Decision tree
(→Limitations and Barriers) |
|||
| Line 148: | Line 148: | ||
==Benefits and Possibilites== | ==Benefits and Possibilites== | ||
==Limitations and Barriers== | ==Limitations and Barriers== | ||
| + | |||
| + | Some risks can not be used in the decision tree because they would cause too severe consequences and will have to be avoided or externalized. | ||
| + | |||
| + | The probabilities of risks happening can only be estimated to a certain degree of actuality. | ||
| + | |||
==Conclusion== | ==Conclusion== | ||
==Annotated Bibliography== | ==Annotated Bibliography== | ||
Revision as of 16:22, 1 October 2017
Abstract
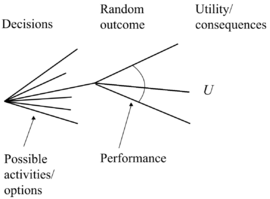
Decision Tree as a tool in Risk Management. [2]
When the risks have been identified and the respective impacts and probabilities have been investigated, the decision whether to insure, mitigate, accept or externalise the risk in question will result in different possible outcomes with different probabilities and consequences. From these different branches other risk decisions will be made, and in the end a decision tree with all the possible different paths to what risks will be managed and how, will be established.
This wiki article investigates how the decision tree works as a tool in risk management, what the benefits are and what barriers are related to this tool.
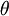 θ
θ
1. The Decision Tree Concept
2. Applying the Decision Tree to Project Management
3. Other Risk Management Tools Involved
4. Benefits and Possibilites
5. Limitations and Barriers
6. Conclusion
7. References
8. Annotated Bibliography
Writer: Frederik Lind, s133570
Contents |
Initial Steps to Decision Making
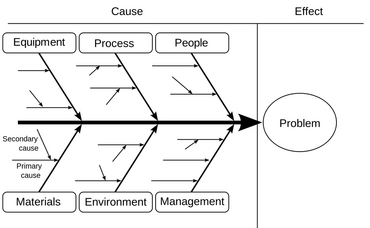
Risk Identification
The identification of risks is a process that must begin early in the project during the planning phase and it must be done thoroughly to mitigate potential delays, change of scope, budget overruns and quality loss.[4]
While the definition of the term risk involves only the possibility of experiencing unfavorable events, risk identification within the project context however both includes the opportunities (positive outcomes) and the threats (negative outcomes).[5]
It is practically impossible to identify all risks before they occur, however it is possible to map an extensive majority through a combination of a number of identification methods.
A common first step to identifying risks is to organize the possible risks in branches of causes, Figure 1.
A list of risks can be gathered through brainstorming in collaboration with the project team, experts and stakeholders by focusing on what possible events and their sources within each branch that will affect changes in scope, cost, time and quality of the outcome of the project.[3]
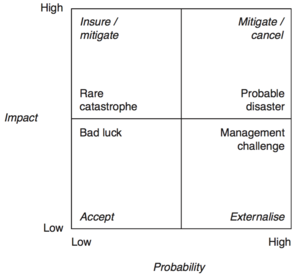
Risk Assessment
The next step is to assess the potential risks where the goal is to define the consequence and likelihood ranges for each risk source in collaboration with the stakeholders. A tool to visually map the respective probabilities and impacts for each risk and to get an immediate overview of desired response approach is to apply the Probability/Impact Matrix, Figure 2.[2]
The impact of a threat or opportunity occurring will always be associated with a direct or an indirect increase or decrease in cost for the project. The cost related to each consequence must be estimated and registered.
When the probabilities and levels of impact have been evaluated, the planning team should be divided into different field-specific sub-groups to which the respective related risks should be assigned for possible response investigation.[7]
Risk Response Analysis
The assigned sub-groups will then identify any possible actions to prevent risks and to enhance opportunities.[7]
Different response options are often available for each risk source, and the angle of attack to construct the final list of approaches for all risks can be inspired by the Probability/Impact Matrix, Figure 2. The response approach consists generally of four pillars: accept, externalise, mitigate and insurance against the risk. A fifth immediate option is to delay the response decision until more information is available.[6]
- Accept the risk. If the risk is accepted a response to the risk event occurring should be planned.
- Externalise the risk. When contracting out the source of the risk down the supply chain of the project structure, the sub-contractor in charge must be in a better position to handle the risk. The secondary risk associated with this response is that the sub-contractor will fail the commitments and either go bankrupt, hand the risk back to the principal or withdraw from the project.
- Mitigate the risk. This response underlines the necessity to risk manage very early in the project and is the main reason behind risk management. By mitigating or avoiding risks, the probabilities of risks are minimized leading to reduced delays, change orders and budget overruns. Mitigating and avoiding a threat can be done in a various number of ways and determining the possibilities to mitigate/avoid the risks or enhance/create opportunities is the main key to benefit from the decision tree.
- Insure against the risk. This response is not always possible but for uncontrollable rare catastrophes insurance is usually possible, such as fire.
- Delay the response. By delaying the response decision until more information is available, it is sometimes possible to make more efficient and tailored risk responses. This approach is often used for unknown risks where a frame for handling the risk event is the only option.
