Portfolio Risk Management Process
JensMoller (Talk | contribs) |
|||
| (17 intermediate revisions by one user not shown) | |||
| Line 1: | Line 1: | ||
| + | ''Developed by Jens Møller'' | ||
| − | |||
| − | + | = Abstract = | |
| + | |||
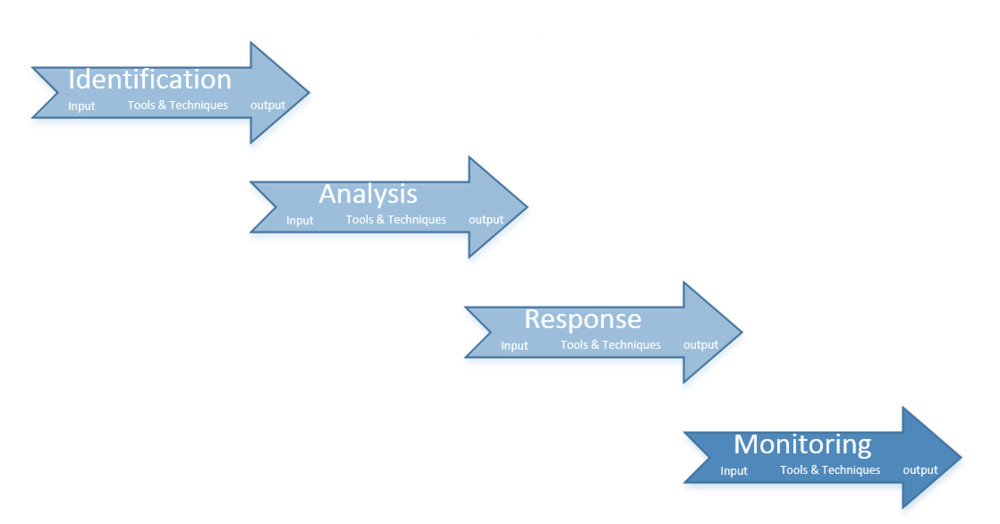
| + | A portfolio manager serves to handle several disciplines, Portfolio Risk Management being one of them<ref name="MP" />. Risks are uncertain. In order to make a solid strategy, with as few surprises as possible, the uncertainties must be dealt with. This area of portfolio management is critical for success. To control the risks affecting a portfolio, one must work through four aspects of "Portfolio Risk Management". These aspects are identification, analysis, development responses and monitoring and control. Therefore, this article will provide guidance on how to structure the framework of the processes and it will explain the content in the aspects. | ||
[[File:Iterative processes.PNG|center|1000px|Ideation tools application]] | [[File:Iterative processes.PNG|center|1000px|Ideation tools application]] | ||
| − | The first aspect is identification. In the identification phase all | + | The first aspect is identification. In the identification phase, all types of risks regarding portfolio management will be found. When the risks have been found, they will be analyzed. A plan of responses will be developed based on the analysis. The plan consists of specific actions, when to execute these actions and who has the acting responsibility once the situation occurs. When the plan has been set, the assigned manager will monitor the risks and their environment. The portfolio manager will act if needed. The assigned manager keeps a record of new findings and new experiences. |
| − | + | ||
| − | + | ||
| + | The process of the four aspects should be handled iteratively, so that all of the aspects are applicable at all times. The first iterative process is from the response phase to the analysis phase. The impact of the developed responses must be analyzed again, to assure that they work as anticipated in relation to the entire portfolio. Another type of iterative process occurs when the conditions of a certain risk change, forcing it to undergo all the phases again. When new risks occur all the phases must be used as described. | ||
[[File:Identification.PNG|center|1000px|Ideation tools application]] | [[File:Identification.PNG|center|1000px|Ideation tools application]] | ||
| + | = Identification of the portfolio risks = | ||
| − | = | + | It is important to realize that there are three types of risks to identify in portfolio risk management<ref name="SPM" />. The types of risks are ''structural risks'', ''component risks'' and ''overall risks''. The ''structural risks'' are the ones related to the interactions between the components. The components consist of either projects or programs. The structural risks are normally threats in terms of resource issues, but they can also be opportunities in terms of niche qualification in the organization. |
| − | + | ''Component Risks'' are normally handled by either the project<ref name="Body" /> or program manager (now component managers). Though, the ''component risks'' may become relevant for the portfolio manager, if the risks escalate and expand out of the mandate of the component manager. The reason for this being that the magnitude of these risks may have significant effect on the portfolio or have a strategic aspect or objective. These kinds of risks are normally related to the three parameters of the Iron Triangle: cost, time and scope. | |
| − | '' | + | The last type of risks are the ''overall risks''. The overall risks are the risks that emerge when components interact in the portfolio. They include all risks that are not defined in the above-mentioned types of risks. The different components can have different objectives, missions or visions, and therefore the components work in different directions. The overall risks may also give the opportunity of distributing "best practice" to other components. |
| − | + | [[File:Knowledge sharing.PNG|thumb|Illustartes knowledge shared between components <ref name= SPM/>]] | |
| − | + | Example: A portfolio has four components, called A, B, C and D. Component B finds best practice in a certain area of expertise, that is applicable in component A and D. This provides the opportunity of optimizing A and D based on the development in component B. | |
| − | + | ==Inputs== | |
| + | The identification phase has various kinds of inputs that can be used to specify the risks in a portfolio. The main categories<ref name="SPM" /> are the ''Enterprise Environmental Factors'', ''Organizational Process Assets'', ''Lists of Selected Portfolio Components'', ''Portfolio Management Plan'' and ''Escalated Component Risks''. It is important to consider which types of inputs that are relevant for the specific portfolio<ref name="Rolf" />. | ||
| + | ''Enterprise Environmental Factors'' is the public information that affects the portfolio e.g. academic studies and benchmarking among others. Some experienced companies use internal databases by sharing gained knowledge throughout the organization. These historical files are called ''Organizational Process Assets''. A third type of input is the ''List of Selected Portfolio Components'' which commonly acts as the baseline of the estimated risks. | ||
| − | ''' | + | ''Portfolio Management Plan'' provides input from a higher level of management regarding scheduling, risks, cost and quality. It shows the known risks in the plan, allocates the responsibility and budgets including the risk premium. The risks will often be illustrated in a Risk Breakdown Structure. |
| − | + | ||
| − | + | The last type of input is the ''Escalated Component Risks'' which are heavily related to component risks. ''Escalated Component Risks'' are the risks that have escalated out of the component managers mandate. | |
| − | + | ==Tools and Techniques== | |
| − | + | Several tools and techniques are highly useful in the process of identifying risks and making a portfolio risk register. The different tools and techniques<ref name="SPM" /> are called ''Documentation Reviews'', ''Information Gathering Techniques'', ''Checklist Analysis'', ''Assumptions Analysis'' and ''Diagramming Techniques''. All the tools have pros and cons. It is important to use the appropriate tools and techniques for the specific situation<ref name="Rolf" />. | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | The ''Documentation Reviews'' is based on big data gained on component management level and matched | + | The ''Documentation Reviews'' is based on big data gained on component management level and matched with the portfolio management objectives. The ''Information Gathering Techniques'' is done by either the [[Brainstorming technique]]<ref name="Wilson" /> <ref name="Body" /> , Delphi technique <ref name="Linstone" /> <ref name="Geraldi" /> ([[The Delphi Technique in Project Management]]), Interviewing, Root Cause Identification or [[SWOT analysis]]. The ''Brainstorming'' is an effective way of making the framework of the identification. It can be done by gathering a group of experts that simply empty their brains in order to get every possible risk on the table. After this exercise the experts organize the risks in a risk breakdown structure. |
