Risk Identification Process
| (21 intermediate revisions by one user not shown) | |||
| Line 1: | Line 1: | ||
| − | Risk identification involves identifying and classifying | + | ''Developed by Karlotta Thorhallsdóttir'' |
| − | There are several basic methods for risk identification; documentation review, information gathering, checklist and risk catalogs, assumption analysis and diagram techniques. | + | |
| + | |||
| + | Risk identification involves identifying and classifying sources of a risk to realize what must be managed in a construction project. Risk identification is the first step in [[Risk management process]], as the potential problems must be identified before assessment, respond and control of the risk can take place. Although it is one of the key elements in the process, it is also one of the less defined, and often a neglected element. | ||
| + | There are several basic methods for risk identification; documentation review, information gathering, checklist and risk catalogs, assumption analysis and diagram techniques. Information gathering is the most common method of identifying risk sources. It involves brainstorming sessions to obtain a comprehensive list of possible risks. It relies on the knowledge of experienced project participants, stakeholders and experts to identify the risk. The other methods involve reviewing all project documentations to identify inconsistencies or uncertainties. Developing risk checklist, based on historical information and data from prior projects, analyzing the validity of the project assumptions, identifying the risks from the inaccuracy, instability, inconsistency, or incompleteness of assumptions. It is also possible to use cause and effect diagrams, flow charts and influence diagrams. These methods for identifying risk sources, are profoundly important for the overall [[Risk assessment]] of project and thus contribution to the success of the project. | ||
| + | |||
= Background= | = Background= | ||
| − | + | Construction projects are essentially risky and uncertain due to nature of the construction industry itself. In general, the industry has a difficulty managing the effects of the constant evolving and emerging conditions throughout the project life-cycle. Because of this inherent risky and uncertain nature of the construction industry, [[Management of risk]] is essential to minimize losses and to ensure a project’s success <ref name="okema" />. The construction industry is often associated with low productivity, and is insufficient risk management often defined as the main reason <ref name=" martin " />. Thus, an effective risk management is an essential aspect of managing a construction project to ensure success and quality, and improve productivity. By providing the potential to realizes vulnerability and strength in construction projects <ref name=" banaitiene " />, this can be done. Risk management process consist of four main steps, identify, asses, respond and control. Through risk management, transparency increases, and many problems can be avoided or mitigated, but the success rate of risk management is highly dependent on the first step, risk identification <ref name=" winch " />. | |
| + | |||
= Risk Identification Process = | = Risk Identification Process = | ||
| − | [[File:RIP.png|300px|thumb|right|Risk Identification | + | [[File:RIP.png|300px|thumb|right|Risk Identification Process as defined by PMI <ref name=" PMI " />]] |
| − | + | Risk identification is the first step in the risk management process and is often defined as the most important aspect <ref name=" winch " /> as an unidentified risk cannot be dealt with <ref name=" martin " /> and the effectiveness of risk management is dependent on correct risk identification <ref name=" banaitiene " />. The main aspect of risk identification is identifying possible risk sources, underlying condition that can generate a risk event and impact the success rate of a construction project. It relies mostly on utilizing experience form past projects. Although risk identification is the first step in the risk management process, it must also be carried out consistent with the project process as over the project life-cycle as further risks might emerge <ref name=" martin " /> . | |
| − | Risk identification is the first step in the risk management process and is often defined as the most important aspect <ref name=" winch " /> as | + | |
There are several risk identification processes available, the process defined by the Project Management Institute (PMI) will be discussed in detailed. PMI have developed a widely accepted standard in project management, the PMBOK ® Guide, in which risk identification process, with a three-step data flow <ref name=" PMI " />, is defined. Inputs are information used for the risk identification and the risk register is the product of risk identification. | There are several risk identification processes available, the process defined by the Project Management Institute (PMI) will be discussed in detailed. PMI have developed a widely accepted standard in project management, the PMBOK ® Guide, in which risk identification process, with a three-step data flow <ref name=" PMI " />, is defined. Inputs are information used for the risk identification and the risk register is the product of risk identification. | ||
| − | |||
| − | |||
