Risk Identification
| (27 intermediate revisions by one user not shown) | |||
| Line 1: | Line 1: | ||
| + | ''Developed by Martin Tromborg Larsen'' | ||
== Introduction and relevance== | == Introduction and relevance== | ||
| − | In all areas of management and projects, it is crucial to be aware of the risks that may affect the outcome of objectives. Identifying what could go wrong, delay or even completely terminate | + | In all areas of management and projects, it is crucial to be aware of the risks that may affect the outcome, quality or completion of objectives. Identifying what could go wrong, delay or even completely terminate an objective is the initial process of risk assessment, and a part of risk management. Identification of risks is important, because once a risk has been identified, the risk can be dealt with. Non-identified risks are much more likely to have significant consequences for a project, because no action to mitigate, prevent or make a plan B can be done. By applying the correct methods, using and involving the right people, risks can be identified, and later handled in risk management. Risk identification is relevant in many different contexts, see Figure 1. This article defines risk identification and its sub-processes, outlines relevant identification methods, and suggest optimization parameters for the main process. |
| + | [[File:Brain.png|450px|right|thumb| Figure 1. Themes where being aware of risks is relevant, thus making risk identification a useful process. ]] | ||
| − | == Definitions | + | == Definitions == |
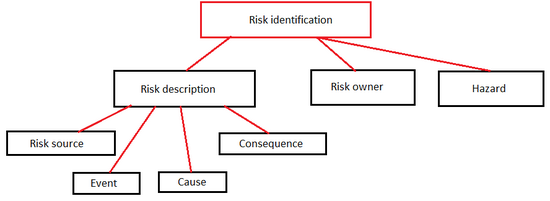
| − | Risk identification is defined as “the process of finding, recognizing and describing risks”. The goal of risk identification is to analyze what might happen, or what situations may affect outcomes or deliverables in a project. When a risk is identified, it is possible to identify any existing controls such as people, systems, design features and processes. These controls are important in the later stages of risk management, as they are the key to influence the risk. Risk identification can be | + | Risk identification is defined as “the process of finding, recognizing and describing risks” <ref>''ISO Standard 31000: Risk management - Principles and guidelines. Annotation: A complete standard for the risk management process, including risk identification. Main guideline for context of the topic of risk identification '' </ref>. The goal of risk identification is to analyze what might happen, or what situations may affect outcomes, objectives or deliverables in a project or organization. When a risk is identified, it is possible to identify any existing controls such as people, systems, design features and processes associated with the risk. These controls are important in the later stages of risk management, as they are the key to influence the risk. Risk identification is a process that can be done at any stage of a project, and can be repeated many times over its duration. It is strong in any initial phase as preparation, but when conditions change over time, so do risks. By repeating the process, the risk manager is always aware of risks, even in changed environments. The following definitions are considered relevant terms and sub-processes associated with risk identification. Their relation can be seen in Figure 2. |
| + | |||
| + | [[File:Definition.png|550px|right|thumb| Figure 2. Relation of the different terms and definitions associated with risk identification ]] | ||
=== Risk description === | === Risk description === | ||
| − | A detailed description of the identified risk. Should include its sources, events, causes and consequences, explained in the following sections. The risk description is crucial tool for managing risks, allowing the manager to get detailed information about a specific risk. | + | A detailed description of the identified risk <ref>''ISO Guide 73-2009 – Risk Management Vocabulary. Annotation: Supportive standard for both ISO 31000 and 31010. Contains detailed vocabulary for risk management, including all relevant terms for risk identification '' </ref>. Should include its sources, events, causes and consequences, explained in the following sections. The risk description is crucial tool for managing risks, allowing the manager to get detailed information about a specific risk. |
| − | === | + | === Risk source === |
| + | The element(s), which can result in a risk. The source can be a single element, or a combination of several. They can have different strength, meaning that a risk can have many sources, but some may be more dominant than others. The source may be tangible or intangible. | ||
| − | + | === Event === | |
| + | Occurrence or change of a particular set of circumstances, also known as an “incident” or “accident”. An event can have consequences, negative or positive, but an event can also be something not happening. If an event has no consequences, it can be labeled as a “near miss”, “near hit” or “close call”. Some events can trigger more than once, and have one or several causes. | ||
| − | + | === Cause === | |
| + | The reason that causes an event to happen. A cause is bound to have a risk source involved. The cause can also be characterized as an effect on a risk source, which leads to an event. | ||
| + | |||
| + | === Consequence === | ||