| − | When different agendas cloud the objectivity of the process the ''Delphi technique'' can be used. The participants of the ''Delphi technique'' are | + | When different agendas cloud the objectivity of the process the ''Delphi technique'' can be used. The participants of the ''Delphi technique'' are a group of experts and a facilitator. At some point, they anonymously reach agreement with the facilitators concerns regarding the risks. |
''Interviews'' can be used to interpret the risks. The participants can be stakeholders <ref name="Stake" /> <ref name="PRINCE2" />, component participants experts, sponsors and so forth. | ''Interviews'' can be used to interpret the risks. The participants can be stakeholders <ref name="Stake" /> <ref name="PRINCE2" />, component participants experts, sponsors and so forth. | ||
| − | + | The most effective tool is probably the ''Root Cause Identification''. As the name suggests, the tool focuses on the root of the risks. The tool can also be used with the risk breakdown structure, where the risks are categorized by the roots of the risks. | |
| − | + | ||
| − | + | ||
| − | + | To get a broader perspective, the risks related to the dimensions of SWOT-analysis can be effective. It provides both the in-house perspective in relation to strengths and weaknesses and the outgoing perspective of opportunities and threats. | |
| − | The '' | + | The ''Checklist Analysis'' is a nice quick way to identify the risks. Keep in mind that it is based on previous experience and new aspects will often be missed when using this tool. When used on routine work it is very effective. |
| − | + | The ''Assumptions Analysis'', on the other hand, can identify risks which have not been experienced. Possible assumptions are tested and the outcomes are assessed and validated. The tool is efficient for "thinking out of the box". It has the constraints of the participants' imaginations, hence it is important to keep unknown risks in mind. | |
| − | + | [[File:Cause-and-Effect Diagram.PNG|thumb|Cause-and-Effect Diagram (''adopted from The Standard for Portfolio Management'') <ref name= SPM/>]] | |
| + | The last type of tool is the ''Diagramming Techniques''. Basically, they are visualizations of causality in relation to possible risks and portfolio objectives e.g. cause-and-effect diagrams, system or process flow charts and influence diagrams. The tools can also help categorize the risks e.g. Risk Component Chart amongst others. | ||
| − | + | ==Outputs== | |
| − | The Output of the Identification is the ''Portfolio Risk Register''. It is a supplement to the Portfolio | + | The Output of the Identification is the ''Portfolio Risk Register''. It is a supplement to the Portfolio Management Plan and it consists of a list of "identified risks, risk owners, list of potential responses, root causes of risks'' and ''updated risk categories''. It is basically a summary of the work above, i.e. the risks are lined up with the immediate dedicated manager and the mandated responses. If known, it may also contain the root of the risks. The ''Portfolio Risk Register'' should be updated, whenever it is necessary<ref name="SPM" />. |
[[File:Analysis.PNG|center|1000px|Ideation tools application]] | [[File:Analysis.PNG|center|1000px|Ideation tools application]] | ||
| − | + | = Analyze Portfolio Risks = | |
| − | + | ==Input== | |
| − | The input | + | The input for the ''Analyze Portfolio Risks'' phase is the output of the ''Identification'' phase. It consists of the Portfolio Risk Register and the Risk Management Plan<ref name="SPM" /> <ref name="Rolf" />. The risks found in the identification phase will be analyzed. The risks will be prioritized based on the impact and the probability. The impact can have different parameters e.g. financial, environmental, strategic et cetera. The tolerance of the risks will also be a part of the analysis. Time gives an extra dimension to the analysis in terms of immediate responses to the risks. If the information is subject to bias or in other ways not comprehensive, the acting manager should gather the missing information. The analysis must be checked routinely to make sure that the assumptions have not changed, and if so a new analysis should be made. |
| − | + | ==Tools and techniques== | |
| − | + | ||
| − | + | The tools used for the analysis is normally divided into two categories. The ''Risk Probability and Impact Assessment'' and ''the Risk Combining and Modeling Techniques''<ref name="SPM" />. Risk Probability and Impact Assessment investigates the probability of a certain risk happening and the actual impact if it happens. It is very important to keep the quality of the input in mind during this process. The risks should be formulated in measurable variables and parameters in order to calculate the impact and probability as objectively as possible. The probability is normally visualized in distributions e.g. normal distribution. | |
| − | + | [[File:Probability & Impact Matrix.PNG|thumb|Probability & Impact Matrix (''adopted from The Standard for Portfolio Management'') <ref name= SPM/>]] | |
| − | The '' | + | The impact and probability is typically investigated by experts in the ''interviews'' or ''Delphi technique''. The impact and probability is not worth much without each other. Hence the two are often combined in the analysis with tools like ''Probability and Impact Matrix <ref name="Geraldi" /> ([[Risk matrix]])'' or ''financial tools ([[Best Practices for Project Portfolio Selection]])'' that can be combined with [[Scenario Analysis]]. |
| − | [[File:Tornado diagram.PNG|thumb|Tornado Diagram (''adopted from The Standard for Portfolio Management'') <ref name= | + | The ''Risk Combining and Modelling Techniques'' analyzes the components in terms of structure and composition. The analysis reaches beyond the accumulated risks of the components that escalate in magnitude into the portfolio level. It also investigates the risks that exists because of the interaction of the components. It is typically done by using ''sensitivity analysis'' and ''modelling and simulation''. |
| + | |||
| + | [[File:Tornado diagram.PNG|thumb|Tornado Diagram (''adopted from The Standard for Portfolio Management'') <ref name= SPM/>]] | ||
