands attention as there is the risk to compare data and risks from projects that are not closely connected to the project.
- Current Assessment: In this method, the risk identification process is focused on analysing the project’s uncertainty based on the information that is known in this specific period of time.
- Creativity Techniques: This approach is based on the creativity of the people who participate in the project. To be more specific, stakeholders have the chance to work individually or with other people in order to identify risks by using creative methods and thinking outside of the box.
All of the techniques mentioned above have both strong points and limitations. This means that if they are used separately, they might lead to inadequate results. Thus, the combination of the three techniques can guarantee more accurate results. [1] (p.28)
1.2 Risk description
The description of the identified risks is a very important component of the risk identification process. It is a way to make sure that the risks are well communicated and understood among all the stakeholders. [7] For instance, in a construction problem, it is identified that a potential risk could be a shock in the economy. A potential explanation is that a shock in the economy could increase the price of raw materials and as a result the project might exceed the agreed budget. As it could be observed, the description of this risk could give a better insight into what this change might impact.
[edit] 2. How to assess the risks
The assessment of the various risks could be applied by using two methods, namely, the qualitative and quantitative risk analysis. Both methods are used to evaluate risks’ importance to the project. This includes an analysis of the probability that each risk has to occur and the impact that they might have on the project. [1] In this article, the assessment of the identified risks is following the ‘’ Practice Standard for Project Risk Management‘’ and the‘’ PMBOK guide ‘’ .
In qualitative risk analysis, the risks are evaluated and ranked based on their probability, impact, and some other characteristics that have been defined before the implementation of the analysis. This analysis is implemented regularly as new threats might need to be identified. The basic components of qualitative risk analysis are the high or low probability of a risk to happen and the consequences that it might have in ‘’ one or more project objectives such as schedule, cost, quality, or performance.’’ [5] (p.423) Additionally, in qualitative risk analysis the risks can be grouped based on various criteria. For example, they can be grouped by risks that might exceed projects’ deadlines. This way, the project management team could monitor the risks in a more effective way since not only they will know the project areas they need to pay more attention to, but they will also have a quicker response managing the threats of the several categories.
The quantitative risk analysis is used to calculate risks’ effects on the project. While this numerical analysis is not considered vital for all the projects, it provides more pragmatistic results. The implementation of the quantitative risk analysis follows on from the qualitative risk analysis. This could be explained by the fact that in the qualitative risk analysis the risks are already prioritized and thus the most vital threats are recognized and could be calculated. The impact and the probability are calculated, and the risk register table can be updated with numerical results.
[edit] 3. How to respond to the risks
It is of utmost importance to tackle the identified risks once they have been assessed. In order to do so, it is necessary to perform a risk management plan which will include the actions for dealing with the risks and the person who is responsible to tackle them. As a first step the risks should be known by all the stakeholders. Every potential risk is assigned to the right people. These people are called risk owners and they are responsible with controlling and finding solutions for the risks they are assigned with. The risks could harm the project in various ways and for this reason, there should be a plan with responses for all of them.[1] [5] In the ‘Practice Standard for Project Risk Management’ it is written that ’’ the planning entails agreeing upon the actions to be taken and the potential changes to the budget, schedule, resources, and scope which these actions might cause.’’ [1] (p.43) Furthermore, the actions that have to be taken for every risk should be developed at the very early stage of its identification. In other words, it is integral to have the strategies and responses in advance so that project’s time schedule will change as little as possible. [1] The risk register includes all the responses and actions on its table. Once new risks are identified risk register is updated with new strategies that the risk owner has to follow. Moreover, throughout the lifecycle of a project, it is possible to make adjustments and corrections to the plans of the previously identified risks. [7]
[edit] 4. How to monitor the risks
