Risk Treatment in project management
(→Risk Mitigation) |
(→Annotated bibliography) |
||
| (70 intermediate revisions by one user not shown) | |||
| Line 1: | Line 1: | ||
| − | + | '' By: William Taul Madsen '' | |
| − | = Abstract = | + | == Abstract == |
In a project, a program, or a portfolio there will always be a number of activities. All these activities will involve risk to some degree – either as a threat or an opportunity. If risks are not managed in the project, program, or portfolio it will be difficult to accomplish success. Therefore, it is important for the project, program, or portfolio leader to manage these risks by identifying them, evaluate them and treat them. The latter will be the focus of this article. | In a project, a program, or a portfolio there will always be a number of activities. All these activities will involve risk to some degree – either as a threat or an opportunity. If risks are not managed in the project, program, or portfolio it will be difficult to accomplish success. Therefore, it is important for the project, program, or portfolio leader to manage these risks by identifying them, evaluate them and treat them. The latter will be the focus of this article. | ||
| − | |||
| − | |||
| − | |||
| − | = Big Idea = | + | Risk Treatment is the discipline within Risk Management that takes place once a risk has been identified and assessed. Here, appropriate measures are put in place to mitigate and reduce all unacceptable risks to steer them towards an acceptable target level<ref name=DS_31010> Danish Standards Association (2019), DS/EN IEC 31010:2019, Risk management - Risk assessment techniques, Retrieved March 27 from https://sd.ds.dk/Viewer?ProjectNr=M321462&Status=60.60</ref>. The identification of the treatment measures should be done from a cost benefit point of view, analysing the cost of treating the risk up against the potential benefits<ref name=cyber> Refsdal, A., Solhaug, B., & Stølen, K. (2015). Cyber-Risk Management (SpringerBriefs in Computer Science) (1st ed. 2015 ed.). Springer. </ref>. Furthermore, as time and resource are often a limited factor, the identification and treatment should be focused on the most important risks identified from the preliminary evaluation phase. |
| + | Risk Treatment is mainly split into four categories, namely ''risk avoidance'', ''risk sharing'', ''risk mitigation'' and ''risk acceptance''. Risk avoidance is the option where one simply avoids the underlying activity that causes the potential risk. Risk transfer (also known as risk sharing) is done by transferring either fully or parts of the risk to other stakeholders e.g., by insurance or by outsourcing the related activities externally. Risk mitigation is done by removing sources of threats, reducing or removing the severity of vulnerabilities and by generally reducing the likelihood of threats through mitigation. Lastly, risk acceptance is the category where the risk is accepted, due to either an acceptable threat level or a too costly treatment given the alternative options. <ref name=DS/ISO31000> International Organization for Standardization (2018), DS/ISO 31000:2018, Risk management - Guidelines, Retrieved from https://sd.ds.dk/Viewer?ProjectNr=M296412&Status=60.60&Inline=true&Page=1&VariantID=41 </ref> | ||
| + | Once appropriate treatment measures have been selected, an action plan should be developed to 1) ensure that the chosen treatment options are communicated and 2) to ensure the chosen measures are implemented and acted on.<ref name=rt_enisa> ''Risk Treatment.'' (2021, June). ENISA, European Union Agency for Cybersecurity. Retrieved March 19, 2022, from: https://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/risk-management-inventory/rm-process/risk-treatment </ref> The action plan should be approved and shared with top management and internal and external stakeholders. | ||
| + | |||
| + | == Big Idea == | ||
[[File:Risk_treatment_process.png|thumb|550px|Figure 1: The risk management process from establishing the context, risk identification, risk analysis, risk evaluation, and finally risk treatment.<ref name=DS/ISO31000_2009/>]] | [[File:Risk_treatment_process.png|thumb|550px|Figure 1: The risk management process from establishing the context, risk identification, risk analysis, risk evaluation, and finally risk treatment.<ref name=DS/ISO31000_2009/>]] | ||
To understand risk treatment, it is first necessary to understand what Risk Management is and where in the Risk Management process the treatment occurs. | To understand risk treatment, it is first necessary to understand what Risk Management is and where in the Risk Management process the treatment occurs. | ||
| Line 13: | Line 14: | ||
First, the context of the project, program or portfolio needs to be established. This is done by articulating objectives, defining the parameters that needs to be considered, both internally and externally, and setting the overall scope of the project, program or portfolio. Secondly, the Risk Assessment phase should be initiated. This phase consists of three steps. | First, the context of the project, program or portfolio needs to be established. This is done by articulating objectives, defining the parameters that needs to be considered, both internally and externally, and setting the overall scope of the project, program or portfolio. Secondly, the Risk Assessment phase should be initiated. This phase consists of three steps. | ||
| − | First step is the Risk Identification phase. Here, a comprehensive list of risks related to the project, program or portfolio is made which creates the foundation for the risk analysis. In the risk analysis, all risks from the identification phase are understood by considering their causes and sources, their potential consequences, and the likelihood of occurrence. | + | First step is the Risk Identification phase. Here, a comprehensive list of risks related to the project, program or portfolio is made which creates the foundation for the risk analysis. In the risk analysis, all risks from the identification phase are understood by considering their causes and sources, their potential consequences, and the likelihood of occurrence <ref name=DS/ISO31000_2009/>. |
The risks are then evaluated based on the analysis. This creates a benchmark for the decision making where risks are to be prioritized, leading the risk management process into the final phase, Risk Treatment. This topic will be expanded further in the following section. | The risks are then evaluated based on the analysis. This creates a benchmark for the decision making where risks are to be prioritized, leading the risk management process into the final phase, Risk Treatment. This topic will be expanded further in the following section. | ||
<br/ > | <br/ > | ||
| Line 29: | Line 30: | ||
<br/ > | <br/ > | ||
| − | = Risk Treatment = | + | == Risk Treatment == |