| − | The ''Sensitivity Analysis'' investigates the risks with the biggest impact on the portfolio. It does that when the other parameters are held to the baseline. | + | The ''Sensitivity Analysis'' investigates the risks with the biggest impact on the portfolio. It does that when the other parameters are held to the baseline. The analysis shows the sensitivity of one parameter, which is not the worst-case scenario, but a relatively more likely scenario. The visual output of the ''Sensitivity Analysis'' could be the tornado diagram. This is a strong tool for prioritizing the risks and where to focus the action and response. |
| − | The ''Modeling and simulation'' could be a ''Monte Carlo Technique <ref name="DS" /> ([[Monte Carlo Simulation of Risk]])''. The simulations and | + | The ''Modeling and simulation'' could be a ''Monte Carlo Technique <ref name="DS" /> ([[Monte Carlo Simulation of Risk]])''. The simulations and modeling is based on parametric optimization. The parameters can be several portfolio objectives that are iteratively randomly simulated. The parameters can have financial, time and quality aspects, but basically every important measurable variable can be a parameter. The iteration is typically computer generated. The output can be the most likely scenario or the worst-case scenario. |
| − | + | ==Output== | |
| − | The output of the ''Analyze Portfolio Risks'' | + | The output of the ''Analyze Portfolio Risks'' updates the ''Portfolio Risk Register'' and implements ''Portfolio Risk Exposure charts''. The update consists of a ranking of the list of portfolio risks. The priority can be divided into different objectives and give the portfolio manager a better overview on the objectives. By now, the risk breakdown structure should be categorized into either root causes or portfolio objectives. Some immediate responses can be a part of the output, but focus should be on the risks impacting the near future. The risks that are not prioritized should be formulated on a watch-list for monitoring. Since the processes are iterative, some of the risks will occur in the analysis more than once. Therefore, information about overall trends should be gathered to monitor the anticipated effects. |
| − | ''Portfolio Risk Exposure Charts'' | + | ''Portfolio Risk Exposure Charts'' illustrate the probability of the portfolio reaching either tangible or nontangible objectives, even though risks are mainly formulated measurably. The cumulative distribution can for instance show the probability of a certain magnitude. |
[[File:Response.PNG|center|1000px|Ideation tools application]] | [[File:Response.PNG|center|1000px|Ideation tools application]] | ||
| − | + | = Developed responses based on the analyzed risks = | |
| − | In this phase the portfolio manager must develop responses on the prioritized risks from the analysis. The manager should implement the risk responses into the budget, schedule and portfolio management plan. The responsibility should be clearly defined, which means that risk owners are dedicated to the specific risk and | + | In this phase the portfolio manager must develop responses on the prioritized risks from the analysis. The manager should implement the risk responses into the budget, schedule and portfolio management plan. The responsibility should be clearly defined, which means that risk owners are dedicated to the specific risk and know how to respond to specified developments regarding the risk and when to contact the superior, if the risk expands out of mandate. |
| − | + | ==Input== | |
| − | The input of the response development phase is updated ''Portfolio Management Plan'' and ''Portfolio Risk Register ([[Risk register ]])''. ''A List of Prioritized components'' within | + | The input of the response development phase is the updated ''Portfolio Management Plan'' and ''Portfolio Risk Register ([[Risk register ]])''. ''A List of Prioritized components'' within each strategic category is needed for this phase as well<ref name="SPM" />. |
| − | + | ==Tools and techniques== | |
| − | The risks can be handled in several ways. Responses | + | The risks can be handled in several ways. Responses do not have to be one solution, but can easily be a combination of responses. It is also recommended to have a fallback plan or two. The risk is often met by a curtain budget and timeframe. ''The Response Strategy Selection'' is a variety of responses, that mainly focus on the type of risk and the wanted exposure towards the risk. The responses combined with scenario analysis<ref name="Hindle" /> <ref name="Rox" /> might help to predict future situations<ref name="SPM" />. |
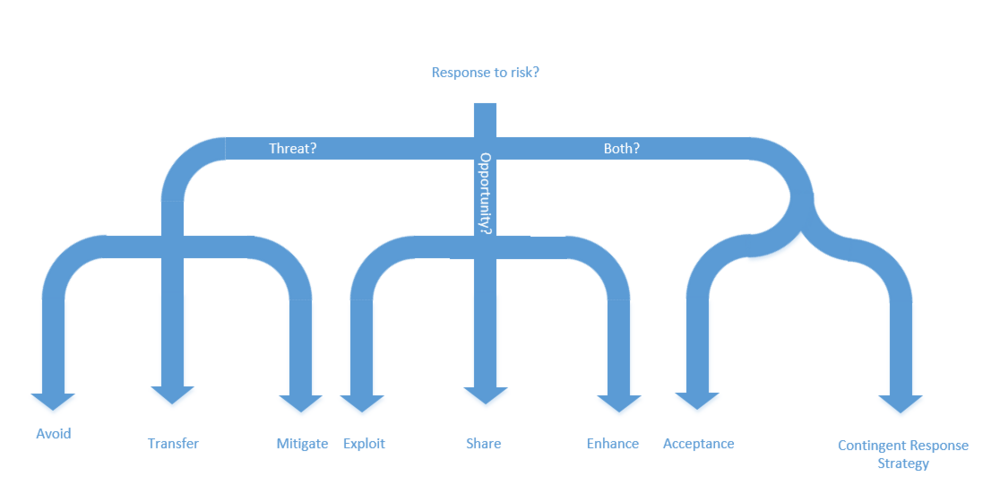
[[File:Response strategies.PNG|center|1000px|Ideation tools application]] | [[File:Response strategies.PNG|center|1000px|Ideation tools application]] | ||
| − | |||
| − | The response strategy can be handled in a lot of ways. In order to structure the approach, the responses can be divided into risks in form of threats, opportunities or both. The threats can be handled in three ways. The manager can either try to avoid, transfer or mitigate the threat. In order to avoid the threats, the portfolio management has to be changed. | + | The response strategy can be handled in a lot of ways. In order to structure the approach, the responses can be divided into risks in form of threats, opportunities or both. The threats can be handled in three ways. The manager can either try to ''avoid'', ''transfer'' or ''mitigate'' the threat. In order to avoid the threats, the portfolio management has to be changed. This can be done by choosing another approach for the same objectives so the portfolio avoids the threat or completely changing the objectives of the portfolio, because the objective is not worth dealing with the threat. |
| − | Another strategy is ''transferring'' the potential threat. It can be done by transferring responsibility of the threatening part of the portfolio. It is mainly used transferring the financial exposure e.g. insurance, guaranties, performance bonds etc. The transfer is normally dictated by law or contracts. | + | Another strategy is ''transferring'' the potential threat. It can be done by transferring the responsibility of the threatening part of the portfolio. It is mainly used for transferring the financial exposure e.g. insurance, guaranties, performance bonds etc. The transfer is normally dictated by law or contracts. |
| − | The third way of dealing with | + | The third way of dealing with threats is to ''mitigate''. When mitigating, the threat reduces in probability, impact or both to the acceptable level. This can be done by splitting the risk or taking early action. |
| − | + | As earlier mentioned, risks are also opportunities. They need to be handled in order to optimize the opportunity exposure in the portfolio. The three opportunity related strategies are ''exploit, share'' and ''enhance''. | |
| − | When ''exploiting'' the opportunity, the manager | + | When ''exploiting'' the opportunity, the manager makes sure to gain from the opportunity. This can be done by allocating more resources in terms of e.g. working hours or material. It can also be done by hiring new employees with new or better competences. |