| − | Inputs to the risk identification process are project information, plans and documentations which are used to realize possible risk sources and ensure are more accurate risk identification process. These inputs (see figure | + | == Inputs == |
| + | Inputs to the risk identification process are project information, plans and documentations which are used to realize possible risk sources and ensure are more accurate risk identification process. These inputs (see figure below) consist of plans estimations and assumptions, criteria, requirements, and uncontrollable conditions (i.e environmental conditions) which are sources of risk and uncertainty in construction projects <ref name=" PMI " />. | ||
| + | [[File:Inputs.PNG|550px|thumb|center|Inputs to the risk identification and the description of their contents. The table was generated using the content form (PMI, 2013)]] | ||
| + | |||
== Basic Method for Identifying Risks == | == Basic Method for Identifying Risks == | ||
=== Documentation Reviews === | === Documentation Reviews === | ||
| − | Documentation review | + | Documentation review consists of collecting project documentations and reviewing them in a structured way, to determine the accuracy, completeness and consistency of the information. These project documentations are plans, assumptions, previous project files, agreements, etc. The purpose is to gain a scheme of possible risk sources in the project. Indicators of risk can be determined form the quality and consistency between the requirements and assumptions of the project information, inaccurate, incomplete or inconsistency project documentation <ref name=" PMI " />. |
| + | |||
=== Information Gathering Techniques === | === Information Gathering Techniques === | ||
| − | There are several methods of gathering information and they are the most common methods of identifying risk sources. These methods are based primarily on utilizing the knowledge of experienced people in the business <ref name=" winch " />. | + | There are several methods of gathering information and they are the most common methods of identifying risk sources in the construction industry. These methods are based primarily on utilizing the knowledge of experienced people in the business <ref name=" winch " />. |
| + | |||
| + | |||
==== Brainstorming ==== | ==== Brainstorming ==== | ||
| − | Brainstorming as a method of identifying | + | Brainstorming as a method of identifying risks in a project. It is one of the oldest and most commonly used technique <ref name=" baumann " />. The method involves a small group of relevant parties, such as the project team, stakeholders and independent experts who under a short period, generate ideas, under the leadership of a facilitator <ref name=" PMI " />. These ideas generated are possible project risks. The time frame is limited to increase productivity during the meetings and uphold concentration <ref name=" baumann " />. |
| − | Brainstorming | + | Brainstorming has its limitations which effect the applicability of the method. Team members who are directly involved in the project are often chosen for the sessions, as it is more convenient or suitable for organizations. Nevertheless, this direction prevents proposed risks sources from different perspectives and thus, less diverse results. The time pressure set on the brainstorming sessions can hinder creativity as the time for adjusting to the change in working is limited but on the other hand longer time periods lead to less productivity. Also, this new way of working might not suit everyone. It might inhibit their creative thinking or due to the social aspect of it so they might not express their ideas and opinions. Judgment of proposals in the early stage of the process can discourage members from presenting their ideas. Lastly, the facilitator can influence the discussion in a preferable direction and thus, respectively influence the results <ref name=" baumann " />. |
| + | |||
| + | |||
==== Delphi technique ==== | ==== Delphi technique ==== | ||
| − | The Delphi | + | [[The Delphi Technique in Project Management]] involves a panel of project risk experts, who offer their expert opinion to identify project risk in a faster and more reliable manner without influences <ref name=" baumann " />. The experts answer questioners anonymously provided by a facilitator. The experts’ responses are summarized and recirculated for further comment until a consensus is reached <ref name=" PMI " />. |
| + | There are some limitations to the method. The interpretation of the results from the questioners and the classification of the risks developed can be challenging, as objectivity and bias thinking must be adapted to achieve a realistic view. | ||
| + | |||
| + | |||
==== Interviewing ==== | ==== Interviewing ==== | ||
| − | The method of interviewing experienced project participants, stakeholders, and experts in the subject to identify project risk sources, essentially involves documenting known risks as well as identifying new risk sources | + | The method of interviewing experienced project participants, stakeholders, and experts in the subject to identify project risk sources, essentially involves documenting known risks as well as identifying new risk sources <ref name=" PMI " />. The interview is conducted face to face for a relative short time and the method is a flexible tool which is easily adaptable to different types of projects <ref name=" baumann " />. |