| − | As previously described, Risk Treatment is the last activity in the Risk Management process. This is the part of the process where the risk is actually being treated and one tries to mitigate the potential consequences. Risk Treatment both addresses the positive and negatives risks, accordingly also referred to as ''opportunities'' and ''threats''. Opportunities are the risks that have the potential to create a positive impact on the project, program or portfolio while threats are the kind of risk that are likely to have a negative impact on the project, program or portfolio. The latter is often the type of risk that people think of when hearing the word ''risk''. | + | As previously described, Risk Treatment is the last activity in the Risk Management process. This is the part of the process where the risk is actually being treated and one tries to mitigate the potential consequences. Risk Treatment both addresses the positive and negatives risks, accordingly also referred to as ''opportunities'' and ''threats''. Opportunities are the risks that have the potential to create a positive impact on the project, program or portfolio while threats are the kind of risk that are likely to have a negative impact on the project, program or portfolio<ref name=cyber/>. The latter is often the type of risk that people think of when hearing the word ''risk''. As threats are the type of risk that can be fatal to a project, program or portfolio, the treatment of these should be prioritized first. However, opportunities should be treated at a similar level as threats as they have the potential to add the equivalent value or more to the project, program or portfolio as the threat could cost in consequences. |
[[File: risk-management-options.jpeg|thumb|700px|Figure 2: Visualization of the four different main strategies one can use to treat risks.<ref name=pb> Watt, A. (2014, August 14). 16. Risk Management Planning – Project Management – 2nd Edition. Pressbooks. Retrieved March 20, 2022, from https://opentextbc.ca/projectmanagement/chapter/chapter-16-risk-management-planning-project-management/ </ref> ]] | [[File: risk-management-options.jpeg|thumb|700px|Figure 2: Visualization of the four different main strategies one can use to treat risks.<ref name=pb> Watt, A. (2014, August 14). 16. Risk Management Planning – Project Management – 2nd Edition. Pressbooks. Retrieved March 20, 2022, from https://opentextbc.ca/projectmanagement/chapter/chapter-16-risk-management-planning-project-management/ </ref> ]] | ||
| Line 42: | Line 43: | ||
* '''Risk Transfer''' | * '''Risk Transfer''' | ||
| + | Selecting the strategies can be done by either combining the different options or by solely using one of them. Choosing the most appropriate strategies involve comparing the potential beneficial outcome, derived in relation to the accomplishment of the defined objectives against the monetary cost, the disadvantages of implementation and the effort put into it <ref name=DS/ISO31000/>. The four main strategies are seen expanded below, as well as how the different strategies should be selected. Also, a visualization of the four options can be seen on figure 2. | ||
| − | |||
| − | + | === Risk Acceptance === | |
| − | + | ||
| − | + | ||
| − | == Risk Acceptance == | + | |
Implementing a treatment always carries a cost to some degree. The cost will often be a direct monetary cost, but can also be an indirect cost shown in for example reduced flexibility in the project, program or portfolio. Therefore, it is necessary to weigh the cost of implementing a treatment up against the benefits of doing so. When choosing to accept a risk, no specific actions are taken to mitigate or provoke the risk, depending on whether it is an opportunity or a threat. The acceptance can be chosen as a strategy because the potential treatment is either too expensive, or because the negative or positive consequences from the risk are without any significant impact <ref name=cyber/>. | Implementing a treatment always carries a cost to some degree. The cost will often be a direct monetary cost, but can also be an indirect cost shown in for example reduced flexibility in the project, program or portfolio. Therefore, it is necessary to weigh the cost of implementing a treatment up against the benefits of doing so. When choosing to accept a risk, no specific actions are taken to mitigate or provoke the risk, depending on whether it is an opportunity or a threat. The acceptance can be chosen as a strategy because the potential treatment is either too expensive, or because the negative or positive consequences from the risk are without any significant impact <ref name=cyber/>. | ||
| − | == Risk Avoidance == | + | === Risk Avoidance === |
When talking about threats, risk avoidance can be done in to ways. Either, the risk is fully eliminated and thereby avoided and removed from the project, program or portfolio. This means that the project, program or portfolio does not need to change its parameters and scope to steer away from the risk, but rather uses resources on eliminating the risk. <ref name=prmf> Damnjanovic, I., & Reinschmidt, K. (2019). Data Analytics for Engineering and Construction Project Risk Management (Risk, Systems and Decisions) (1st ed. 2020 ed.). Springer. https://link.springer.com/chapter/10.1007/978-3-030-14251-3_2#citeas </ref> This can also be classified as a mitigating action. Or else, the risk is avoided and is thereby still existing, but not relevant to the project, program or portfolio anymore. This is done by changing the parameters, and asking yourself the question: "How can this project, program or portfolio be redesigned so that the risk in question disappears?" <ref name=prmf/>. Potentially, it can also be chosen not to start or continue an activity that gives rise to the risk, and thereby desist from taking on the risk <ref name=DS/ISO31000/>. | When talking about threats, risk avoidance can be done in to ways. Either, the risk is fully eliminated and thereby avoided and removed from the project, program or portfolio. This means that the project, program or portfolio does not need to change its parameters and scope to steer away from the risk, but rather uses resources on eliminating the risk. <ref name=prmf> Damnjanovic, I., & Reinschmidt, K. (2019). Data Analytics for Engineering and Construction Project Risk Management (Risk, Systems and Decisions) (1st ed. 2020 ed.). Springer. https://link.springer.com/chapter/10.1007/978-3-030-14251-3_2#citeas </ref> This can also be classified as a mitigating action. Or else, the risk is avoided and is thereby still existing, but not relevant to the project, program or portfolio anymore. This is done by changing the parameters, and asking yourself the question: "How can this project, program or portfolio be redesigned so that the risk in question disappears?" <ref name=prmf/>. Potentially, it can also be chosen not to start or continue an activity that gives rise to the risk, and thereby desist from taking on the risk <ref name=DS/ISO31000/>. | ||