| − | If | + | If it is not possible to ''exploit'' the opportunity, ''sharing'' can be the way to go. When sharing the opportunity another party is broad in. The other party gets a part of the gain in return for raising the magnitude or chances of realizing the opportunity. This can be done by establishing partnerships e.g. joint venture, special-purpose companies etc. |
| − | The last recommended technique for handling opportunities is ''enhancing''. This means that the value of the opportunity is increased in terms of impact and probability. This can either be done by raising the chances of the trigger conditions or by targeting the impact drivers in order to make the project or | + | The last recommended technique for handling opportunities is ''enhancing''. This means that the value of the opportunity is increased in terms of impact and probability. This can either be done by raising the chances of the trigger conditions, or by targeting the impact drivers in order to make the project's or program's effect on the portfolio greater. |
| − | Other responses can be used for both opportunities and threats. The strategy, ''Acceptance'', can either be passive or active. In the passive acceptance the | + | Other responses can be used for both opportunities and threats. The strategy, ''Acceptance'', can either be passive or active. In the passive acceptance the portfolio manager acts when the risk occurs without planned responses. When using the active acceptance, the responses can be planned and time and resources are allocated to handle the risks that are expected. In addition to this, the active approach might include allocations for unknown risks. |
| − | ''Contingent Response Strategy'' is another type of strategy to handle both threats and opportunities. The predefined response is used if certain trigger conditions | + | ''Contingent Response Strategy'' is another type of strategy to handle both threats and opportunities. The predefined response is used if certain trigger conditions occur. This strategy can be used if the trigger conditions have clear warnings in time to incorporate the planned response. |
| − | The ''scenario analysis'' can also be used | + | The ''scenario analysis'' can also be used. Basically, it consists of several responses based on different outcomes. In order to find appropriate causality related to responses and risks, the previous steps, identification and analysis, might be necessary. |
| + | ==Output== | ||
| − | ''' | + | The output of the developed responses is the updated versions of previously mentioned ''Portfolio Risk Register, Portfolio Management plan'' and ''Portfolio components''. The Portfolio risk register has new elements, which are: |
| − | + | * Response strategies and actions related to the strategy | |
| + | * Trigger plans and related conditions and warnings | ||
| + | * Allocated budget and time for risks in project<ref name="Body" />, program and portfolio level | ||
| + | * Fallback plan if the planned responses do not have the estimated and wanted effect | ||
| + | * Risks, which are created by responses and related strategies | ||
| + | * Expected risks after responses have been executed, consisting of primordial accepted risks and new accepted risks | ||
| − | + | The updated ''Portfolio Components'' includes reevaluated and rearranged components in the categories. The portfolio component might need to be re-balanced in order to keep the susceptibility of the portfolio. ''The Portfolio Management Plan'' is also updated in terms of contingency reserves, schedule and resources, to an extent where the portfolio manager can monitor the risks and its environment and know how to respond when trigger conditions occur<ref name="SPM" />. | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | The updated | + | |
[[File:Monitoring.PNG|center|1000px|Ideation tools application]] | [[File:Monitoring.PNG|center|1000px|Ideation tools application]] | ||
| − | + | = Monitoring and controlling Portfolio risks = | |
| − | In this phase the portfolio manager controls the risks by using the | + | In this phase the portfolio manager controls the risks by using the previously defined risk owners and responses . The monitoring and controlling manager should focus on the belowmentioned elements that are defined in “The Standard for Portfolio Management”: <ref name="SPM" />: |
* Risks | * Risks | ||
* Trigger conditions | * Trigger conditions | ||
| Line 156: | Line 153: | ||
* Efficiency of the risk responses | * Efficiency of the risk responses | ||
| − | + | In addition to the elements above, the monitoring phase contains the identification of emerging risks. The portfolio manager should also analyze and develop responses to both emerging and existing risks. The existing risks are included because the environment of the risks change throughout time. The portfolios attitude towards susceptibility or strategy might change as well. | |
| + | ==Input== | ||
| − | ''' | + | The input consists of ''Updated Portfolio management plan'', ''Portfolio Risk Register'', ''Component Progress Report'' and ''Additional Component Data''. |
| − | + | ==Tools and techniques== | |
| − | ''' | + | When the portfolio risks must be monitored, a handful of tools and techniques are useful. ''Portfolio Risk Audits'' focuses on the documentation of the effectiveness of the risk responses. Based on the performance data, the portfolio manager finds trends in order to ensure the forecasts still point in the direction of the portfolio strategy. This type of tool is called ''Variance and Trend Analysis''<ref name="SPM" />. |
| − | + | ''Status Meetings<ref name="Body" /> ([[Meeting strategies ]])'' should be incorporated as a periodic event, where discussion is focused on newly identified risks and a walk-through of the phases of Portfolio Risk Management. | |
| − | '' | + | The last tool for monitoring is the ''Portfolio Risk Reassessment''. This tool is used to identify, analyze and develop responses to new risks. The technique is also used if the risks escalate into unanticipated areas, for instance if risks emerge from the watch-list into a priority-list. The risk environment can change in impact or probability; thus, a reassessment must be done. The reassessment must be done in the entire lifecycle of the portfolio. |
| − | + | ==Output== | |
| − | + | ||
| − | + | ||
The output consists of the ''Portfolio Change Requests'', ''Portfolio Risk Register'' and ''Organizational Process Assets''. An integration of responses in the ''Portfolio Management Plan'' is done in the ''Portfolio Change Requests'' together with the chosen way of monitoring. | The output consists of the ''Portfolio Change Requests'', ''Portfolio Risk Register'' and ''Organizational Process Assets''. An integration of responses in the ''Portfolio Management Plan'' is done in the ''Portfolio Change Requests'' together with the chosen way of monitoring. | ||