| + | Despite the method of interviewing is considered to have various advantages it has its limitations as well. As in using the Delphi technique, the interpretation and classification of the results can be challenging, as objectivity and bias thinking must be adapted to achieve a realistic view. Moreover, training and practice is needed to write open-ended questions and to lead the interview in an explicit direction to get structural result. Finally, the preparations, documentation, transcription and interpretation of data which is inherent in the process is time-consuming <ref name=" Winch2" />. | ||
| + | |||
| − | |||
==== Root cause analysis ==== | ==== Root cause analysis ==== | ||
Root cause analysis is a method of identifying essential causes of risk and the underlying causes of it. Identifying the root cause of risks assists in identifying more risks and understand the risk more clearly <ref name=" PMI " />. | Root cause analysis is a method of identifying essential causes of risk and the underlying causes of it. Identifying the root cause of risks assists in identifying more risks and understand the risk more clearly <ref name=" PMI " />. | ||
| + | |||
=== Diagramming Techniques === | === Diagramming Techniques === | ||
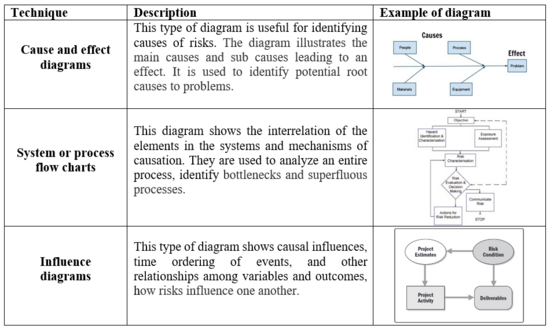
| − | [[File:DT.PNG| | + | Risk diagramming techniques are quantitative methods. PMBOK® Guide mentions three risk diagram techniques used in risk identifications, described and shown below. |
| + | [[File:DT.PNG|550px|thumb|center|The three different diagram techniques described in PIM and their description and example. The table was generated using the content form (PMI, 2013)]] | ||
| − | |||
=== Checklist Analysis === | === Checklist Analysis === | ||
| − | Checklist analysis has also been found as one of the more commonly used methods for risk identification <ref name=" Winch2" />. Checklist with possible risk sources can be developed based on historical data from previous projects and other sources. This method is a quick and simple way of identifying risks in a project and requires relatively limited experience. When creating a checklist for risk identification, it is important to remember that it is not possible to create an all-inclusive list and that each project, though similar have project specific risks. Additionally, items missing from the checklist should also be explored and the checklist review throughout the project life-cycle <ref name=" PMI " />. | + | Checklist analysis has also been found as one of the more commonly used methods for risk identification <ref name=" Winch2" />. Checklist with possible risk sources can be developed based on historical data from previous projects and other sources. This method is a quick and simple way of identifying risks in a project and requires relatively limited experience. When creating a checklist for risk identification, it is important to remember that it is not possible to create an all-inclusive list and that each project, though similar, have project specific risks. Additionally, items missing from the checklist should also be explored and the checklist review throughout the project life-cycle <ref name=" PMI " />. |
| + | |||
=== Assumptions Analysis === | === Assumptions Analysis === | ||
The method explores the validity of the assumptions made in the project planning process. It is primarily based on identifying risks in the project due to inaccuracy, inconsistency and incompleteness of the assumptions <ref name=" PMI " />. | The method explores the validity of the assumptions made in the project planning process. It is primarily based on identifying risks in the project due to inaccuracy, inconsistency and incompleteness of the assumptions <ref name=" PMI " />. | ||
| + | |||
=== SWOT Analysis === | === SWOT Analysis === | ||
[[File:SWOT.png|180px|thumb|right|The four aspects of SWOT analysis <ref name=" baumann " />]] | [[File:SWOT.png|180px|thumb|right|The four aspects of SWOT analysis <ref name=" baumann " />]] | ||
| + | SWOT is an acronym for strength, weaknesses, opportunities and threats and [[SWOT analysis]] (also known as [[SWOT matrix]]) focuses on evaluating these four elements of an organization or project. This method of identifying risk also expands the range of identified risks by including internally generated risks <ref name=" PMI " />. Analysis of the internal section of a project includes looking at the strengths and weaknesses and analysis of the external section includes the opportunities and threats <ref name=" baumann " />. First, the strengths and weaknesses of a project are identified and then the opportunities and threats from those results. The method also analyses to which degree the strengths counteract the threats and identify the opportunities which may surmount the weaknesses <ref name=" PMI " />. In some cases, brainstorming may be used to identify possible strengths, weaknesses, opportunities and threats. In risk identification, the weaknesses and threats are more important aspects, as they are the possible risk sources of the project which may need to be managed <ref name=" baumann " />. | ||
| + | SWOT analysis is not acceptable for identifying future risks, but only existing or obvious risks. There is also a challenge in categorizing accurately as strengths can become weaknesses, opportunities can turn into threats and not all combinations may be considered. Furthermore, SWOT analysis is mainly a qualitative analysis and without quantitative analysis. | ||
| − | |||
| − | |||
=== Expert Judgment === | === Expert Judgment === | ||