Risk monitoring is the last process that needs to be implemented in order to fill in the risk register table. This final step is as important as the three steps mentioned above. Risk should be monitored throughout the life cycle of a project. It is a continuous process that includes the actions that have to be taken in order to control not only the risks that already have been identified but also the new threats that have to be tamed. [1]. [5] Additionally, risk monitoring is used to certify that all the risk responses are taken place when there is a need for action. This is a way to appraise the effectiveness of the responses and the risk owner in the risk management process. [1] The process starts by checking the risk register table. The table should include the appropriate responses for every risk, otherwise, it has to be updated with the new actions that have to be taken.[1] Moreover, it is important for the new actions and changes to be well communicated to the stakeholders and to the people responsible for that specific risks. The number of information varies at the different stages of a project. More information is available to the project managers as the project continues its processes, which means that changes can be made in the risk register. These changes will be defined during the monitoring process and will be updated and documented in the risk register by providing new information for the actions that have to be changed. [1]
In this article, three techniques are analyzed for controlling the risks. These techniques are analyzed in the ‘PMBOK guide ’ [5] (p.456-457) :
- Data analysis: This technique is used to ensure that the reserves of the project are enough to not threaten its budget and the deadlines. [5] More specifically, this analysis is checking if the reserves that a project has as a backup is enough to ensure that it will have the resources to manage an unexpected event that will make its budget and time exceed the agreed limits. [1]
- Audits: This method applied in order to evaluate the performance of the processes included in the risk management and hence they are recorded in the risk register. It is worth noting that this way of monitoring risks can be conducted during project meetings when the project team examines the risks. [5]
- Meetings: During meetings, the project management team can evaluate the various risks. This is a vital process that examines the overall process of risk management planning. More specifically, the meeting can ensure that all the stakeholders have a clear overview of the risks that need to be tackled. Furthermore, it is possible that some of the identified risks happened in the past, and through the meeting, the project management team can communicate the learning outcomes and mistakes that they should avoid in the future. [5]
After these processes, the risk register framework is updated with the new data in order to assist the project management team with the risk management process.
[edit] Reflections
While many positive outcomes can arise from the use of the risk register framework, there are also some limitations that are worth mentioning. In this section, the advantages and limitations of the risk register framework are discussed.
[edit] Advantages
The risk register is used to document information about the various risks that have been identified not only at the very early stages but also throughout the whole lifecycle of the project. This is an extremely beneficial characteristic of the tool that can be used for the assessment of a project's performance as well as for the strategic and decision-making processes that are related to risk management. [2] More specifically, as the project is developing, the amount of gathered information is growing which means that new risks will be identified to threaten the project's success. The risk register table is storing the information from the risks that already have been identified and evaluated, and once new treats have been found, the table is expanded with the new data. [2] [1] This could be vital for the overall success of the project since the new risk could be well communicated among the stakeholders and thus they will be informed for the new actions they have to take in order to eliminate the negative impact of the threats. Additionally, the table includes information that is the output of the qualitative risk analysis. [1] [5] In other words, in the qualitative analysis, it is examined how possible is for a risk to take place and the impact that it will have on the project. This analysis is used to prioritize the risks based on their importance. [2] [1] Once the risks are ranked, the stakeholders are informed of the threats that they have to pay more attention to. This means that they might have to spend more time planning a strategy around these risks as they will have a higher impact. Finally, the risk register is an advantageous tool for complex projects. When a project is very complex, it's important to use tools that could break down the planning processes. Risk register, due to its structure, provides the needed information for every risk from the moment it is identified. [4]
[edit] Limitations
The identified risks are listed based on the critical way of thinking of the people who are associated with the risk evaluation. This could be a limitation since the results on the risk register table might reflect the personal opinion of the people who implemented it and not the reality.[5] [8] Moreover, the development of the risk register table requires a lot of time in order to insert the data from the four processes. Apart from that since the table is updated when changes are made either to the list of the identified risks or to the actions that have to be taken, it is possible that mistakes might occur when the new data are imported. Hence, the implementation of the documented results of the risk register seeks attention in order to avoid mistakes. However, the risk register is more than important when it comes to analysing the risks. [2] This means that even though it is a time-consuming process, the outcomes of the tool can prevent threats that otherwise could have a negative impact on the project.