| − | The new elements in the ''Portfolio Risk Register'' | + | The new elements in the ''Portfolio Risk Register'' are the outcomes from the ''Portfolio Risk Reassessment'' including an update of the described elements in "Tools and techniques". The Risk Register also contains documentation of the actual risk evolvement and the efficiency of the responses for future use. |
| − | The last element of the output is the ''Organizational Assets'' | + | The last element of the output is the ''Organizational Assets'' which state that the four phases of ''Portfolio Risk Management'' might contribute with some changes in the organizational processes, if needed.<ref name="SPM" />. |
| − | + | =Conclusion= | |
| − | + | This guide should provide the framework for Portfolio Risk Management. When the guide has been followed and reflections have been made regarding appropriate tools and techniques, the ''Portfolio Risk Management Processes'' should provide good management guidance in relation to risks and uncertainty. In order for the guide to be efficient, it is important to use it in a structured manner. The organization is also provided with the opportunity to optimize the processes in terms of risk control. | |
| − | + | = Limitations = | |
| − | + | ||
| − | + | Portfolio Risk Management is obviously not the whole truth. It tries to predict how the risks evolve. The methods in the described process and the process itself has some limitations. Some of these are stated below: | |
| − | * | + | * The entire investigation assumes that the world will act in the way we have seen before. |
| − | * | + | * Unforeseen events will happen randomly. |
| − | * | + | * The investigation should serve as support to the decisions, but the manager shouldn’t make decisions entirely based on the results of the investigation. |
| − | * | + | * It is not always worth spending time and money on the risk manager, if the risks are too insignificant or if the handling of the risks cannot be implemented. |
| − | * | + | * The assumption that human behavior can be predicted can also be challenged. Humans have always evolved and their behavior is to some extent unique. |
| − | * | + | * Mega-trends can be extremely difficult to forecast and the investigation is to some extent dependent on the mega-trend assumptions. |
| + | * In a rapidly changing world where the risk environment changes all the time, the risk manager should ask himself if he can make his forecasts before the environment changes again. | ||
| − | + | = Annotated bibliography = | |
| − | '''The Standard for Portfolio Management, Second Edition, Project Management Institute, 2008''' is one of the standards in the field of Portfolio management, | + | '''The Standard for Portfolio Management, Second Edition, Project Management Institute, 2008''' is one of the standards in the field of Portfolio management, thus the credibility is very high. It focuses more on the Risk Management than other standards, but has the same framework regarding the processes as most standards, just more detailed. It gives a good overview of all the portfolio management aspects. |
| − | '''A Guide to the Project Management Body of Knowledge (PMBOK® Guide), Fifth Edition, Project Management Institute, 2013''' is one of the most well-known standards in the field of project management, | + | '''A Guide to the Project Management Body of Knowledge (PMBOK® Guide), Fifth Edition, Project Management Institute, 2013''' is one of the most well-known standards in the field of project management, thus it has also a great credibility. It is great for getting to know, what the components in the portfolio consists of. |
| − | '''Management of Portfolios, Office Of Government Commerce, TSO, 2011''' Gives a broader perspective to the duties of the portfolio manager. It is also a very well-known and the credibility is high as well. It is on the other hand not very good for Portfolio Risk Management. | + | '''Management of Portfolios, Office Of Government Commerce, TSO, 2011''' Gives a broader perspective to the duties of the portfolio manager. It is also a very well-known and the credibility is high as well. It is on the other hand not very good for Portfolio Risk Management. |
| − | + | = References = | |
| − | + | ||
| − | + | ||
<references> | <references> | ||
| + | |||
<ref name="SPM">The Standard for Portfolio Management, Second Edition, Project Management Institute, 2008</ref> | <ref name="SPM">The Standard for Portfolio Management, Second Edition, Project Management Institute, 2008</ref> | ||
| Line 219: | Line 214: | ||
<ref name="MP"> Management of Portfolios, Office Of Government Commerce, TSO, 2011</ref> | <ref name="MP"> Management of Portfolios, Office Of Government Commerce, TSO, 2011</ref> | ||
| − | |||
| − | + | <ref name="Rolf"> Risk management in a multi-project environment An approach to manage portfolio risks Rolf Olsson, Bombardier Transportation, Vasteras, Sweden, 2007</ref> | |
| − | + | <ref name="Wilson"> Wilson, C. (2013) Brainstorming and beyond: A User-Centered Design Method. Morgan Kaufmann.</ref> | |
| − | <ref name=" | + | |
| − | <ref name=" | + | <ref name="Geraldi"> Geraldi J., Thuesen C., Oehmen J., How to do Projects, Version 0.5 </ref> |
| − | <ref name=" | + | <ref name="Linstone"> Linstone, H.A. and Turoff, M. (eds.) (1975 and 2002 reviewed version) The Delphi Method Techniques and Applications.</ref> |
| − | <ref name=" | + | <ref name="Rox">Roxburgh, C., (2009), “The use and abuse of scenarios” online article: http://www.mckinsey.com/business-functions/strategy-and-corporate-finance/our-insights/the-use-and-abuse-of-scenarios </ref> |
| − | <ref name=" | + | <ref name="Hindle">Hindle, T., (2008), “Scenario Planning”, The Economist, online article: http://www.economist.com/node/12000755 </ref> |
| − | <ref name=" | + | <ref name="DS">Danish Standards,ISO 31000 Risk management - Principles and guidelines 2009 </ref> |
| − | <ref name=" | + | <ref name="Stake">Developing Stakeholder Theory, Andrew L. Friedman and Samantha Miles, Journal of Management Studies 39, January 2002 </ref> |
| − | <ref name=" | + | <ref name="PRINCE2">Managing successful projects with PRINCE2, TSO, 2009 </ref> |
| − | < | + | <references /> |
| − | + | ||
| + | [[Category:Portfolio Management]] | ||
Latest revision as of 16:20, 16 November 2018
Developed by Jens Møller
Contents |
[edit] Abstract
A portfolio manager serves to handle several disciplines, Portfolio Risk Management being one of them[1]. Risks are uncertain. In order to make a solid strategy, with as few surprises as possible, the uncertainties must be dealt with. This area of portfolio management is critical for success. To control the risks affecting a portfolio, one must work through four aspects of "Portfolio Risk Management". These aspects are identification, analysis, development responses and monitoring and control. Therefore, this article will provide guidance on how to structure the framework of the processes and it will explain the content in the aspects.