<br /> | <br /> | ||
When avoiding a known risk, it is important that one is aware of not taking on even greater risks in the process that could result in more severe consequences. | When avoiding a known risk, it is important that one is aware of not taking on even greater risks in the process that could result in more severe consequences. | ||
<br /> | <br /> | ||
| − | Risk avoidance within opportunities are different, as it most often does not make sense to avoid an opportunity. One would rather seek to meet the risk, and the corresponding action would therefore be Risk Pursuit. Risk pursuit can be done by actively pursuing or continuing the activity that has been assed to cause a positive impact, by manipulating possible positive consequences to maximize estimated gains or by increasing the general likelihood of the risk to elevate positive outcomes <ref name=rt_enisa/>. | + | Risk avoidance within opportunities are different, as it most often does not make sense to avoid an opportunity. One would rather seek to meet the risk, and the corresponding action would therefore be Risk Pursuit. Risk pursuit can be done by actively pursuing or continuing the activity that has been assed to cause a positive impact, by manipulating possible positive consequences to maximize estimated gains or by increasing the general likelihood of the risk to elevate positive outcomes <ref name=rt_enisa/>. |
| − | == Risk Mitigation == | + | === Risk Mitigation === |
| + | Active actions can be taken to reduce or mitigate a risk. This approach is called risk mitigation, sometimes referred to as risk reduction<ref name=pb/>. Risk mitigation involves an investment of resources, where one through investments brings the risk to an acceptable level. Risk mitigation is the most used strategy, as all measures used to steer a risk towards an acceptable target level can be seen as a mitigating action. The type of mitigating actions can vary depending on the type of risk and project. Examples on mitigating actions are <ref name=pb/>: | ||
| + | * Hire in technical experts to review technical documentations and calculations that are a potential risk if not being exact | ||
| + | * Freeze a currency contractually to avoid exchange rate fluctuations in the project, program or portfolio | ||
| + | * Ensure that key personnel and executives are using different transport vessels, to minimize the amount of lost personnel in an accident | ||
| − | == Risk Transfer == | + | === Risk Transfer === |
Risk transfer is the action where the risk owner transfers the risk (typically a threat) to other parties, by paying the other parti a fee for taking on the risk.<ref name=prmf/>. The transfer can be compared to a marketplace, where the risk owner wish to sell some ''goods'' (in this case ''bads'' as they are threats), but rather than receiving money for the transfer, the risk owner accompanies the transferred risk with money or other considerations that the buyer would then receive<ref name=prmf/>. The risk transfer can be done both internally and externally in the project, program or portfolio, but most often it is done through an external transfer to a contractor or similar. The contractor may then seek to transfer the risk on to sub-contractors. | Risk transfer is the action where the risk owner transfers the risk (typically a threat) to other parties, by paying the other parti a fee for taking on the risk.<ref name=prmf/>. The transfer can be compared to a marketplace, where the risk owner wish to sell some ''goods'' (in this case ''bads'' as they are threats), but rather than receiving money for the transfer, the risk owner accompanies the transferred risk with money or other considerations that the buyer would then receive<ref name=prmf/>. The risk transfer can be done both internally and externally in the project, program or portfolio, but most often it is done through an external transfer to a contractor or similar. The contractor may then seek to transfer the risk on to sub-contractors. | ||
<br /> | <br /> | ||
| − | Risk transfer can also be done through ''insurance''. Not all risks can be insured, but choosing insurance as an option spreads out the risk and provides some safety to the risk owner knowing that a worst case scenario can be afforded. Also, from an economical point of view, it can be beneficial to fix a risk cost as it eliminates the economical cost from a potential | + | Risk transfer can also be done through ''insurance''. Not all risks can be insured, but choosing insurance as an option spreads out the risk and provides some safety to the risk owner knowing that a worst case scenario can be afforded. Also, from an economical point of view, it can be beneficial to fix a risk cost as it eliminates the economical cost from a potential disruption the risk could cause, which in the end could blow the budget and thereby be a showstopper for the project, program or portfolio. |
<br /> | <br /> | ||
Insurance is solely based on statistics, hence it can be difficult to insure new and unknown risks as the insurer will need to have enough data to know that they will statistically profit from the insurance in the long term. Insurance is therefore often seen in construction projects where data is easy available. Like risk transfer to contractors, an insurer can also choose to sell out parts of the insurance to sub-insurers to split out his own risk and carry the risk at a lower premium<ref name=prmf/>. | Insurance is solely based on statistics, hence it can be difficult to insure new and unknown risks as the insurer will need to have enough data to know that they will statistically profit from the insurance in the long term. Insurance is therefore often seen in construction projects where data is easy available. Like risk transfer to contractors, an insurer can also choose to sell out parts of the insurance to sub-insurers to split out his own risk and carry the risk at a lower premium<ref name=prmf/>. | ||
| Line 69: | Line 71: | ||
No matter what kind of risk transfer is chosen, it is important that all parts of the transfer fully understands the risk and the rewards. If the risk owner transfers a threat to another part and it turns out that the other part is not capable of handling the threat, the owner will be left with the original risk himself, not being able to afford a sufficient treatment. Likewise, if the risk owner transfers a threat that he believes is of great risk, but it turns out that it is not, the owner could have saved a potential high premium by keeping the risk internally<ref name=prmf/>. | No matter what kind of risk transfer is chosen, it is important that all parts of the transfer fully understands the risk and the rewards. If the risk owner transfers a threat to another part and it turns out that the other part is not capable of handling the threat, the owner will be left with the original risk himself, not being able to afford a sufficient treatment. Likewise, if the risk owner transfers a threat that he believes is of great risk, but it turns out that it is not, the owner could have saved a potential high premium by keeping the risk internally<ref name=prmf/>. | ||