It is worth noting, that ignoring the limitations of the risk management tool could have a negative impact on the project. Nevertheless, it is a very important tool that should be applied in the risk management processes most or all of the time.
[edit] Annotated bibliography
- "Practice standard for project risk management." Project Management Institute, 2009.
This book is based on the PMBOK Guide– Fourth Edition. It is a book about the risk management processes that a project has to follow. It analyses the techniques for the identification, assessment, responding, and controlling of the risks. In this book, the reader can find information for the risk register model and how it is involved in all the previously mentioned processes. Although the book provides many details on how to manage risks, it does not illustrate the risk register table. For this reason, the visualization of the table in this article is based on the theoretical outcomes of the book and not on the graphical illustrations included in it.
- Project Management: "Managing Successful Projects with PRINCE2" 6th Edition (2017)
This book is focused on how to manage projects based on PRINCE2 principles. It describes the activities that a project needs based on its implementation stage. Risks analysis is also explained in one of the chapters of the book. In this book, the various stages of the risk management process are explained by providing the needing theory and figures. For example, the article's figure 1 is inspired by one of the illustrations of the book. However, the risk register model is also not illustrated in one of the pages of the book and that could be considered as a negative point.
- Project Management: A guide to the Project Management Body of Knowledge (PMBOK guide) 6th Edition (2017)
The book A guide to the Project Management Body of Knowledge provides detailed information on how to manage projects. The risk register framework is analyzed in the chapters of the book by providing information on the usage of the tool in the various processes of risk management. This book is a very useful guide for project management planning. It provides many details for the implementation and organization of projects.
[edit] References
- ↑ 1.00 1.01 1.02 1.03 1.04 1.05 1.06 1.07 1.08 1.09 1.10 1.11 1.12 1.13 1.14 1.15 1.16 1.17 1.18 1.19 1.20 1.21 1.22 1.23 1.24 1.25 1.26 1.27 1.28 1.29 1.30 Project Mangement Institute. "Practice standard for project risk management." Project Management Institute, 2009.
- ↑ 2.0 2.1 2.2 2.3 2.4 2.5 2.6 2.7 Risk register developement and implementation for construction projects, Ivana Burcar Dunović, Mladen Radujković, Mladen Vukomanović, 2013, Retrieved from: https://doi.org/10.14256/JCE.722.2012
- ↑ 3.0 3.1 3.2 3.3 Project Management: "Managing Successful Projects with PRINCE2" 6th Edition (2017) Retrieved from: https://ebookcentral-proquest-com.proxy.findit.dtu.dk/lib/DTUDK/detail.action?docID=4863041
- ↑ 4.0 4.1 What Is a Risk Register in Project Management? Retrieved from: https://www.wrike.com/blog/what-is-a-risk-register-project-management/, Accessed on 20/02/2021
- ↑ 5.00 5.01 5.02 5.03 5.04 5.05 5.06 5.07 5.08 5.09 5.10 5.11 5.12 5.13 5.14 5.15 Project Management Institute, Project Management: A guide to the Project Management Body of Knowledge (PMBOK guide) 6th Edition (2017), Retrieved from:https://app-knovel-com.proxy.findit.dtu.dk/web/toc.v/cid:kpGPMBKP02/viewerType:toc/root_slug:viewerType%3Atoc/url_slug:root_slug%3Aguide-project-management?kpromoter=federation
- ↑ Project Risk Register Analysis Based on the Theoretical Analysis of Project Management Notion of Risk, Juris Uzulāns, University of Latvia, 2016 Retrieved from: https://doi.org/10.1515/eb-2016-0020
- ↑ 7.0 7.1 Guide to Using a Risk Register, Stephanie Ray, https://www.projectmanager.com/blog/guide-using-risk-register Accessed on 19/02/2020
- ↑ Why risk registers don't do enough to help you manage risks, https://www.civilsociety.co.uk/finance/why-risk-registers-don-t-do-enough-to-help-you-manage-risks.html, Accessed on 22/02/2020