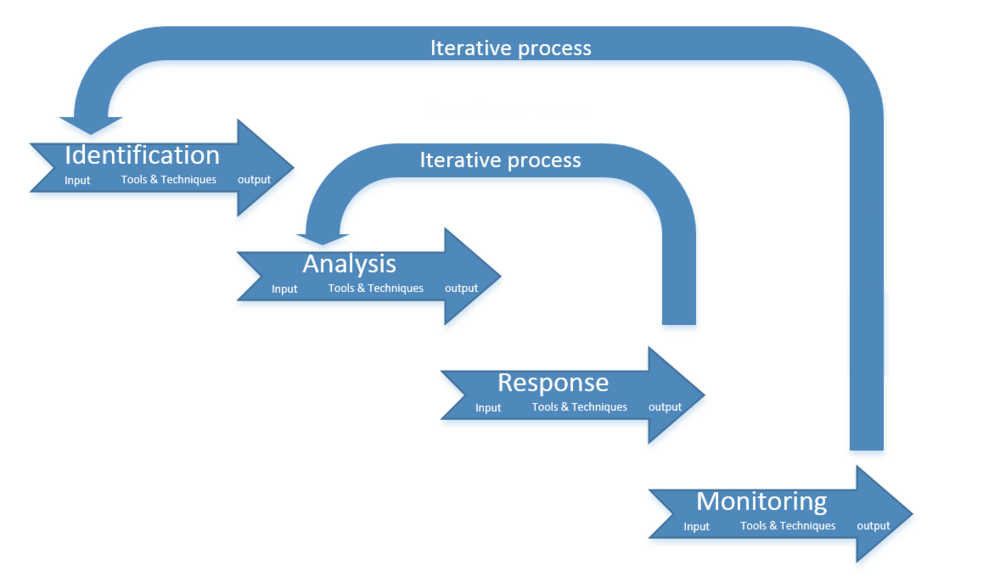
The first aspect is identification. In the identification phase, all types of risks regarding portfolio management will be found. When the risks have been found, they will be analyzed. A plan of responses will be developed based on the analysis. The plan consists of specific actions, when to execute these actions and who has the acting responsibility once the situation occurs. When the plan has been set, the assigned manager will monitor the risks and their environment. The portfolio manager will act if needed. The assigned manager keeps a record of new findings and new experiences.
The process of the four aspects should be handled iteratively, so that all of the aspects are applicable at all times. The first iterative process is from the response phase to the analysis phase. The impact of the developed responses must be analyzed again, to assure that they work as anticipated in relation to the entire portfolio. Another type of iterative process occurs when the conditions of a certain risk change, forcing it to undergo all the phases again. When new risks occur all the phases must be used as described.
[edit] Identification of the portfolio risks
It is important to realize that there are three types of risks to identify in portfolio risk management[2]. The types of risks are structural risks, component risks and overall risks. The structural risks are the ones related to the interactions between the components. The components consist of either projects or programs. The structural risks are normally threats in terms of resource issues, but they can also be opportunities in terms of niche qualification in the organization.
Component Risks are normally handled by either the project[3] or program manager (now component managers). Though, the component risks may become relevant for the portfolio manager, if the risks escalate and expand out of the mandate of the component manager. The reason for this being that the magnitude of these risks may have significant effect on the portfolio or have a strategic aspect or objective. These kinds of risks are normally related to the three parameters of the Iron Triangle: cost, time and scope.
The last type of risks are the overall risks. The overall risks are the risks that emerge when components interact in the portfolio. They include all risks that are not defined in the above-mentioned types of risks. The different components can have different objectives, missions or visions, and therefore the components work in different directions. The overall risks may also give the opportunity of distributing "best practice" to other components.
Example: A portfolio has four components, called A, B, C and D. Component B finds best practice in a certain area of expertise, that is applicable in component A and D. This provides the opportunity of optimizing A and D based on the development in component B.
[edit] Inputs
The identification phase has various kinds of inputs that can be used to specify the risks in a portfolio. The main categories[2] are the Enterprise Environmental Factors, Organizational Process Assets, Lists of Selected Portfolio Components, Portfolio Management Plan and Escalated Component Risks. It is important to consider which types of inputs that are relevant for the specific portfolio[4].
Enterprise Environmental Factors is the public information that affects the portfolio e.g. academic studies and benchmarking among others. Some experienced companies use internal databases by sharing gained knowledge throughout the organization. These historical files are called Organizational Process Assets. A third type of input is the List of Selected Portfolio Components which commonly acts as the baseline of the estimated risks.
Portfolio Management Plan provides input from a higher level of management regarding scheduling, risks, cost and quality. It shows the known risks in the plan, allocates the responsibility and budgets including the risk premium. The risks will often be illustrated in a Risk Breakdown Structure.
The last type of input is the Escalated Component Risks which are heavily related to component risks. Escalated Component Risks are the risks that have escalated out of the component managers mandate.
[edit] Tools and Techniques
Several tools and techniques are highly useful in the process of identifying risks and making a portfolio risk register. The different tools and techniques[2] are called Documentation Reviews, Information Gathering Techniques, Checklist Analysis, Assumptions Analysis and Diagramming Techniques. All the tools have pros and cons. It is important to use the appropriate tools and techniques for the specific situation[4].
The Documentation Reviews is based on big data gained on component management level and matched with the portfolio management objectives. The Information Gathering Techniques is done by either the Brainstorming technique[5] [3] , Delphi technique [6] [7] (The Delphi Technique in Project Management), Interviewing, Root Cause Identification or SWOT analysis. The Brainstorming is an effective way of making the framework of the identification. It can be done by gathering a group of experts that simply empty their brains in order to get every possible risk on the table. After this exercise the experts organize the risks in a risk breakdown structure.
When different agendas cloud the objectivity of the process the Delphi technique can be used. The participants of the Delphi technique are a group of experts and a facilitator. At some point, they anonymously reach agreement with the facilitators concerns regarding the risks.
Interviews can be used to interpret the risks. The participants can be stakeholders [8] [9], component participants experts, sponsors and so forth.
The most effective tool is probably the Root Cause Identification. As the name suggests, the tool focuses on the root of the risks. The tool can also be used with the risk breakdown structure, where the risks are categorized by the roots of the risks.
To get a broader perspective, the risks related to the dimensions of SWOT-analysis can be effective. It provides both the in-house perspective in relation to strengths and weaknesses and the outgoing perspective of opportunities and threats.
The Checklist Analysis is a nice quick way to identify the risks. Keep in mind that it is based on previous experience and new aspects will often be missed when using this tool. When used on routine work it is very effective.
The Assumptions Analysis, on the other hand, can identify risks which have not been experienced. Possible assumptions are tested and the outcomes are assessed and validated. The tool is efficient for "thinking out of the box". It has the constraints of the participants' imaginations, hence it is important to keep unknown risks in mind.
The last type of tool is the Diagramming Techniques. Basically, they are visualizations of causality in relation to possible risks and portfolio objectives e.g. cause-and-effect diagrams, system or process flow charts and influence diagrams. The tools can also help categorize the risks e.g. Risk Component Chart amongst others.
[edit] Outputs
The Output of the Identification is the Portfolio Risk Register. It is a supplement to the Portfolio Management Plan and it consists of a list of "identified risks, risk owners, list of potential responses, root causes of risks and updated risk categories. It is basically a summary of the work above, i.e. the risks are lined up with the immediate dedicated manager and the mandated responses. If known, it may also contain the root of the risks. The Portfolio Risk Register should be updated, whenever it is necessary[2].