| + | Outcome of an event, which affect objectives. An event can have several consequences. A consequence is usually associated with something negative, but in risk management, a consequence can affect an objective in a positive or negative way. Consequences can vary from a small delay, injury of personnel or termination of the project. Some consequences are only annoying, while others are devastating. Analysis of consequences plays an important role in risk management, because it influences what risks we want to influence, and which ones we will not. In the risk description, the consequence should only be identified. | ||
| + | |||
| + | === Hazard === | ||
| + | Risk in the context of risk identification and management usually refers to a risk for the project or organization. A hazard is a risk that involves physical or mental harm of people in the project or organization. A hazard can also be a risk source, and may have additional consequences in addition to the damage on employees or stakeholders. In the risk identification process, hazards and risks should be distinguished, allowing a focus on safety. Ethically, hazards should have priority in the identification and management of risks, but that is not always the case. This may be reality in cases where hazards have little impact on objectives, and are expensive or time consuming to deal with. | ||
| − | + | === Risk owner === | |
| − | + | Person, group or entity with accountability and authority to manage and affect a risk. By identifying the risk owner, it is easier to handle the risk in later stages of risk management. Communication and cooperation can easier take place when the correct connection and responsibilities are established. | |
| − | + | ||
| − | + | == Context of risk identification == | |
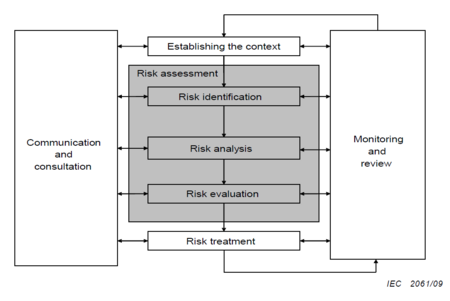
| − | + | Risk identification can be done as standalone process, but it is close to useless if it is not followed by additional risk management processes. Therefore, it is important to carry out the risk identification while being aware of its context: a part of risk management. Risk identification should be seen as the first step in risk assessment, and as part of a tool, that protects the organization against unwanted events and their negative consequences. It is also important to monitor and review the identification process, as well as using communication. The full context of risk identification in risk management can be seen in Figure 3. | |
| − | + | ||
| + | [[File:RM.png|450px|right|thumb| Figure 3. Risk management process as illustrated in the ISO standard 31000 . Shows the context risk identification should always be seen in. The blue line represents the flow of sub-processes of risk management. The blue-line loop also indicates that the process is repeatable. ]] | ||
| Line 32: | Line 44: | ||
== Risk identification methods == | == Risk identification methods == | ||
| − | Different methods for risk identification exists, each having strengths covering a certain area. The process should include as many methods as possible, to | + | Different methods for risk identification exists, each having strengths covering a certain area. The process should include as many methods as possible, to identify the most risks. The more risks associated with a project, the more methods will be necessary to cover them all. The use of a method should result in a risk or hazard description, preferably including the risk owner. However, the most important output of each method should be to confirm the existence of different risks. Once a risk has been identified, the risk description can be done. The individual methods attempts different approaches to being aware of a risk. |
| − | + | === Brainstorming === | |
| − | The most basic of methods, which has its strength as an initial method. During a brainstorm, quantity is central, and whatever risk comes to mind should be mentioned. The quality and relevance of the identified risks is not important at this stage. | + | The most basic of methods, which has its strength as an initial method, but can be used at any stage <ref> http://www.innovation-portal.info/toolkits/brainstorming/ . Annotation: Detailed guide and description for the brainstorming method. Also includes tips on how to achieve the optimal brainstorm </ref>. The concept is to generate a lot of ideas in a group, focusing on idea generation, not evaluation . A headline for the brainstorm is chosen, to define what specific area should be covered. This is important to keep the brainstorm focused. The headline could be very concrete, for instance risks associated with a certain process or activity, or very general, as all risks associated with a certain project. One can also start with a broad risk generation, and move into specific areas along the way. It is recommended to appoint a brainstorm leader, to act as a chairman, and to make sure the focus is on idea generation, not evaluation. During a brainstorm, quantity is central, and whatever risk comes to mind should be mentioned. The quality and relevance of the identified risks is not important at this stage. After a set amount of time, the idea phase closes, which should result in a large number of risks within the chosen area or subject. Now, each suggested risk can be debated, and it can be decided what risks are worth keeping for further analysis, and which should be discarded. If an identified risk is discarded, because it is concluded that it is not relevant, it will not be part of risk management later. Therefore, it should only be discarded if the identifier(s) agree, that it will be a waste of resources to handle the risk at a later stage. To avoid that important risks are removed from the list