The method utilizes the expert judgement and experience of experts in the relevant field. The project manager appoints the experts who identify and suggest possible risks directly by considering all aspects of the project. For this method, the experts’ bias should be considered as it can influence the result immensely <ref name=" PMI " />. | The method utilizes the expert judgement and experience of experts in the relevant field. The project manager appoints the experts who identify and suggest possible risks directly by considering all aspects of the project. For this method, the experts’ bias should be considered as it can influence the result immensely <ref name=" PMI " />. | ||
| + | |||
== Risk Register == | == Risk Register == | ||
| − | The | + | The [[Risk register]] is a document containing all the results from the elements of the risk managements process. The main product of the risk identification is the initial recording in the risk register. Over time, as more results from the risk management process are recorded, the type and level of information contained in the registry increases. The information from the risk identification process registered in the risk register are of two types; identified risk and potential responses. The risk identified must described in a detailed and sensible manner. During risk identification, the cause of risks might be identified, in that case, they should be recorder so that they may be used for future reference. During the risk identification process, the potential response may be identified, if so, they should be used as inputs for the risk response planning <ref name=" PMI " />. |
| − | |||
| − | |||
| − | |||
| − | = | + | = Limitation = |
| − | + | Although risk identification is considered a vital part in risk management, the process is still relatively less understood than other elements in risk management and the techniques are less developed. As mentioned before, the most commonly used risk identification methods are checklists, brainstorming, interviewing and SWOT analysis. The other techniques are rarely used as many have doubts and lack knowledge about their applicability <ref name=" Winch2" />. Numerous of these methods rely heavily on historical data, which might not cover all potential risks as each project is unique and consequently has its own specific project related risks that need to be identified and managed <ref name=" Winch2" />. Risk identification needs to be constant over the project life-cycle as new risks may become apparent with the increased level of information. However, even if risk identification has been performed throughout a project life-cycle, there is always a possibility that some risks are overlooked <ref name="chapman"/>. | |
| + | The inaccuracy of the methods used is due to many various aspects, most of them related to the human activities. The choice of the members of the risk identification teams are therefore, of great importance. The lack of experts with varying perspectives could lead to an inaccurate choice of critical risk sources as their opinions are rarely questioned. Consequently, the selection of experts effects the results of the method and can thus be influenced. Despite the importance of the competence and skills of the chosen members, the individuals are working collaboratively and thus, compatibility is important to ensure results of high quality. To control the team effectiveness, individual characteristics can be asses with the [[Myers-Briggs Type Indicator]] in order to evaluate and balance the team’s behavior <ref name="chapman"/>. When interpreting results from interviewing, it’s important to remain objective and bias. | ||
| − | |||
| − | |||
| − | The | + | The difficulty in obtaining accurate result in risk identification as well of the lack of knowledge is one of the primary reasons why risk identification is often a neglected element in risk management process. Thus, further research and development of the tools and techniques is needed as risk identification is the fundamental step in risk management which assessment, respond and control of risks are dependent on. |
| + | |||
| + | |||
| + | = Annotated bibliography = | ||
Banaitiene, N. (2012). Risk management in construction projects. In N. Banaitiene & A. Banaitis. Risk Management - Current Issues and Challenges. INTECH Open Access Publisher. Retrieved from: http://cdn.intechopen.com/pdfs/38973/InTechRisk_management_in_construction_projects.pdf | Banaitiene, N. (2012). Risk management in construction projects. In N. Banaitiene & A. Banaitis. Risk Management - Current Issues and Challenges. INTECH Open Access Publisher. Retrieved from: http://cdn.intechopen.com/pdfs/38973/InTechRisk_management_in_construction_projects.pdf | ||
| Line 93: | Line 110: | ||
This article emphasizes the importance of risk identification within the risk management process as it is the basis for every further stage. The authors describe several risk identification tools (methods) used and defines the most commonly used methods in businesses today. The authors advocates using several of these tools together as it offers the highest potential of identifying the potential risks and the techniques must be customized to each project in accordance with their business nature. The authors also propose that diversity in the risk identification team will result in more accurate identification. | This article emphasizes the importance of risk identification within the risk management process as it is the basis for every further stage. The authors describe several risk identification tools (methods) used and defines the most commonly used methods in businesses today. The authors advocates using several of these tools together as it offers the highest potential of identifying the potential risks and the techniques must be customized to each project in accordance with their business nature. The authors also propose that diversity in the risk identification team will result in more accurate identification. | ||