[edit] Analyze Portfolio Risks
[edit] Input
The input for the Analyze Portfolio Risks phase is the output of the Identification phase. It consists of the Portfolio Risk Register and the Risk Management Plan[2] [4]. The risks found in the identification phase will be analyzed. The risks will be prioritized based on the impact and the probability. The impact can have different parameters e.g. financial, environmental, strategic et cetera. The tolerance of the risks will also be a part of the analysis. Time gives an extra dimension to the analysis in terms of immediate responses to the risks. If the information is subject to bias or in other ways not comprehensive, the acting manager should gather the missing information. The analysis must be checked routinely to make sure that the assumptions have not changed, and if so a new analysis should be made.
[edit] Tools and techniques
The tools used for the analysis is normally divided into two categories. The Risk Probability and Impact Assessment and the Risk Combining and Modeling Techniques[2]. Risk Probability and Impact Assessment investigates the probability of a certain risk happening and the actual impact if it happens. It is very important to keep the quality of the input in mind during this process. The risks should be formulated in measurable variables and parameters in order to calculate the impact and probability as objectively as possible. The probability is normally visualized in distributions e.g. normal distribution.
The impact and probability is typically investigated by experts in the interviews or Delphi technique. The impact and probability is not worth much without each other. Hence the two are often combined in the analysis with tools like Probability and Impact Matrix [7] (Risk matrix) or financial tools (Best Practices for Project Portfolio Selection) that can be combined with Scenario Analysis.
The Risk Combining and Modelling Techniques analyzes the components in terms of structure and composition. The analysis reaches beyond the accumulated risks of the components that escalate in magnitude into the portfolio level. It also investigates the risks that exists because of the interaction of the components. It is typically done by using sensitivity analysis and modelling and simulation.

The Sensitivity Analysis investigates the risks with the biggest impact on the portfolio. It does that when the other parameters are held to the baseline. The analysis shows the sensitivity of one parameter, which is not the worst-case scenario, but a relatively more likely scenario. The visual output of the Sensitivity Analysis could be the tornado diagram. This is a strong tool for prioritizing the risks and where to focus the action and response.
The Modeling and simulation could be a Monte Carlo Technique [10] (Monte Carlo Simulation of Risk). The simulations and modeling is based on parametric optimization. The parameters can be several portfolio objectives that are iteratively randomly simulated. The parameters can have financial, time and quality aspects, but basically every important measurable variable can be a parameter. The iteration is typically computer generated. The output can be the most likely scenario or the worst-case scenario.
[edit] Output
The output of the Analyze Portfolio Risks updates the Portfolio Risk Register and implements Portfolio Risk Exposure charts. The update consists of a ranking of the list of portfolio risks. The priority can be divided into different objectives and give the portfolio manager a better overview on the objectives. By now, the risk breakdown structure should be categorized into either root causes or portfolio objectives. Some immediate responses can be a part of the output, but focus should be on the risks impacting the near future. The risks that are not prioritized should be formulated on a watch-list for monitoring. Since the processes are iterative, some of the risks will occur in the analysis more than once. Therefore, information about overall trends should be gathered to monitor the anticipated effects.
Portfolio Risk Exposure Charts illustrate the probability of the portfolio reaching either tangible or nontangible objectives, even though risks are mainly formulated measurably. The cumulative distribution can for instance show the probability of a certain magnitude.
[edit] Developed responses based on the analyzed risks
In this phase the portfolio manager must develop responses on the prioritized risks from the analysis. The manager should implement the risk responses into the budget, schedule and portfolio management plan. The responsibility should be clearly defined, which means that risk owners are dedicated to the specific risk and know how to respond to specified developments regarding the risk and when to contact the superior, if the risk expands out of mandate.
[edit] Input
The input of the response development phase is the updated Portfolio Management Plan and Portfolio Risk Register (Risk register ). A List of Prioritized components within each strategic category is needed for this phase as well[2].
[edit] Tools and techniques
The risks can be handled in several ways. Responses do not have to be one solution, but can easily be a combination of responses. It is also recommended to have a fallback plan or two. The risk is often met by a curtain budget and timeframe. The Response Strategy Selection is a variety of responses, that mainly focus on the type of risk and the wanted exposure towards the risk. The responses combined with scenario analysis[11] [12] might help to predict future situations[2].
The response strategy can be handled in a lot of ways. In order to structure the approach, the responses can be divided into risks in form of threats, opportunities or both. The threats can be handled in three ways. The manager can either try to avoid, transfer or mitigate the threat. In order to avoid the threats, the portfolio management has to be changed. This can be done by choosing another approach for the same objectives so the portfolio avoids the threat or completely changing the objectives of the portfolio, because the objective is not worth dealing with the threat.
Another strategy is transferring the potential threat. It can be done by transferring the responsibility of the threatening part of the portfolio. It is mainly used for transferring the financial exposure e.g. insurance, guaranties, performance bonds etc. The transfer is normally dictated by law or contracts.
The third way of dealing with threats is to mitigate. When mitigating, the threat reduces in probability, impact or both to the acceptable level. This can be done by splitting the risk or taking early action.
As earlier mentioned, risks are also opportunities. They need to be handled in order to optimize the opportunity exposure in the portfolio. The three opportunity related strategies are exploit, share and enhance.
When exploiting the opportunity, the manager makes sure to gain from the opportunity. This can be done by allocating more resources in terms of e.g. working hours or material. It can also be done by hiring new employees with new or better competences.
If it is not possible to exploit the opportunity, sharing can be the way to go. When sharing the opportunity another party is broad in. The other party gets a part of the gain in return for raising the magnitude or chances of realizing the opportunity. This can be done by establishing partnerships e.g. joint venture, special-purpose companies etc.
The last recommended technique for handling opportunities is enhancing. This means that the value of the opportunity is increased in terms of impact and probability. This can either be done by raising the chances of the trigger conditions, or by targeting the impact drivers in order to make the project's or program's effect on the portfolio greater.
Other responses can be used for both opportunities and threats. The strategy, Acceptance, can either be passive or active. In the passive acceptance the portfolio manager acts when the risk occurs without planned responses. When using the active acceptance, the responses can be planned and time and resources are allocated to handle the risks that are expected. In addition to this, the active approach might include allocations for unknown risks.
Contingent Response Strategy is another type of strategy to handle both threats and opportunities. The predefined response is used if certain trigger conditions occur. This strategy can be used if the trigger conditions have clear warnings in time to incorporate the planned response.
The scenario analysis can also be used. Basically, it consists of several responses based on different outcomes. In order to find appropriate causality related to responses and risks, the previous steps, identification and analysis, might be necessary.