<br /> | <br /> | ||
| − | If the risk is an opportunity, it can still be beneficial to transfer or share the risk with other stakeholders if they can either increase the likelihood of the opportunity happening or benefit from the opportunity happening themselves, increasing their motivation to provoke the risk<ref name=rt_enisa/>. | + | If the risk is an opportunity, it can still be beneficial to transfer or share the risk with other stakeholders if they can either increase the likelihood of the opportunity happening or benefit from the opportunity happening themselves, increasing their motivation to provoke the risk<ref name=rt_enisa/>. |
| − | == Selecting treatment options == | + | === Selecting treatment options === |
| + | As mentioned in the abstract, the selection of the different treatment options should be done from a cost-benefit point of view. The cost of implementing the treatment should be held up against to potential benefits it would generate, and an assessment on each treatment should be made to ensure the benefits outweighs the cost<ref name=rehacek> Rehacek, P. (2017). Risk management standards for project management. International Journal of Advanced and Applied Sciences, 1–13. http://www.science-gate.com/IJAAS/V4I6/Rehacek.html </ref>. The selection should however take more than only financial cost into account, as obligations, stakeholder views and other commitments should be considered as well. Furthermore, the selection of treatments should be made in accordance with the objectives of the project, program or portfolio and with reservations to available resources<ref name=rehacek/>. | ||
| + | Once the treatment options have been selected, they should be documented and communicated to relevant stakeholders. It should also be ensured, that any new risks raised by the treatment options are identified and managed and that they lie within an acceptable level. All treatments should be assigned to an owner to ensure they are acted and followed up on<ref name=PMI_PPP> Project Management Institute, Inc. (PMI). (2019). Standard for Risk Management in Portfolios, Programs, and Projects. Project Management Institute, Inc. (PMI). Retrieved from | ||
| + | https://app.knovel.com/hotlink/toc/id:kpSRMPPP01/standard-risk-management/standard-risk-management </ref>. | ||
| + | If no treatment options are selected, the risk is still to be kept under review and continuously recorded. | ||
| + | == Application == | ||
| + | Once the risk assessment has been done and appropriate treatment strategies has been chosen for all identified risks, the implementation and application of the treatments can be done. This is done through ''Treatment Plans''. | ||
| − | <ref name= | + | === Development and approval of Treatment Plans === |
| − | + | Treatment plans formalizes the chosen treatment strategies and they are the tool that ensures the risk are acted upon through treatments. The plan describes how the options should be implemented and outlines who is responsible of doing so. The plans should be clear, concise and accurate to eliminate any misunderstandings, and should as a minimum include <ref name=rt_enisa/> <ref name=DS/ISO31000/>: | |
| + | * Prioritized (can be done through risk scoring) overview of included risks | ||
| + | * Proposed treatment actions and strategies | ||
| + | * Time and date on when actions are expected to be completed | ||
| + | * Designation of responsible persons for all actions, including their role in that specific action. If possible, a RACI chart can be used | ||
| + | * Performance indicators that quantifies the effect of the treatments | ||
| + | * Estimated resource requirement to each action | ||
| + | * Information on how treatments will be reported, monitored and followed up on | ||
| + | * Information on who is responsible and accountable for implementation and approval | ||
| − | = | + | The treatment plan should be developed in such way that it can be shared with both internal stakeholders and potential external contractors and sub contractors. Once developed, the plan should be distributed and communicated to relevant parts to be able to obtain approval on it<ref name=rt_enisa/>. The more influence other stakeholders can have on the plan, the more commitment, understanding, and willingness to implement the treatments they will have. |
| − | + | <br/ > | |
| − | + | <br/ > | |
| − | + | The initial approval from relevant stakeholders is necessary before the plan can be approved by top management. The support of top management is crucial as they are the sponsors of the plan. Top management are to approve the plan before it can be implemented and they should be kept updated and informed about the plan at all times<ref name=rt_enisa/>. | |
| − | + | === Implementation of Treatment plans === | |
| − | + | Once the treatment plan has been approved by top management, it can be implemented in the project, program or portfolio. | |
| − | + | To obtain most efficiency of the treatments, the treatment plan should be an integrated part of the risk management process used<ref name=DS/ISO31000/>. If possible, the plan should also be an integrated part of other plans and processes within the project, program or portfolio such as business continuity, audit, asset management, human resource, investment and project management, and fraud control<ref name=rt_enisa/>. Hence, the implementation of the plan is done through integration into existing processes and by communicating and notifying relevant stakeholders of the existence of the plan. | |
| − | + | When the plan has been integrated into existing processes, the plan is an active asset of the risk management process in the project, program or portfolio. | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
= Limitations = | = Limitations = | ||
| − | |||
| − | |||
| − | |||
=== Limitations to the risk identification and the cost of treatment === | === Limitations to the risk identification and the cost of treatment === | ||
| − | Firstly when talking about risks, there will always be the limitation that one is simply not capable of identifying every risk related to a project, program or portfolio as there will be unknowns that | + | Firstly when talking about risks, there will always be the limitation that one is simply not capable of identifying every risk related to a project, program or portfolio as there will be unknowns that one is still not aware of. It could however be argued, that most often risk assessments will identify the most important risks, and thereby be able to mitigate the risks that are a threat to the project, program or portfolio. Also, if one were able to identify all risks, there would still be a limitation to the treatment. Choosing the kind of treatments one wish to implement can be done freely, but there will be a cost related to this treatment. The cost will be a limiting factor, as there will be a budget in where the cost of the treatment will need to stay. Therefore, it is not possible to choose exhausting treatments for all risks which limits one in the possibility of treating the risks. |