of identified risks, it is recommendable to appoint a “devils advocate”. It is the job of the devil’s advocate to defend all risks from removal from the list, with sane arguments of course. It also opens for further debate of the individual identified risk. The brainstorm excels at finding the obvious risks associated with the projects, but may lack in-depth analysis of some of the other tools.Furthermore, it is strong in high uncertainty situations, because the innovative approach forces participants to think outside the box. The brainstorm is recommendable for any risk identification process, because of the large amount of ground it covers, with minimal effort. It should be noted that the brainstorm is a qualitative method. The risk description generated by the brainstorm can be supported by quantitative initiatives after the brainstorming itself is done. |
| − | + | === Evidence based method === | |
| − | Identification of risks based on historical data and experience. The | + | Identification of risks based on historical data and experience. The method consists of finding similar organizations, projects or tasks, and review them. What went wrong and why, and what went well and why. Then relate it to risks, how they were handled and why. The method ranges from analysis of heavy empirical and statistical data, to qualitative statements and interviews. The essence is to learn from the past in any way possible, in order to improve risk identification. This method may require a lot of resources, because of the amount of potential data. It is most suited for projects which can be related to other projects, and not completely new ventures, because a certain amount of evidence is required. However, even by moving into relatively unknown territory, there will always be some aspects, organizational, technical or human, which will relate to previous experiences. A good example is the NASA space program, which constantly evaluate its own performance, especially when something goes wrong. If a risk has not been identified, but triggers an event, it results in learning and improvement. The risk will definitely be handled differently next time! The method can be carried out in a team or workgroup, but may require a lot of time and individual work. |
| − | + | === Systematic team approach === | |
| + | A team of experts follow a systematic process to identify risks by means of a structured set of prompts or questions <ref>''ISO Standard 31010: Risk Assesment Techniques. Annotation: A complete standard for the risk assessment process. Supportive standard for the ISO 31000. Goes more in depth with the content of Risk Assesment, namely risk identification, risk analysis and risk evaluation. Contains more details on risk identification than the ISO 31000.'' </ref>. The questions may be predefined from a previous, similar project or situation, or they may be unique. Often, it will be a combination. The process is much less random than the brainstorming method, and more thorough. It is especially strong for projects in which many activities and processes are repetition from previous projects. The process struggles a bit more in undefined projects, like research projects. It is much more difficult to prepare prompts and questions for something there is limited knowledge about. Overall, the selected topics for questions/prompts will have their risks covered very well. However, if some topics are not considered in the systematic team approach, they may be completely missed, because they will not be debated by the team (in this method). The method should yield a complete risk description. All aspects of risk identification should be covered in the systematic approach. | ||
| − | + | === Hazard and operability study === | |
| + | A Hazard and operability study (HAZOP) has the purpose to identify hazards. By having an isolated method for hazard identification, the risk of forgetting hazards in the risk identification process is reduced. The method is closely related to the systematic team approach, where a set of questions, guidelines or prompts are followed to identify hazards. It is also carried out in a team. The keywords are highly standardized, as almost all possible ways human damage can happen are considered. Examples of keywords could be flow, pressure, temperature, vibrations, chemical reaction and so on. The HAZOP method should be mandatory in projects and situations associated with hazards. This could be, but not limited to, construction, mining, factory, production and military. In fields with less associated hazards, for instance organizational change projects, a HAZOP will not be necessary. It should be emphasized that hazards can also be identified through other non-hazard based methods, but the strength of the HAZOP is the relentless focus on hazards. The method also promotes safety above all else, which is a good signal to send to all employees working in the project or organization. | ||
== Conditions for optimal risk identification == | == Conditions for optimal risk identification == | ||
| + | By using one or several of the suggested methods for risk identification, the process is off to a good start. Additional factors in the organization or project environment can greatly affect the outcome of the identification process. Even if the methods are used, it needs to be the right people who are using them. The most important thing to remember, is that risk identification should not be done in a vacuum. An individual can make a good, detailed and useful risk identification – but chances are that it could be greatly improved by involving more people. The process could be done alone by the project leader in a project, or a manager in an organization. That is not recommendable. An individual cannot debate with itself, and there is no chance for a second opinion. The following initiatives will boost the effectiveness and efficiency of the risk identification process. | ||