[edit] Output
The output of the developed responses is the updated versions of previously mentioned Portfolio Risk Register, Portfolio Management plan and Portfolio components. The Portfolio risk register has new elements, which are:
- Response strategies and actions related to the strategy
- Trigger plans and related conditions and warnings
- Allocated budget and time for risks in project[3], program and portfolio level
- Fallback plan if the planned responses do not have the estimated and wanted effect
- Risks, which are created by responses and related strategies
- Expected risks after responses have been executed, consisting of primordial accepted risks and new accepted risks
The updated Portfolio Components includes reevaluated and rearranged components in the categories. The portfolio component might need to be re-balanced in order to keep the susceptibility of the portfolio. The Portfolio Management Plan is also updated in terms of contingency reserves, schedule and resources, to an extent where the portfolio manager can monitor the risks and its environment and know how to respond when trigger conditions occur[2].
[edit] Monitoring and controlling Portfolio risks
In this phase the portfolio manager controls the risks by using the previously defined risk owners and responses . The monitoring and controlling manager should focus on the belowmentioned elements that are defined in “The Standard for Portfolio Management”: [2]:
- Risks
- Trigger conditions
- Contingency plans
- Residual risks
- Stakeholders[8] [9] (Stakeholder Management )
- Risk responses
- Efficiency of the risk responses
In addition to the elements above, the monitoring phase contains the identification of emerging risks. The portfolio manager should also analyze and develop responses to both emerging and existing risks. The existing risks are included because the environment of the risks change throughout time. The portfolios attitude towards susceptibility or strategy might change as well.
[edit] Input
The input consists of Updated Portfolio management plan, Portfolio Risk Register, Component Progress Report and Additional Component Data.
[edit] Tools and techniques
When the portfolio risks must be monitored, a handful of tools and techniques are useful. Portfolio Risk Audits focuses on the documentation of the effectiveness of the risk responses. Based on the performance data, the portfolio manager finds trends in order to ensure the forecasts still point in the direction of the portfolio strategy. This type of tool is called Variance and Trend Analysis[2].
Status Meetings[3] (Meeting strategies ) should be incorporated as a periodic event, where discussion is focused on newly identified risks and a walk-through of the phases of Portfolio Risk Management.
The last tool for monitoring is the Portfolio Risk Reassessment. This tool is used to identify, analyze and develop responses to new risks. The technique is also used if the risks escalate into unanticipated areas, for instance if risks emerge from the watch-list into a priority-list. The risk environment can change in impact or probability; thus, a reassessment must be done. The reassessment must be done in the entire lifecycle of the portfolio.
[edit] Output
The output consists of the Portfolio Change Requests, Portfolio Risk Register and Organizational Process Assets. An integration of responses in the Portfolio Management Plan is done in the Portfolio Change Requests together with the chosen way of monitoring.
The new elements in the Portfolio Risk Register are the outcomes from the Portfolio Risk Reassessment including an update of the described elements in "Tools and techniques". The Risk Register also contains documentation of the actual risk evolvement and the efficiency of the responses for future use.
The last element of the output is the Organizational Assets which state that the four phases of Portfolio Risk Management might contribute with some changes in the organizational processes, if needed.[2].
[edit] Conclusion
This guide should provide the framework for Portfolio Risk Management. When the guide has been followed and reflections have been made regarding appropriate tools and techniques, the Portfolio Risk Management Processes should provide good management guidance in relation to risks and uncertainty. In order for the guide to be efficient, it is important to use it in a structured manner. The organization is also provided with the opportunity to optimize the processes in terms of risk control.
[edit] Limitations
Portfolio Risk Management is obviously not the whole truth. It tries to predict how the risks evolve. The methods in the described process and the process itself has some limitations. Some of these are stated below:
- The entire investigation assumes that the world will act in the way we have seen before.
- Unforeseen events will happen randomly.
- The investigation should serve as support to the decisions, but the manager shouldn’t make decisions entirely based on the results of the investigation.
- It is not always worth spending time and money on the risk manager, if the risks are too insignificant or if the handling of the risks cannot be implemented.
- The assumption that human behavior can be predicted can also be challenged. Humans have always evolved and their behavior is to some extent unique.
- Mega-trends can be extremely difficult to forecast and the investigation is to some extent dependent on the mega-trend assumptions.
- In a rapidly changing world where the risk environment changes all the time, the risk manager should ask himself if he can make his forecasts before the environment changes again.
[edit] Annotated bibliography
The Standard for Portfolio Management, Second Edition, Project Management Institute, 2008 is one of the standards in the field of Portfolio management, thus the credibility is very high. It focuses more on the Risk Management than other standards, but has the same framework regarding the processes as most standards, just more detailed. It gives a good overview of all the portfolio management aspects.
A Guide to the Project Management Body of Knowledge (PMBOK® Guide), Fifth Edition, Project Management Institute, 2013 is one of the most well-known standards in the field of project management, thus it has also a great credibility. It is great for getting to know, what the components in the portfolio consists of.
Management of Portfolios, Office Of Government Commerce, TSO, 2011 Gives a broader perspective to the duties of the portfolio manager. It is also a very well-known and the credibility is high as well. It is on the other hand not very good for Portfolio Risk Management.
[edit] References
- ↑ Management of Portfolios, Office Of Government Commerce, TSO, 2011
- ↑ 2.00 2.01 2.02 2.03 2.04 2.05 2.06 2.07 2.08 2.09 2.10 2.11 2.12 2.13 2.14 2.15 The Standard for Portfolio Management, Second Edition, Project Management Institute, 2008
- ↑ 3.0 3.1 3.2 3.3 A Guide to the Project Management Body of Knowledge (PMBOK® Guide), Fifth Edition, Project Management Institute, 2013
- ↑ 4.0 4.1 4.2 Risk management in a multi-project environment An approach to manage portfolio risks Rolf Olsson, Bombardier Transportation, Vasteras, Sweden, 2007
- ↑ Wilson, C. (2013) Brainstorming and beyond: A User-Centered Design Method. Morgan Kaufmann.
- ↑ Linstone, H.A. and Turoff, M. (eds.) (1975 and 2002 reviewed version) The Delphi Method Techniques and Applications.
- ↑ 7.0 7.1 Geraldi J., Thuesen C., Oehmen J., How to do Projects, Version 0.5
- ↑ 8.0 8.1 Developing Stakeholder Theory, Andrew L. Friedman and Samantha Miles, Journal of Management Studies 39, January 2002
- ↑ 9.0 9.1 Managing successful projects with PRINCE2, TSO, 2009
- ↑ Danish Standards,ISO 31000 Risk management - Principles and guidelines 2009
- ↑ Hindle, T., (2008), “Scenario Planning”, The Economist, online article: http://www.economist.com/node/12000755
- ↑ Roxburgh, C., (2009), “The use and abuse of scenarios” online article: http://www.mckinsey.com/business-functions/strategy-and-corporate-finance/our-insights/the-use-and-abuse-of-scenarios