| + | |||
= References = | = References = | ||
| Line 108: | Line 126: | ||
<ref name="Winch2"> Maytorena, E., Winch, G. M. & Kiely, T. (2005). Construction risk identification. K. Kähkönen, & M. Sexton, Understanding the Construction Business and Companies in the New Millennium, pp. 304-315. </ref> | <ref name="Winch2"> Maytorena, E., Winch, G. M. & Kiely, T. (2005). Construction risk identification. K. Kähkönen, & M. Sexton, Understanding the Construction Business and Companies in the New Millennium, pp. 304-315. </ref> | ||
| − | |||
| − | |||
<ref name="chapman"> Chapman, R. J. (1998). The effectiveness of working group risk identification and assessment techniques. International Journal of Project Management, 16(6), pp. 333-343. </ref> | <ref name="chapman"> Chapman, R. J. (1998). The effectiveness of working group risk identification and assessment techniques. International Journal of Project Management, 16(6), pp. 333-343. </ref> | ||
</references> | </references> | ||
Latest revision as of 19:26, 20 November 2018
Developed by Karlotta Thorhallsdóttir
Risk identification involves identifying and classifying sources of a risk to realize what must be managed in a construction project. Risk identification is the first step in Risk management process, as the potential problems must be identified before assessment, respond and control of the risk can take place. Although it is one of the key elements in the process, it is also one of the less defined, and often a neglected element.
There are several basic methods for risk identification; documentation review, information gathering, checklist and risk catalogs, assumption analysis and diagram techniques. Information gathering is the most common method of identifying risk sources. It involves brainstorming sessions to obtain a comprehensive list of possible risks. It relies on the knowledge of experienced project participants, stakeholders and experts to identify the risk. The other methods involve reviewing all project documentations to identify inconsistencies or uncertainties. Developing risk checklist, based on historical information and data from prior projects, analyzing the validity of the project assumptions, identifying the risks from the inaccuracy, instability, inconsistency, or incompleteness of assumptions. It is also possible to use cause and effect diagrams, flow charts and influence diagrams. These methods for identifying risk sources, are profoundly important for the overall Risk assessment of project and thus contribution to the success of the project.
Contents |
[edit] Background
Construction projects are essentially risky and uncertain due to nature of the construction industry itself. In general, the industry has a difficulty managing the effects of the constant evolving and emerging conditions throughout the project life-cycle. Because of this inherent risky and uncertain nature of the construction industry, Management of risk is essential to minimize losses and to ensure a project’s success [1]. The construction industry is often associated with low productivity, and is insufficient risk management often defined as the main reason [2]. Thus, an effective risk management is an essential aspect of managing a construction project to ensure success and quality, and improve productivity. By providing the potential to realizes vulnerability and strength in construction projects [3], this can be done. Risk management process consist of four main steps, identify, asses, respond and control. Through risk management, transparency increases, and many problems can be avoided or mitigated, but the success rate of risk management is highly dependent on the first step, risk identification [4].
[edit] Risk Identification Process
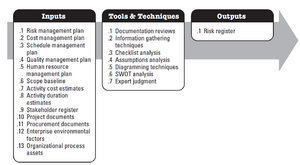
Risk identification is the first step in the risk management process and is often defined as the most important aspect [4] as an unidentified risk cannot be dealt with [2] and the effectiveness of risk management is dependent on correct risk identification [3]. The main aspect of risk identification is identifying possible risk sources, underlying condition that can generate a risk event and impact the success rate of a construction project. It relies mostly on utilizing experience form past projects. Although risk identification is the first step in the risk management process, it must also be carried out consistent with the project process as over the project life-cycle as further risks might emerge [2] . There are several risk identification processes available, the process defined by the Project Management Institute (PMI) will be discussed in detailed. PMI have developed a widely accepted standard in project management, the PMBOK ® Guide, in which risk identification process, with a three-step data flow [5], is defined. Inputs are information used for the risk identification and the risk register is the product of risk identification.