| + | |||
| + | === Use of a group === | ||
| + | The use of a group is the most important condition for optimal risk identification. By having a group, experience and opinions can be pooled together, in an effort to identify risks. It also allows the debate of the individual risk. Quantitatively, a group is more like to identify more relevant risks than an individual, assuming that the group members are qualified. The downsides to having a group are the increased amount of resources required to complete the process, and groupthink may happen <ref>Dag Ingvar Jacobsen and Jan Thorsvik, “How organizations work”. Original title, Norwegian: “Hvordan organisasjoner fungerer”. 2nd edition, 2008. Annotation: Complete book about organizations and how they work. Used in the context of groups and organizational culture, which it contains very detailed information about </ref> . Groupthink, where a desire for harmony and unity leads to dysfunctional decision making, is a threat to any group process. Groupthink, and other group-related problems, are less likely if the group is diverse. | ||
| + | |||
| + | === Diversity of the group === | ||
| + | Having a group is a good start, but what is more important is having the right people in the group. In short, the more diverse the group is, the more risk-related areas may be covered. The accumulated experience and knowledge in the group should be as big as possible. Having a lot of people with the same competences will not increase the total risk coverage of the group. The group should be diversified on the following areas: | ||
| + | |||
| + | '''Technology and knowledge:''' Especially important if there can be risks involved with the use/development of a certain technology <ref>David Davies, “Risk Identification”, Computer Law and Security Report – 1988, Volume 4, Issue 3, pp.20-22 .Annotation: A good introduction to risk identification, including examples and perspective. Also investigates what makes a good risk investigator '' </ref>. It may be completely impossible for a non-expert to predict risks in a technical unknown field | ||
| + | |||
| + | '''Culture and religion:''' Especially important for understanding the people involved and/or exposed to the risks. Risks are not necessarily considered the same in different cultures. | ||
| + | |||
| + | '''Demographic knowledge:''' If a group from Denmark is identifying risks in a construction project in Indonesia, it is important to understand the risks associated with the specific place. It can be achieved either by having people from different geographical areas in the group, or by having acquired knowledge and understanding about a specific place. | ||
| + | |||
| + | '''Different personalities:''' Having 5 middle-aged business men in suits may give fine results, but different people tend to have different opinions – and different perspective on risks. The mother of 3, the immigrant or the newly qualified engineer may give a different perspective to the identification process, which is very useful. | ||
| + | |||
| + | '''Organizational departments:''' Having only people from one department increases the likelihood of groupthink and departmental selfishness. If the group consists of people from marketing department only for instance, the group may value risk in marketing above else, which is undesirable. Having members from different departments ensures a more non-biased view on risks. | ||
| + | |||
| + | |||
| + | It should be noted that these diversities are recommendable to most groups and organizations – they are not exclusive for a group carrying out the risk identification process. Furthermore, it is not always possible to tailor the group exactly around these principles. In such a situation, it is important that the group recognizes this and asks for advice in other parts of the organization or project group. Consultants can also be used to cover areas where the group is not confident. | ||
| + | |||
| + | === Involving stakeholders === | ||
| + | Involving stakeholders in the risk identification process is highly recommended. Assuming we are identifying risks in a project, one of the most logical places to go for advice are the stakeholders <ref>Mette L. Attrup and John Ryding Olsson, “Power in Projects and Portfolios”. 2nd edition, 2008 .Annotation: Extensive book about basic project and portfolio management. Includes details about risk, uncertainty and risk analysis '' </ref>. They may have exclusive information on a certain subject, which may help to identify risks. It also gives the stakeholders the opportunity to participate, and take responsibility in the management of risks. A long, formal meeting is not required to involve stakeholders. A simple phone call or conversation about their experience on the subject may point out risks otherwise not identified by the group. Stakeholders should not only be involved the initial stages of risk identification, but also at later stages. When conditions and environments change, stakeholders remain a good source of opinions and information. It should be remembered that some stakeholders may know much more on the subject than members of the group. | ||