| − | Secondly, risks | + | Secondly, risks are generally based on previous experience or historical data. This works great in larger organizations where the risk exposure stays within the same scope over time, where you have a great amount of data and where you have several years of experience in the working field. But in especially projects where time and experience are a limited factor, this can result in difficulties identifying all relevant risks. There is not much, if any, data to rely on as projects are different from one another. A consequence of this is that the related risks will need to be identified from experience, and this is very much dependent on the people working on the project. If they do not have much experience to rely on, the project will be exposed to an overall greater risk than if people in the project did have a lot of experience. Furthermore, as projects are time limited and are not in an ongoing development like an organization, there is no previous experience from an exactly similar project to base the risk assessment on. |
| + | <br/ > | ||
| + | Looking at programs and portfolios, it will often be easier to gather data and relevant experience to base the risk assessment on. Here, there is no settled time limit and one will be able to use the experience from different projects within the programs and portfolios. This means treatments can be implemented and improved over time, optimizing the cost and resources used on the treatments. | ||
| − | + | === Limitations of treatment plans === | |
| − | + | As the treatment plan is a product of the chosen treatment strategies, it cannot be developed until all treatments have been identified. Also, the plan needs to be approved and implemented before it has any effect. The process of doing so takes time, and in projects with a short lifetime it can be difficult to develop, obtain approval on and implement the plan in a sufficient short period for the plan to be able to add value and reduce risks from start to end in the project. Parts of this can be mitigated by using experienced personnel and by having templates in place for all sections of the plan. | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
= Annotated bibliography = | = Annotated bibliography = | ||
| − | + | '''1: International Organization for Standardization (2018), DS/ISO 31000:2018, Risk management - Guidelines. Retrieved March 23, 2022 from:''' https://sd.ds.dk/Viewer?ProjectNr=M296412&Status=60.60&Inline=true&Page=1&VariantID=41 | |
| − | + | ::- ''The DS ISO 31000:2018 is a risk management standard that provides a general overview of what risk management is, including risk treatment and its location in the risk management process.'' | |
| − | + | '''2: Risk Treatment. (2021, June). ENISA, European Union Agency for Cybersecurity. Retrieved March 19, 2022, from:''' https://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/risk-management-inventory/rm-process/risk-treatment | |
| − | ''''' | + | ::- ''The ENISA webpage on Risk Treatment is a well explained summary of the whole risk treatment topic, including an explanation of treatment options and treatment plans.'' |
| − | + | '''3: Refsdal, A., Solhaug, B., & Stølen, K. (2015). Cyber-Risk Management (SpringerBriefs in Computer Science) (1st ed. 2015 ed.). Springer.''' | |
| − | ''' | + | ::- ''The Cyber-Risk Management book gives a thorough description on how to identify treatment options together with an in-depth explanation on the risk acceptance option. Even though the book is focused on Cyber-Risk, most can be used directly on other risk treatment processes also.'' |
| + | '''4: Rehacek, P. (2017). Risk management standards for project management. International Journal of Advanced and Applied Sciences, 1–13. Retrieved March 9, 2022 from:''' http://www.science-gate.com/IJAAS/V4I6/Rehacek.html | ||
| + | ::- ''P. Rehacek's article is a relatively short but comprehensive text that gives the reader a full introduction to the risk management topic based on different ISO standards. The article does however communicate the information in an easier understandable way, and visualizes well how risk treatment is part of the risk management process.'' | ||
= References = | = References = | ||
<references/> | <references/> | ||
Latest revision as of 20:30, 27 March 2022
By: William Taul Madsen
Contents |
[edit] Abstract
In a project, a program, or a portfolio there will always be a number of activities. All these activities will involve risk to some degree – either as a threat or an opportunity. If risks are not managed in the project, program, or portfolio it will be difficult to accomplish success. Therefore, it is important for the project, program, or portfolio leader to manage these risks by identifying them, evaluate them and treat them. The latter will be the focus of this article.
Risk Treatment is the discipline within Risk Management that takes place once a risk has been identified and assessed. Here, appropriate measures are put in place to mitigate and reduce all unacceptable risks to steer them towards an acceptable target level[1]. The identification of the treatment measures should be done from a cost benefit point of view, analysing the cost of treating the risk up against the potential benefits[2]. Furthermore, as time and resource are often a limited factor, the identification and treatment should be focused on the most important risks identified from the preliminary evaluation phase. Risk Treatment is mainly split into four categories, namely risk avoidance, risk sharing, risk mitigation and risk acceptance. Risk avoidance is the option where one simply avoids the underlying activity that causes the potential risk. Risk transfer (also known as risk sharing) is done by transferring either fully or parts of the risk to other stakeholders e.g., by insurance or by outsourcing the related activities externally. Risk mitigation is done by removing sources of threats, reducing or removing the severity of vulnerabilities and by generally reducing the likelihood of threats through mitigation. Lastly, risk acceptance is the category where the risk is accepted, due to either an acceptable threat level or a too costly treatment given the alternative options. [3] Once appropriate treatment measures have been selected, an action plan should be developed to 1) ensure that the chosen treatment options are communicated and 2) to ensure the chosen measures are implemented and acted on.[4] The action plan should be approved and shared with top management and internal and external stakeholders.