[edit] Inputs
Inputs to the risk identification process are project information, plans and documentations which are used to realize possible risk sources and ensure are more accurate risk identification process. These inputs (see figure below) consist of plans estimations and assumptions, criteria, requirements, and uncontrollable conditions (i.e environmental conditions) which are sources of risk and uncertainty in construction projects [5].
[edit] Basic Method for Identifying Risks
[edit] Documentation Reviews
Documentation review consists of collecting project documentations and reviewing them in a structured way, to determine the accuracy, completeness and consistency of the information. These project documentations are plans, assumptions, previous project files, agreements, etc. The purpose is to gain a scheme of possible risk sources in the project. Indicators of risk can be determined form the quality and consistency between the requirements and assumptions of the project information, inaccurate, incomplete or inconsistency project documentation [5].
[edit] Information Gathering Techniques
There are several methods of gathering information and they are the most common methods of identifying risk sources in the construction industry. These methods are based primarily on utilizing the knowledge of experienced people in the business [4].
[edit] Brainstorming
Brainstorming as a method of identifying risks in a project. It is one of the oldest and most commonly used technique [6]. The method involves a small group of relevant parties, such as the project team, stakeholders and independent experts who under a short period, generate ideas, under the leadership of a facilitator [5]. These ideas generated are possible project risks. The time frame is limited to increase productivity during the meetings and uphold concentration [6]. Brainstorming has its limitations which effect the applicability of the method. Team members who are directly involved in the project are often chosen for the sessions, as it is more convenient or suitable for organizations. Nevertheless, this direction prevents proposed risks sources from different perspectives and thus, less diverse results. The time pressure set on the brainstorming sessions can hinder creativity as the time for adjusting to the change in working is limited but on the other hand longer time periods lead to less productivity. Also, this new way of working might not suit everyone. It might inhibit their creative thinking or due to the social aspect of it so they might not express their ideas and opinions. Judgment of proposals in the early stage of the process can discourage members from presenting their ideas. Lastly, the facilitator can influence the discussion in a preferable direction and thus, respectively influence the results [6].
[edit] Delphi technique
The Delphi Technique in Project Management involves a panel of project risk experts, who offer their expert opinion to identify project risk in a faster and more reliable manner without influences [6]. The experts answer questioners anonymously provided by a facilitator. The experts’ responses are summarized and recirculated for further comment until a consensus is reached [5]. There are some limitations to the method. The interpretation of the results from the questioners and the classification of the risks developed can be challenging, as objectivity and bias thinking must be adapted to achieve a realistic view.
[edit] Interviewing
The method of interviewing experienced project participants, stakeholders, and experts in the subject to identify project risk sources, essentially involves documenting known risks as well as identifying new risk sources [5]. The interview is conducted face to face for a relative short time and the method is a flexible tool which is easily adaptable to different types of projects [6]. Despite the method of interviewing is considered to have various advantages it has its limitations as well. As in using the Delphi technique, the interpretation and classification of the results can be challenging, as objectivity and bias thinking must be adapted to achieve a realistic view. Moreover, training and practice is needed to write open-ended questions and to lead the interview in an explicit direction to get structural result. Finally, the preparations, documentation, transcription and interpretation of data which is inherent in the process is time-consuming [7].
[edit] Root cause analysis
Root cause analysis is a method of identifying essential causes of risk and the underlying causes of it. Identifying the root cause of risks assists in identifying more risks and understand the risk more clearly [5].
[edit] Diagramming Techniques
Risk diagramming techniques are quantitative methods. PMBOK® Guide mentions three risk diagram techniques used in risk identifications, described and shown below.