| − | |||
| − | |||
| − | + | == Limitations and conclusion == | |
| + | Risk identification, as a part of risk management, is a recommended process in all organizations and projects. In fact, it is recommended in all aspects of life, to be aware of what might affect our path and objectives. But risk identification should not be overdone either. There is little help in being aware of risks, if nothing is done to control them. Neither is it helpful to spend so many resources, that other vital processes and activities are unable to take place. Another trap may be to assume that risk identification, at a certain point, is complete. All risks have been found. This is simply not possible. By the nature of uncertainty, even the unthinkable happens from time to time. In addition, projects, organizations and their environments is constantly changing. New risks may arise at any time, and therefore, risk identification should be repeated. Risk identification cannot guarantee safety, because the conditions change all the time. This is something that must be fundamentally accepted, that no matter the effort, we cannot assume that everything is within our control. When risk identification is seen in the context of risk management, it is a very strong process that can decide whether objectives are achieved or not. It allows heavy influence on risks in a desired way. In conclusion, risk identification is limited by the nature of uncertainty and chance. But that is no reason not to attempt to affect the risks, because much can be achieved by doing so. | ||
| − | == | + | == References == |
| + | <references/> | ||
Latest revision as of 15:27, 18 December 2018
Developed by Martin Tromborg Larsen
Contents |
[edit] Introduction and relevance
In all areas of management and projects, it is crucial to be aware of the risks that may affect the outcome, quality or completion of objectives. Identifying what could go wrong, delay or even completely terminate an objective is the initial process of risk assessment, and a part of risk management. Identification of risks is important, because once a risk has been identified, the risk can be dealt with. Non-identified risks are much more likely to have significant consequences for a project, because no action to mitigate, prevent or make a plan B can be done. By applying the correct methods, using and involving the right people, risks can be identified, and later handled in risk management. Risk identification is relevant in many different contexts, see Figure 1. This article defines risk identification and its sub-processes, outlines relevant identification methods, and suggest optimization parameters for the main process.
[edit] Definitions
Risk identification is defined as “the process of finding, recognizing and describing risks” [1]. The goal of risk identification is to analyze what might happen, or what situations may affect outcomes, objectives or deliverables in a project or organization. When a risk is identified, it is possible to identify any existing controls such as people, systems, design features and processes associated with the risk. These controls are important in the later stages of risk management, as they are the key to influence the risk. Risk identification is a process that can be done at any stage of a project, and can be repeated many times over its duration. It is strong in any initial phase as preparation, but when conditions change over time, so do risks. By repeating the process, the risk manager is always aware of risks, even in changed environments. The following definitions are considered relevant terms and sub-processes associated with risk identification. Their relation can be seen in Figure 2.
[edit] Risk description
A detailed description of the identified risk [2]. Should include its sources, events, causes and consequences, explained in the following sections. The risk description is crucial tool for managing risks, allowing the manager to get detailed information about a specific risk.
[edit] Risk source
The element(s), which can result in a risk. The source can be a single element, or a combination of several. They can have different strength, meaning that a risk can have many sources, but some may be more dominant than others. The source may be tangible or intangible.
[edit] Event
Occurrence or change of a particular set of circumstances, also known as an “incident” or “accident”. An event can have consequences, negative or positive, but an event can also be something not happening. If an event has no consequences, it can be labeled as a “near miss”, “near hit” or “close call”. Some events can trigger more than once, and have one or several causes.
[edit] Cause
The reason that causes an event to happen. A cause is bound to have a risk source involved. The cause can also be characterized as an effect on a risk source, which leads to an event.
[edit] Consequence
Outcome of an event, which affect objectives. An event can have several consequences. A consequence is usually associated with something negative, but in risk management, a consequence can affect an objective in a positive or negative way. Consequences can vary from a small delay, injury of personnel or termination of the project. Some consequences are only annoying, while others are devastating. Analysis of consequences plays an important role in risk management, because it influences what risks we want to influence, and which ones we will not. In the risk description, the consequence should only be identified.