[edit] Big Idea
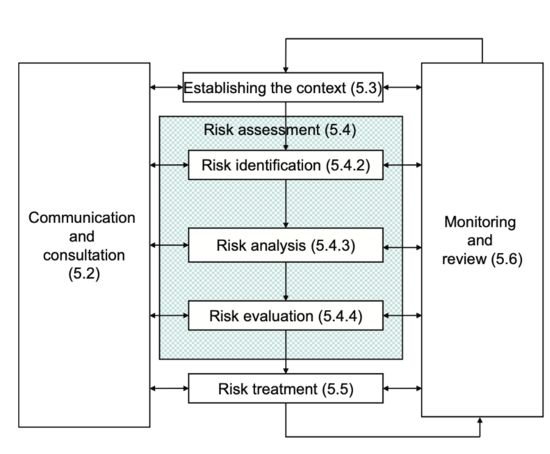
To understand risk treatment, it is first necessary to understand what Risk Management is and where in the Risk Management process the treatment occurs. In the ISO 31000 standard, Risk Management is defined as: “Coordinated activities to direct and control an organization with regard to risk” [5] This means that Risk Management controls several different activities that in combination with each other seeks to protect an organization towards risks. The purpose of risk management is to increase the probability of achieving the main goals and objectives of the project, program, or portfolio. This is done through the Risk Management Process as seen illustrated on figure 1.
First, the context of the project, program or portfolio needs to be established. This is done by articulating objectives, defining the parameters that needs to be considered, both internally and externally, and setting the overall scope of the project, program or portfolio. Secondly, the Risk Assessment phase should be initiated. This phase consists of three steps.
First step is the Risk Identification phase. Here, a comprehensive list of risks related to the project, program or portfolio is made which creates the foundation for the risk analysis. In the risk analysis, all risks from the identification phase are understood by considering their causes and sources, their potential consequences, and the likelihood of occurrence [5].
The risks are then evaluated based on the analysis. This creates a benchmark for the decision making where risks are to be prioritized, leading the risk management process into the final phase, Risk Treatment. This topic will be expanded further in the following section.
[edit] Risk Treatment
As previously described, Risk Treatment is the last activity in the Risk Management process. This is the part of the process where the risk is actually being treated and one tries to mitigate the potential consequences. Risk Treatment both addresses the positive and negatives risks, accordingly also referred to as opportunities and threats. Opportunities are the risks that have the potential to create a positive impact on the project, program or portfolio while threats are the kind of risk that are likely to have a negative impact on the project, program or portfolio[2]. The latter is often the type of risk that people think of when hearing the word risk. As threats are the type of risk that can be fatal to a project, program or portfolio, the treatment of these should be prioritized first. However, opportunities should be treated at a similar level as threats as they have the potential to add the equivalent value or more to the project, program or portfolio as the threat could cost in consequences.
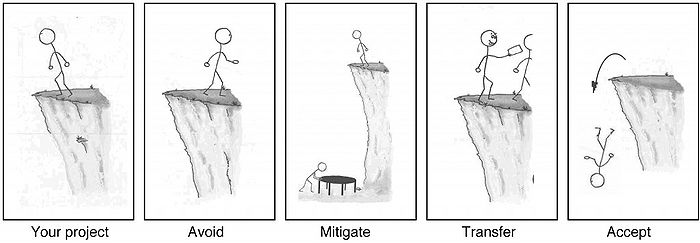
When choosing treatment options, there is mainly four different strategies that can be used [7]:
- Risk Acceptance
- Risk Avoidance
- Risk Mitigation
- Risk Transfer
Selecting the strategies can be done by either combining the different options or by solely using one of them. Choosing the most appropriate strategies involve comparing the potential beneficial outcome, derived in relation to the accomplishment of the defined objectives against the monetary cost, the disadvantages of implementation and the effort put into it [3]. The four main strategies are seen expanded below, as well as how the different strategies should be selected. Also, a visualization of the four options can be seen on figure 2.
[edit] Risk Acceptance
Implementing a treatment always carries a cost to some degree. The cost will often be a direct monetary cost, but can also be an indirect cost shown in for example reduced flexibility in the project, program or portfolio. Therefore, it is necessary to weigh the cost of implementing a treatment up against the benefits of doing so. When choosing to accept a risk, no specific actions are taken to mitigate or provoke the risk, depending on whether it is an opportunity or a threat. The acceptance can be chosen as a strategy because the potential treatment is either too expensive, or because the negative or positive consequences from the risk are without any significant impact [2].
[edit] Risk Avoidance
When talking about threats, risk avoidance can be done in to ways. Either, the risk is fully eliminated and thereby avoided and removed from the project, program or portfolio. This means that the project, program or portfolio does not need to change its parameters and scope to steer away from the risk, but rather uses resources on eliminating the risk. [8] This can also be classified as a mitigating action. Or else, the risk is avoided and is thereby still existing, but not relevant to the project, program or portfolio anymore. This is done by changing the parameters, and asking yourself the question: "How can this project, program or portfolio be redesigned so that the risk in question disappears?" [8]. Potentially, it can also be chosen not to start or continue an activity that gives rise to the risk, and thereby desist from taking on the risk [3].
When avoiding a known risk, it is important that one is aware of not taking on even greater risks in the process that could result in more severe consequences.
Risk avoidance within opportunities are different, as it most often does not make sense to avoid an opportunity. One would rather seek to meet the risk, and the corresponding action would therefore be Risk Pursuit. Risk pursuit can be done by actively pursuing or continuing the activity that has been assed to cause a positive impact, by manipulating possible positive consequences to maximize estimated gains or by increasing the general likelihood of the risk to elevate positive outcomes [4].