[edit] Checklist Analysis
Checklist analysis has also been found as one of the more commonly used methods for risk identification [7]. Checklist with possible risk sources can be developed based on historical data from previous projects and other sources. This method is a quick and simple way of identifying risks in a project and requires relatively limited experience. When creating a checklist for risk identification, it is important to remember that it is not possible to create an all-inclusive list and that each project, though similar, have project specific risks. Additionally, items missing from the checklist should also be explored and the checklist review throughout the project life-cycle [5].
[edit] Assumptions Analysis
The method explores the validity of the assumptions made in the project planning process. It is primarily based on identifying risks in the project due to inaccuracy, inconsistency and incompleteness of the assumptions [5].
[edit] SWOT Analysis
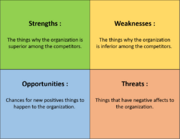
SWOT is an acronym for strength, weaknesses, opportunities and threats and SWOT analysis (also known as SWOT matrix) focuses on evaluating these four elements of an organization or project. This method of identifying risk also expands the range of identified risks by including internally generated risks [5]. Analysis of the internal section of a project includes looking at the strengths and weaknesses and analysis of the external section includes the opportunities and threats [6]. First, the strengths and weaknesses of a project are identified and then the opportunities and threats from those results. The method also analyses to which degree the strengths counteract the threats and identify the opportunities which may surmount the weaknesses [5]. In some cases, brainstorming may be used to identify possible strengths, weaknesses, opportunities and threats. In risk identification, the weaknesses and threats are more important aspects, as they are the possible risk sources of the project which may need to be managed [6]. SWOT analysis is not acceptable for identifying future risks, but only existing or obvious risks. There is also a challenge in categorizing accurately as strengths can become weaknesses, opportunities can turn into threats and not all combinations may be considered. Furthermore, SWOT analysis is mainly a qualitative analysis and without quantitative analysis.
[edit] Expert Judgment
The method utilizes the expert judgement and experience of experts in the relevant field. The project manager appoints the experts who identify and suggest possible risks directly by considering all aspects of the project. For this method, the experts’ bias should be considered as it can influence the result immensely [5].
[edit] Risk Register
The Risk register is a document containing all the results from the elements of the risk managements process. The main product of the risk identification is the initial recording in the risk register. Over time, as more results from the risk management process are recorded, the type and level of information contained in the registry increases. The information from the risk identification process registered in the risk register are of two types; identified risk and potential responses. The risk identified must described in a detailed and sensible manner. During risk identification, the cause of risks might be identified, in that case, they should be recorder so that they may be used for future reference. During the risk identification process, the potential response may be identified, if so, they should be used as inputs for the risk response planning [5].
[edit] Limitation
Although risk identification is considered a vital part in risk management, the process is still relatively less understood than other elements in risk management and the techniques are less developed. As mentioned before, the most commonly used risk identification methods are checklists, brainstorming, interviewing and SWOT analysis. The other techniques are rarely used as many have doubts and lack knowledge about their applicability [7]. Numerous of these methods rely heavily on historical data, which might not cover all potential risks as each project is unique and consequently has its own specific project related risks that need to be identified and managed [7]. Risk identification needs to be constant over the project life-cycle as new risks may become apparent with the increased level of information. However, even if risk identification has been performed throughout a project life-cycle, there is always a possibility that some risks are overlooked [8]. The inaccuracy of the methods used is due to many various aspects, most of them related to the human activities. The choice of the members of the risk identification teams are therefore, of great importance. The lack of experts with varying perspectives could lead to an inaccurate choice of critical risk sources as their opinions are rarely questioned. Consequently, the selection of experts effects the results of the method and can thus be influenced. Despite the importance of the competence and skills of the chosen members, the individuals are working collaboratively and thus, compatibility is important to ensure results of high quality. To control the team effectiveness, individual characteristics can be asses with the Myers-Briggs Type Indicator in order to evaluate and balance the team’s behavior [8]. When interpreting results from interviewing, it’s important to remain objective and bias.
The difficulty in obtaining accurate result in risk identification as well of the lack of knowledge is one of the primary reasons why risk identification is often a neglected element in risk management process. Thus, further research and development of the tools and techniques is needed as risk identification is the fundamental step in risk management which assessment, respond and control of risks are dependent on.