[edit] Hazard
Risk in the context of risk identification and management usually refers to a risk for the project or organization. A hazard is a risk that involves physical or mental harm of people in the project or organization. A hazard can also be a risk source, and may have additional consequences in addition to the damage on employees or stakeholders. In the risk identification process, hazards and risks should be distinguished, allowing a focus on safety. Ethically, hazards should have priority in the identification and management of risks, but that is not always the case. This may be reality in cases where hazards have little impact on objectives, and are expensive or time consuming to deal with.
[edit] Risk owner
Person, group or entity with accountability and authority to manage and affect a risk. By identifying the risk owner, it is easier to handle the risk in later stages of risk management. Communication and cooperation can easier take place when the correct connection and responsibilities are established.
[edit] Context of risk identification
Risk identification can be done as standalone process, but it is close to useless if it is not followed by additional risk management processes. Therefore, it is important to carry out the risk identification while being aware of its context: a part of risk management. Risk identification should be seen as the first step in risk assessment, and as part of a tool, that protects the organization against unwanted events and their negative consequences. It is also important to monitor and review the identification process, as well as using communication. The full context of risk identification in risk management can be seen in Figure 3.
[edit] Application of risk identification
Risk identification should be used when a project or organization faces unknown entities in their operations. It can be argued, that this is always the case, because there is a risk involved in being active in our society. It is always recommendable to be aware of risks, and try to identify them. But to initiate a complete risk identification, followed by risk management, is only recommendable for operations with a certain degree of uncertainty. Projects are a good example, as they are partly defined by their uncertainty. The scope should also be considered. Short, uncomplicated projects may have less need for a risk identification process, while it would be organizational suicide to do a mega-project without risk identification. Especially in smaller projects, it will come down to a matter of resources and prioritizing. Risk identification should never be completely ignored, but can have a lower priority in small-scope operations and projects.
[edit] Risk identification methods
Different methods for risk identification exists, each having strengths covering a certain area. The process should include as many methods as possible, to identify the most risks. The more risks associated with a project, the more methods will be necessary to cover them all. The use of a method should result in a risk or hazard description, preferably including the risk owner. However, the most important output of each method should be to confirm the existence of different risks. Once a risk has been identified, the risk description can be done. The individual methods attempts different approaches to being aware of a risk.
[edit] Brainstorming
The most basic of methods, which has its strength as an initial method, but can be used at any stage [3]. The concept is to generate a lot of ideas in a group, focusing on idea generation, not evaluation . A headline for the brainstorm is chosen, to define what specific area should be covered. This is important to keep the brainstorm focused. The headline could be very concrete, for instance risks associated with a certain process or activity, or very general, as all risks associated with a certain project. One can also start with a broad risk generation, and move into specific areas along the way. It is recommended to appoint a brainstorm leader, to act as a chairman, and to make sure the focus is on idea generation, not evaluation. During a brainstorm, quantity is central, and whatever risk comes to mind should be mentioned. The quality and relevance of the identified risks is not important at this stage. After a set amount of time, the idea phase closes, which should result in a large number of risks within the chosen area or subject. Now, each suggested risk can be debated, and it can be decided what risks are worth keeping for further analysis, and which should be discarded. If an identified risk is discarded, because it is concluded that it is not relevant, it will not be part of risk management later. Therefore, it should only be discarded if the identifier(s) agree, that it will be a waste of resources to handle the risk at a later stage. To avoid that important risks are removed from the list of identified risks, it is recommendable to appoint a “devils advocate”. It is the job of the devil’s advocate to defend all risks from removal from the list, with sane arguments of course. It also opens for further debate of the individual identified risk. The brainstorm excels at finding the obvious risks associated with the projects, but may lack in-depth analysis of some of the other tools.Furthermore, it is strong in high uncertainty situations, because the innovative approach forces participants to think outside the box. The brainstorm is recommendable for any risk identification process, because of the large amount of ground it covers, with minimal effort. It should be noted that the brainstorm is a qualitative method. The risk description generated by the brainstorm can be supported by quantitative initiatives after the brainstorming itself is done.