[6]
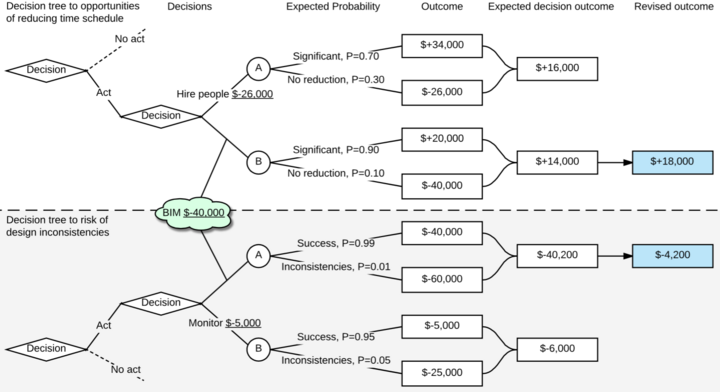
To fully exploit the opportunities related to using the decision tree, the different response angles for all estimated risks should be investigated and listed. Furthermore every preventive or enhancing action or lack hereof is associated with a direct cost which is important to determine to make a thorough scientific base for the decision tree.
Decision Tree - Treating Risks
The Concept
yes yes this is math 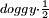

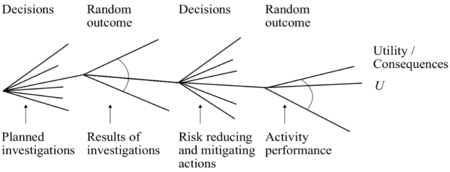
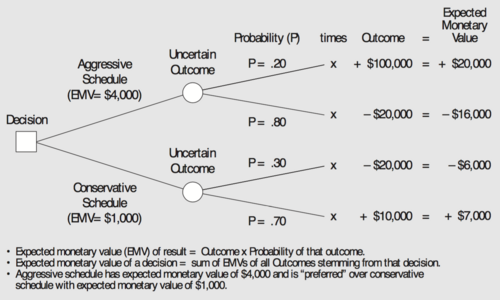
Applying the Decision Tree
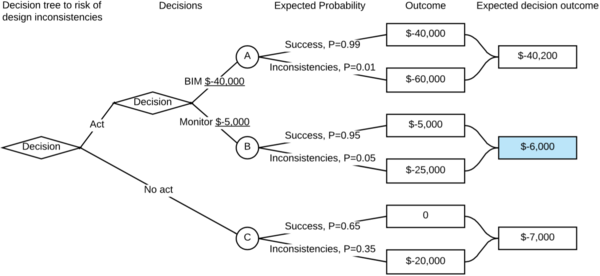
- Replace traditional processes and methods with BIM for clash detection
- Monitor the levels of consistencies more thoroughly through the development process
- Do nothing
- Replace traditional processes and methods with BIM for clash detection
- Monitor the levels of consistencies more thoroughly through the development process
- Do nothing
- Replace traditional processes and methods with BIM for clash detection
- Monitor the levels of consistencies more thoroughly through the development process
- Do nothing
| Consequence of risk | Outcome |
|---|---|
| No inconsistencies | $0 |
| Inconsistencies | $-20,000 |
Yes yes this is tables
| Action | Cost | |
|---|---|---|
| A: | BIM | $-40,000 |
| B: | Monitor | $-5,000 |
| C | No act | $0 |
| Action | Probabilities of outcome | |
|---|---|---|
| Success | Inconsistencies | |
| BIM | 0.99 | 0.01 |
| Monitor | 0.95 | 0.05 |
| No act | 0.65 | 0.35 |
- Replace traditional processes and methods with BIM for clash detection
- Monitor the levels of consistencies more thoroughly through the development process
- Do nothing
- Replace traditional processes and methods with BIM for clash detection
- Monitor the levels of consistencies more thoroughly through the development process
- Do nothing
Usability for Project, Programme and Portfolio Risk Management
Pre and Posterior Decision Making
Benefits and Possibilites
Limitations and Barriers
Some risks can not be used in the decision tree because they would cause too severe consequences and will have to be avoided or externalized.
The probabilities of risks happening can only be estimated to a certain degree of actuality.
Conclusion
Annotated Bibliography
References
- ↑ 1.0 1.1 1.2 Faber, Michael Havbro (2010) Statistics and Probability Theory - In Pursuit of Engineering Decision Support, Publisher: Springer International Publishing AG.
- ↑ 2.0 2.1 Geraldi, Joana and Thuesen, Christian and Stingl, Verena and Oehmen, Josef (2017) How to DO Projects? A Nordic Flavour to Managing Projects: DS-handbook, Version 1.0, Publisher: Dansk Standard
- ↑ 3.0 3.1 Geraldi, Joana and Thuesen, Christian and Stingl, Verena and Oehmen, Josef (2017) Risk identification - basic methods, http://www.doing-projects.org/Conceptbox/Risk-identification-basic-methods [retrieved Sep 20th 2017], Publisher: Doing-Projects.org.
- ↑ Jutte, Bart (2016) 10 GOLDEN RULES OF PROJECT RISK MANAGEMENT, https://www.projectsmart.co.uk/10-golden-rules-of-project-risk-management.php [retrieved Sep 20th 2017], Publisher: Public Smart.
- ↑ 5.0 5.1 Duncan, William R. (1996). A Guide to the Project Management Body of Knowledge, Project Management Institue: PMI Standards Committee.
- ↑ 6.0 6.1 6.2 Winch, Graham M. (2010) Managing Construction Projects - An Information Processing Approach, 2nd Edition, Publisher: John Wiley & Sons, Ltd.
- ↑ 7.0 7.1 Wrona, Vicki (2015) YOUR RISK MANAGEMENT PROCESS: A PRACTICAL AND EFFECTIVE APPROACH, https://www.projectsmart.co.uk/your-risk-management-process-a-practical-and-effective-approach.php [retrieved Sep 22nd 2017], Publisher: Public Smart.