[edit] Risk Mitigation
Active actions can be taken to reduce or mitigate a risk. This approach is called risk mitigation, sometimes referred to as risk reduction[6]. Risk mitigation involves an investment of resources, where one through investments brings the risk to an acceptable level. Risk mitigation is the most used strategy, as all measures used to steer a risk towards an acceptable target level can be seen as a mitigating action. The type of mitigating actions can vary depending on the type of risk and project. Examples on mitigating actions are [6]:
- Hire in technical experts to review technical documentations and calculations that are a potential risk if not being exact
- Freeze a currency contractually to avoid exchange rate fluctuations in the project, program or portfolio
- Ensure that key personnel and executives are using different transport vessels, to minimize the amount of lost personnel in an accident
[edit] Risk Transfer
Risk transfer is the action where the risk owner transfers the risk (typically a threat) to other parties, by paying the other parti a fee for taking on the risk.[8]. The transfer can be compared to a marketplace, where the risk owner wish to sell some goods (in this case bads as they are threats), but rather than receiving money for the transfer, the risk owner accompanies the transferred risk with money or other considerations that the buyer would then receive[8]. The risk transfer can be done both internally and externally in the project, program or portfolio, but most often it is done through an external transfer to a contractor or similar. The contractor may then seek to transfer the risk on to sub-contractors.
Risk transfer can also be done through insurance. Not all risks can be insured, but choosing insurance as an option spreads out the risk and provides some safety to the risk owner knowing that a worst case scenario can be afforded. Also, from an economical point of view, it can be beneficial to fix a risk cost as it eliminates the economical cost from a potential disruption the risk could cause, which in the end could blow the budget and thereby be a showstopper for the project, program or portfolio.
Insurance is solely based on statistics, hence it can be difficult to insure new and unknown risks as the insurer will need to have enough data to know that they will statistically profit from the insurance in the long term. Insurance is therefore often seen in construction projects where data is easy available. Like risk transfer to contractors, an insurer can also choose to sell out parts of the insurance to sub-insurers to split out his own risk and carry the risk at a lower premium[8].
No matter what kind of risk transfer is chosen, it is important that all parts of the transfer fully understands the risk and the rewards. If the risk owner transfers a threat to another part and it turns out that the other part is not capable of handling the threat, the owner will be left with the original risk himself, not being able to afford a sufficient treatment. Likewise, if the risk owner transfers a threat that he believes is of great risk, but it turns out that it is not, the owner could have saved a potential high premium by keeping the risk internally[8].
If the risk is an opportunity, it can still be beneficial to transfer or share the risk with other stakeholders if they can either increase the likelihood of the opportunity happening or benefit from the opportunity happening themselves, increasing their motivation to provoke the risk[4].
[edit] Selecting treatment options
As mentioned in the abstract, the selection of the different treatment options should be done from a cost-benefit point of view. The cost of implementing the treatment should be held up against to potential benefits it would generate, and an assessment on each treatment should be made to ensure the benefits outweighs the cost[9]. The selection should however take more than only financial cost into account, as obligations, stakeholder views and other commitments should be considered as well. Furthermore, the selection of treatments should be made in accordance with the objectives of the project, program or portfolio and with reservations to available resources[9]. Once the treatment options have been selected, they should be documented and communicated to relevant stakeholders. It should also be ensured, that any new risks raised by the treatment options are identified and managed and that they lie within an acceptable level. All treatments should be assigned to an owner to ensure they are acted and followed up on[10]. If no treatment options are selected, the risk is still to be kept under review and continuously recorded.
[edit] Application
Once the risk assessment has been done and appropriate treatment strategies has been chosen for all identified risks, the implementation and application of the treatments can be done. This is done through Treatment Plans.
[edit] Development and approval of Treatment Plans
Treatment plans formalizes the chosen treatment strategies and they are the tool that ensures the risk are acted upon through treatments. The plan describes how the options should be implemented and outlines who is responsible of doing so. The plans should be clear, concise and accurate to eliminate any misunderstandings, and should as a minimum include [4] [3]:
- Prioritized (can be done through risk scoring) overview of included risks
- Proposed treatment actions and strategies
- Time and date on when actions are expected to be completed
- Designation of responsible persons for all actions, including their role in that specific action. If possible, a RACI chart can be used
- Performance indicators that quantifies the effect of the treatments
- Estimated resource requirement to each action
- Information on how treatments will be reported, monitored and followed up on
- Information on who is responsible and accountable for implementation and approval
The treatment plan should be developed in such way that it can be shared with both internal stakeholders and potential external contractors and sub contractors. Once developed, the plan should be distributed and communicated to relevant parts to be able to obtain approval on it[4]. The more influence other stakeholders can have on the plan, the more commitment, understanding, and willingness to implement the treatments they will have.
The initial approval from relevant stakeholders is necessary before the plan can be approved by top management. The support of top management is crucial as they are the sponsors of the plan. Top management are to approve the plan before it can be implemented and they should be kept updated and informed about the plan at all times[4].
[edit] Implementation of Treatment plans
Once the treatment plan has been approved by top management, it can be implemented in the project, program or portfolio. To obtain most efficiency of the treatments, the treatment plan should be an integrated part of the risk management process used[3]. If possible, the plan should also be an integrated part of other plans and processes within the project, program or portfolio such as business continuity, audit, asset management, human resource, investment and project management, and fraud control[4]. Hence, the implementation of the plan is done through integration into existing processes and by communicating and notifying relevant stakeholders of the existence of the plan.
When the plan has been integrated into existing processes, the plan is an active asset of the risk management process in the project, program or portfolio.
[edit] Limitations
[edit] Limitations to the risk identification and the cost of treatment
Firstly when talking about risks, there will always be the limitation that one is simply not capable of identifying every risk related to a project, program or portfolio as there will be unknowns that one is still not aware of. It could however be argued, that most often risk assessments will identify the most important risks, and thereby be able to mitigate the risks that are a threat to the project, program or portfolio. Also, if one were able to identify all risks, there would still be a limitation to the treatment. Choosing the kind of treatments one wish to implement can be done freely, but there will be a cost related to this treatment. The cost will be a limiting factor, as there will be a budget in where the cost of the treatment will need to stay. Therefore, it is not possible to choose exhausting treatments for all risks which limits one in the possibility of treating the risks.