[edit] Annotated bibliography
Banaitiene, N. (2012). Risk management in construction projects. In N. Banaitiene & A. Banaitis. Risk Management - Current Issues and Challenges. INTECH Open Access Publisher. Retrieved from: http://cdn.intechopen.com/pdfs/38973/InTechRisk_management_in_construction_projects.pdf
The chapter in the book Risk Management – Current Issues and Challenges discusses risk management in a construction project and the four steps in the process defined in the standard publish by the project management institute (PMI). The first step is defined as risk identification and is considered the most important step by the authors. The chapter also introduces a few methods of risk identification in a project and discusses the importance of accurate risk identification for a project success.
Winch, G.M. (2010) Managing Construction Projects: An Information Processing Approach, Second Edition. Oxford: Wiley-Blackwell Publishing.
The book contains a description of the practice of managing risk and uncertainty in a construction project. The four steps of risk management process are introduced and each step of the process is described lightly. The author defines risk identification as a key step in the beginning of the process but also that the risk identification is important throughout the project life-cycle. The management of the risk identified is describes as well in great detail, that is the respond and control to the risk sources.
Project Management Institute, Inc. (2013). A Guide to the Project Management Body of Knowledge (PMBOK® Guide) – Fifth Edition. Newtown Square, Pennsylvania :Project Management Institute, Inc
The Project Management Institute’s “A Guide to the Project Management Body of Knowledge” is a guideline for managing individual projects and defines project management related concepts. The guideline also describes the project and the project management life-cycle and their processes. In the guideline, there are nine knowledge areas, typical in most construction project, defined, risk management being one of them. In the risk management process, risk identification process is described in great detail, what is needed for the identification, basic methods for risk identification and the product of risk identification, the risk register
Baumann, S., Erber, I. & Gattringer, M. (2016) Selection of risk identification instruments. ACRN Oxford Journal of Finance and Risk Perspectives 5(2), pp. 27-41.
This article emphasizes the importance of risk identification within the risk management process as it is the basis for every further stage. The authors describe several risk identification tools (methods) used and defines the most commonly used methods in businesses today. The authors advocates using several of these tools together as it offers the highest potential of identifying the potential risks and the techniques must be customized to each project in accordance with their business nature. The authors also propose that diversity in the risk identification team will result in more accurate identification.
[edit] References
- ↑ Okema, J. E. (2000). "Risk and Uncertainty Management of Projects: Challenges of Construction Industry." International Conference on Construction in Developing Countries. Rotterdam, Netherlands: InHouse Publishing. Retrieved from: https://www.irbnet.de/daten/iconda/CIB8940.pdf
- ↑ 2.0 2.1 2.2 Martin, S. (2006). “Risk management in construction project management”. Journal of Business Economics and Management. 7(2), pp.77-83: http://www.tandfonline.com/doi/pdf/10.1080/16111699.2006.9636126
- ↑ 3.0 3.1 Banaitiene, N. (2012). Risk management in construction projects. In N. Banaitiene & A. Banaitis. Risk Management - Current Issues and Challenges. INTECH Open Access Publisher. Retrieved from: http://cdn.intechopen.com/pdfs/38973/InTechRisk_management_in_construction_projects.pdf
- ↑ 4.0 4.1 4.2 Winch, G.M. (2010) Managing Construction Projects: An Information Processing Approach, Second Edition. Oxford: Wiley-Blackwell Publishing
- ↑ 5.00 5.01 5.02 5.03 5.04 5.05 5.06 5.07 5.08 5.09 5.10 5.11 5.12 5.13 Project Management Institute, Inc. (2013). A Guide to the Project Management Body of Knowledge (PMBOK® Guide) – Fifth Edition. Newtown Square, Pennsylvania :Project Management Institute, Inc
- ↑ 6.0 6.1 6.2 6.3 6.4 6.5 6.6 6.7 Baumann, S., Erber, I. & Gattringer, M. (2016) Selection of risk identification instruments. ACRN Oxford Journal of Finance and Risk Perspectives 5(2), pp. 27-41.
- ↑ 7.0 7.1 7.2 7.3 Maytorena, E., Winch, G. M. & Kiely, T. (2005). Construction risk identification. K. Kähkönen, & M. Sexton, Understanding the Construction Business and Companies in the New Millennium, pp. 304-315.
- ↑ 8.0 8.1 Chapman, R. J. (1998). The effectiveness of working group risk identification and assessment techniques. International Journal of Project Management, 16(6), pp. 333-343.