[edit] Evidence based method
Identification of risks based on historical data and experience. The method consists of finding similar organizations, projects or tasks, and review them. What went wrong and why, and what went well and why. Then relate it to risks, how they were handled and why. The method ranges from analysis of heavy empirical and statistical data, to qualitative statements and interviews. The essence is to learn from the past in any way possible, in order to improve risk identification. This method may require a lot of resources, because of the amount of potential data. It is most suited for projects which can be related to other projects, and not completely new ventures, because a certain amount of evidence is required. However, even by moving into relatively unknown territory, there will always be some aspects, organizational, technical or human, which will relate to previous experiences. A good example is the NASA space program, which constantly evaluate its own performance, especially when something goes wrong. If a risk has not been identified, but triggers an event, it results in learning and improvement. The risk will definitely be handled differently next time! The method can be carried out in a team or workgroup, but may require a lot of time and individual work.
[edit] Systematic team approach
A team of experts follow a systematic process to identify risks by means of a structured set of prompts or questions [4]. The questions may be predefined from a previous, similar project or situation, or they may be unique. Often, it will be a combination. The process is much less random than the brainstorming method, and more thorough. It is especially strong for projects in which many activities and processes are repetition from previous projects. The process struggles a bit more in undefined projects, like research projects. It is much more difficult to prepare prompts and questions for something there is limited knowledge about. Overall, the selected topics for questions/prompts will have their risks covered very well. However, if some topics are not considered in the systematic team approach, they may be completely missed, because they will not be debated by the team (in this method). The method should yield a complete risk description. All aspects of risk identification should be covered in the systematic approach.
[edit] Hazard and operability study
A Hazard and operability study (HAZOP) has the purpose to identify hazards. By having an isolated method for hazard identification, the risk of forgetting hazards in the risk identification process is reduced. The method is closely related to the systematic team approach, where a set of questions, guidelines or prompts are followed to identify hazards. It is also carried out in a team. The keywords are highly standardized, as almost all possible ways human damage can happen are considered. Examples of keywords could be flow, pressure, temperature, vibrations, chemical reaction and so on. The HAZOP method should be mandatory in projects and situations associated with hazards. This could be, but not limited to, construction, mining, factory, production and military. In fields with less associated hazards, for instance organizational change projects, a HAZOP will not be necessary. It should be emphasized that hazards can also be identified through other non-hazard based methods, but the strength of the HAZOP is the relentless focus on hazards. The method also promotes safety above all else, which is a good signal to send to all employees working in the project or organization.
[edit] Conditions for optimal risk identification
By using one or several of the suggested methods for risk identification, the process is off to a good start. Additional factors in the organization or project environment can greatly affect the outcome of the identification process. Even if the methods are used, it needs to be the right people who are using them. The most important thing to remember, is that risk identification should not be done in a vacuum. An individual can make a good, detailed and useful risk identification – but chances are that it could be greatly improved by involving more people. The process could be done alone by the project leader in a project, or a manager in an organization. That is not recommendable. An individual cannot debate with itself, and there is no chance for a second opinion. The following initiatives will boost the effectiveness and efficiency of the risk identification process.
[edit] Use of a group
The use of a group is the most important condition for optimal risk identification. By having a group, experience and opinions can be pooled together, in an effort to identify risks. It also allows the debate of the individual risk. Quantitatively, a group is more like to identify more relevant risks than an individual, assuming that the group members are qualified. The downsides to having a group are the increased amount of resources required to complete the process, and groupthink may happen [5] . Groupthink, where a desire for harmony and unity leads to dysfunctional decision making, is a threat to any group process. Groupthink, and other group-related problems, are less likely if the group is diverse.
[edit] Diversity of the group
Having a group is a good start, but what is more important is having the right people in the group. In short, the more diverse the group is, the more risk-related areas may be covered. The accumulated experience and knowledge in the group should be as big as possible. Having a lot of people with the same competences will not increase the total risk coverage of the group. The group should be diversified on the following areas:
Technology and knowledge: Especially important if there can be risks involved with the use/development of a certain technology [6]. It may be completely impossible for a non-expert to predict risks in a technical unknown field
Culture and religion: Especially important for understanding the people involved and/or exposed to the risks. Risks are not necessarily considered the same in different cultures.
Demographic knowledge: If a group from Denmark is identifying risks in a construction project in Indonesia, it is important to understand the risks associated with the specific place. It can be achieved either by having people from different geographical areas in the group, or by having acquired knowledge and understanding about a specific place.