Secondly, risks are generally based on previous experience or historical data. This works great in larger organizations where the risk exposure stays within the same scope over time, where you have a great amount of data and where you have several years of experience in the working field. But in especially projects where time and experience are a limited factor, this can result in difficulties identifying all relevant risks. There is not much, if any, data to rely on as projects are different from one another. A consequence of this is that the related risks will need to be identified from experience, and this is very much dependent on the people working on the project. If they do not have much experience to rely on, the project will be exposed to an overall greater risk than if people in the project did have a lot of experience. Furthermore, as projects are time limited and are not in an ongoing development like an organization, there is no previous experience from an exactly similar project to base the risk assessment on.
Looking at programs and portfolios, it will often be easier to gather data and relevant experience to base the risk assessment on. Here, there is no settled time limit and one will be able to use the experience from different projects within the programs and portfolios. This means treatments can be implemented and improved over time, optimizing the cost and resources used on the treatments.
[edit] Limitations of treatment plans
As the treatment plan is a product of the chosen treatment strategies, it cannot be developed until all treatments have been identified. Also, the plan needs to be approved and implemented before it has any effect. The process of doing so takes time, and in projects with a short lifetime it can be difficult to develop, obtain approval on and implement the plan in a sufficient short period for the plan to be able to add value and reduce risks from start to end in the project. Parts of this can be mitigated by using experienced personnel and by having templates in place for all sections of the plan.
[edit] Annotated bibliography
1: International Organization for Standardization (2018), DS/ISO 31000:2018, Risk management - Guidelines. Retrieved March 23, 2022 from: https://sd.ds.dk/Viewer?ProjectNr=M296412&Status=60.60&Inline=true&Page=1&VariantID=41
- - The DS ISO 31000:2018 is a risk management standard that provides a general overview of what risk management is, including risk treatment and its location in the risk management process.
2: Risk Treatment. (2021, June). ENISA, European Union Agency for Cybersecurity. Retrieved March 19, 2022, from: https://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/risk-management-inventory/rm-process/risk-treatment
- - The ENISA webpage on Risk Treatment is a well explained summary of the whole risk treatment topic, including an explanation of treatment options and treatment plans.
3: Refsdal, A., Solhaug, B., & Stølen, K. (2015). Cyber-Risk Management (SpringerBriefs in Computer Science) (1st ed. 2015 ed.). Springer.
- - The Cyber-Risk Management book gives a thorough description on how to identify treatment options together with an in-depth explanation on the risk acceptance option. Even though the book is focused on Cyber-Risk, most can be used directly on other risk treatment processes also.
4: Rehacek, P. (2017). Risk management standards for project management. International Journal of Advanced and Applied Sciences, 1–13. Retrieved March 9, 2022 from: http://www.science-gate.com/IJAAS/V4I6/Rehacek.html
- - P. Rehacek's article is a relatively short but comprehensive text that gives the reader a full introduction to the risk management topic based on different ISO standards. The article does however communicate the information in an easier understandable way, and visualizes well how risk treatment is part of the risk management process.
[edit] References
- ↑ Danish Standards Association (2019), DS/EN IEC 31010:2019, Risk management - Risk assessment techniques, Retrieved March 27 from https://sd.ds.dk/Viewer?ProjectNr=M321462&Status=60.60
- ↑ 2.0 2.1 2.2 Refsdal, A., Solhaug, B., & Stølen, K. (2015). Cyber-Risk Management (SpringerBriefs in Computer Science) (1st ed. 2015 ed.). Springer.
- ↑ 3.0 3.1 3.2 3.3 3.4 International Organization for Standardization (2018), DS/ISO 31000:2018, Risk management - Guidelines, Retrieved from https://sd.ds.dk/Viewer?ProjectNr=M296412&Status=60.60&Inline=true&Page=1&VariantID=41
- ↑ 4.0 4.1 4.2 4.3 4.4 4.5 4.6 Risk Treatment. (2021, June). ENISA, European Union Agency for Cybersecurity. Retrieved March 19, 2022, from: https://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/risk-management-inventory/rm-process/risk-treatment
- ↑ 5.0 5.1 5.2 International Organization for Standardization (2009), DS/ISO 31000:2009, Risikoledelse - Principper og vejledning, Risk management - Principles and guidelines, Retrieved from https://sd.ds.dk/Post?ProjectNr=M228821&Status=99.60
- ↑ 6.0 6.1 6.2 Watt, A. (2014, August 14). 16. Risk Management Planning – Project Management – 2nd Edition. Pressbooks. Retrieved March 20, 2022, from https://opentextbc.ca/projectmanagement/chapter/chapter-16-risk-management-planning-project-management/
- ↑ International Organization for Standardization (2020), DS/ISO 21502:2020, Project-, programme and portfolio management - Guidance on project management, Retrieved from https://sd.ds.dk/Viewer?ProjectNr=M351700&Status=60.60&Inline=true&Page=1&VariantID=
- ↑ 8.0 8.1 8.2 8.3 8.4 8.5 Damnjanovic, I., & Reinschmidt, K. (2019). Data Analytics for Engineering and Construction Project Risk Management (Risk, Systems and Decisions) (1st ed. 2020 ed.). Springer. https://link.springer.com/chapter/10.1007/978-3-030-14251-3_2#citeas
- ↑ 9.0 9.1 Rehacek, P. (2017). Risk management standards for project management. International Journal of Advanced and Applied Sciences, 1–13. http://www.science-gate.com/IJAAS/V4I6/Rehacek.html
- ↑ Project Management Institute, Inc. (PMI). (2019). Standard for Risk Management in Portfolios, Programs, and Projects. Project Management Institute, Inc. (PMI). Retrieved from https://app.knovel.com/hotlink/toc/id:kpSRMPPP01/standard-risk-management/standard-risk-management