Different personalities: Having 5 middle-aged business men in suits may give fine results, but different people tend to have different opinions – and different perspective on risks. The mother of 3, the immigrant or the newly qualified engineer may give a different perspective to the identification process, which is very useful.
Organizational departments: Having only people from one department increases the likelihood of groupthink and departmental selfishness. If the group consists of people from marketing department only for instance, the group may value risk in marketing above else, which is undesirable. Having members from different departments ensures a more non-biased view on risks.
It should be noted that these diversities are recommendable to most groups and organizations – they are not exclusive for a group carrying out the risk identification process. Furthermore, it is not always possible to tailor the group exactly around these principles. In such a situation, it is important that the group recognizes this and asks for advice in other parts of the organization or project group. Consultants can also be used to cover areas where the group is not confident.
[edit] Involving stakeholders
Involving stakeholders in the risk identification process is highly recommended. Assuming we are identifying risks in a project, one of the most logical places to go for advice are the stakeholders [7]. They may have exclusive information on a certain subject, which may help to identify risks. It also gives the stakeholders the opportunity to participate, and take responsibility in the management of risks. A long, formal meeting is not required to involve stakeholders. A simple phone call or conversation about their experience on the subject may point out risks otherwise not identified by the group. Stakeholders should not only be involved the initial stages of risk identification, but also at later stages. When conditions and environments change, stakeholders remain a good source of opinions and information. It should be remembered that some stakeholders may know much more on the subject than members of the group.
[edit] Limitations and conclusion
Risk identification, as a part of risk management, is a recommended process in all organizations and projects. In fact, it is recommended in all aspects of life, to be aware of what might affect our path and objectives. But risk identification should not be overdone either. There is little help in being aware of risks, if nothing is done to control them. Neither is it helpful to spend so many resources, that other vital processes and activities are unable to take place. Another trap may be to assume that risk identification, at a certain point, is complete. All risks have been found. This is simply not possible. By the nature of uncertainty, even the unthinkable happens from time to time. In addition, projects, organizations and their environments is constantly changing. New risks may arise at any time, and therefore, risk identification should be repeated. Risk identification cannot guarantee safety, because the conditions change all the time. This is something that must be fundamentally accepted, that no matter the effort, we cannot assume that everything is within our control. When risk identification is seen in the context of risk management, it is a very strong process that can decide whether objectives are achieved or not. It allows heavy influence on risks in a desired way. In conclusion, risk identification is limited by the nature of uncertainty and chance. But that is no reason not to attempt to affect the risks, because much can be achieved by doing so.
[edit] References
- ↑ ISO Standard 31000: Risk management - Principles and guidelines. Annotation: A complete standard for the risk management process, including risk identification. Main guideline for context of the topic of risk identification
- ↑ ISO Guide 73-2009 – Risk Management Vocabulary. Annotation: Supportive standard for both ISO 31000 and 31010. Contains detailed vocabulary for risk management, including all relevant terms for risk identification
- ↑ http://www.innovation-portal.info/toolkits/brainstorming/ . Annotation: Detailed guide and description for the brainstorming method. Also includes tips on how to achieve the optimal brainstorm
- ↑ ISO Standard 31010: Risk Assesment Techniques. Annotation: A complete standard for the risk assessment process. Supportive standard for the ISO 31000. Goes more in depth with the content of Risk Assesment, namely risk identification, risk analysis and risk evaluation. Contains more details on risk identification than the ISO 31000.
- ↑ Dag Ingvar Jacobsen and Jan Thorsvik, “How organizations work”. Original title, Norwegian: “Hvordan organisasjoner fungerer”. 2nd edition, 2008. Annotation: Complete book about organizations and how they work. Used in the context of groups and organizational culture, which it contains very detailed information about
- ↑ David Davies, “Risk Identification”, Computer Law and Security Report – 1988, Volume 4, Issue 3, pp.20-22 .Annotation: A good introduction to risk identification, including examples and perspective. Also investigates what makes a good risk investigator
- ↑ Mette L. Attrup and John Ryding Olsson, “Power in Projects and Portfolios”. 2nd edition, 2008 .Annotation: Extensive book about basic project and portfolio management. Includes details about risk, uncertainty and risk analysis