Risk management in industry 4.0
(→Risk identification) |
(→Limitations) |
||
| (30 intermediate revisions by one user not shown) | |||
| Line 36: | Line 36: | ||
The core idea of industry 4.0 is to implement the Cyber Physical Systems (CPS) for production, i.e. using actuators and sensors, networks of microcomputers, linking the machines to the value chain. It also considers the digital enhancement and reengineering of products. The Figure 1 shows an abstract of industry 4.0 production style. In addition, it is denoted by highly differentiated customized products, and specific combination of product and services, and further the value added services with the actual product or service. After all, industry 4.0 is supposed to have three smart targets: machines, storage system, and production facility. That means minimizing the human interventions and grow productivity. It focus on decentralized and highly automated production, as shown in Figure 1. | The core idea of industry 4.0 is to implement the Cyber Physical Systems (CPS) for production, i.e. using actuators and sensors, networks of microcomputers, linking the machines to the value chain. It also considers the digital enhancement and reengineering of products. The Figure 1 shows an abstract of industry 4.0 production style. In addition, it is denoted by highly differentiated customized products, and specific combination of product and services, and further the value added services with the actual product or service. After all, industry 4.0 is supposed to have three smart targets: machines, storage system, and production facility. That means minimizing the human interventions and grow productivity. It focus on decentralized and highly automated production, as shown in Figure 1. | ||
| − | One of the easiest examples of sensor networks is RFID (Radio-frequency Identification). Invented to solve logistic problems of army, RFID works via radio waves to read and capture information stored on a tag attached to an object. A tag can be read from up to several feet away and does not need to be within direct line-of-sight of the reader to be tracked. This means that it is possible to know what a pack | + | One of the easiest examples of sensor networks is RFID (Radio-frequency Identification). Invented to solve logistic problems of army, RFID works via radio waves to read and capture information stored on a tag attached to an object. A tag can be read from up to several feet away and does not need to be within direct line-of-sight of the reader to be tracked. This means that it is possible to know what a pack contains exactly without opening it.<ref name="RFID"> "https://link.springer.com/chapter/10.1007%2F978-2-8178-0363-0_7/"Electromagnetic Fields, Environment and Health" </ref> |
In such an unknown business environment there are many challenges concerning the management approaches, for instance business model innovation, since success in industry 4.0 is due to the innovation capability of enterprise. If organization requires to be smart, they need bright employees, and climate for learning and innovation, which needs appropriate management practices. Management plays a fundamental role for industry 4.0, since the requisite of Industry 4.0 is to develop capabilities across different dimensions in the organizations. There is need to develop capabilities to successfully manage business models, and product portfolio, to access potential market and customers, to intensify value chain processes and systems, legal matters, cultural management -because of globalization- and mostly risk management. | In such an unknown business environment there are many challenges concerning the management approaches, for instance business model innovation, since success in industry 4.0 is due to the innovation capability of enterprise. If organization requires to be smart, they need bright employees, and climate for learning and innovation, which needs appropriate management practices. Management plays a fundamental role for industry 4.0, since the requisite of Industry 4.0 is to develop capabilities across different dimensions in the organizations. There is need to develop capabilities to successfully manage business models, and product portfolio, to access potential market and customers, to intensify value chain processes and systems, legal matters, cultural management -because of globalization- and mostly risk management. | ||
| Line 50: | Line 50: | ||
==== Identification ==== | ==== Identification ==== | ||
| − | During this first process, potential risk events and their characteristics that can have a negative effect on the project are identified. It is possible to repeat this step, as risks can change or new risks are discovered, all over the project's | + | During this first process, potential risk events and their characteristics that can have a negative effect on the project are identified. It is possible to repeat this step, as risks can change or new risks are discovered, all over the project's life cycle. The identification process can consist of a variety of different stakeholders, project management team, experts, senior managers, etc. |
==== Assessment ==== | ==== Assessment ==== | ||
| Line 79: | Line 79: | ||
It is important to outline that risks should be monitored, reviewed and controlled steadily. Risk control is carried out by constantly monitoring the identified risks and identifying and analyzing the new risks. Risks and the effectiveness of controls and mitigations should be assessed throughout the project life cycle. | It is important to outline that risks should be monitored, reviewed and controlled steadily. Risk control is carried out by constantly monitoring the identified risks and identifying and analyzing the new risks. Risks and the effectiveness of controls and mitigations should be assessed throughout the project life cycle. | ||
| − | Moreover, the last few years has seen the emergence of Enterprise Risk Management (ERM), which is often denoted as a new business trend that builds on the principles of traditional risk management. It is a more structured and disciplined approach that | + | Moreover, the last few years has seen the emergence of Enterprise Risk Management (ERM), which is often denoted as a new business trend that builds on the principles of traditional risk management. It is a more structured and disciplined approach that coordinates strategy, processes, people, technology and knowledge, with the intent of evaluating and managing the uncertainties the enterprise faces as it creates value. |
== Risk management and performance == | == Risk management and performance == | ||
| Line 92: | Line 92: | ||
The purpose of risk identification is to find all the risks that can hinder the achievements of the business. | The purpose of risk identification is to find all the risks that can hinder the achievements of the business. | ||
| − | And it is fundamental to identify the risks related to not getting an opportunity as soon as possible, since a risk that is not considered at this stage will not be recognized in remoter risk analysis. As it was mentioned before, industry 4.0 generates new several operational | + | And it is fundamental to identify the risks related to not getting an opportunity as soon as possible, since a risk that is not considered at this stage will not be recognized in remoter risk analysis. As it was mentioned before, industry 4.0 generates new several operational risks, affecting the manufacturing area: |
* Manufacturing process management: information risk associated with data losses | * Manufacturing process management: information risk associated with data losses | ||
| Line 105: | Line 105: | ||
* Machine environments: attack from Internet network, problems related to electromagnetic compatibility and electromagnetic emissions affecting manufacturing machines<ref name="RM4.0" /> | * Machine environments: attack from Internet network, problems related to electromagnetic compatibility and electromagnetic emissions affecting manufacturing machines<ref name="RM4.0" /> | ||
| − | Most of repeated risk factors in the manufacturing are connected with information security. So, it is fundamental to understand to protect this manufacturing system against cyber-attacks, loss of data integrity or problems related to the availability of information and the way to achieve that is implementing the information security management system (ISMS). Even if information security is accessible only to who | + | Most of repeated risk factors in the manufacturing are connected with information security. So, it is fundamental to understand how to protect this manufacturing system against cyber-attacks, loss of data integrity or problems related to the availability of information; and the way to achieve that is implementing the information security management system (ISMS). Even if information security is accessible only to who has access, it is critical to consider also integrity and availability. The first one means protecting the reliability and plenitude of information and processing methods. And availability means the possibility to get every data in every moment. Implementing this standard should be the key to solve the problem of security inside companies which follow the Industry 4.0 model. |
| − | The similarity with other ISO standards | + | The similarity with other ISO standards is important for building a certified integrated management system based on the management of quality, information and environmental requirements. On the other hand, the standard ISMS can be effectively integrated into ERM. |
==== Design a structure ==== | ==== Design a structure ==== | ||
| − | The | + | The next step is to incorporate and implement the crucial needs for ERM and ISMS. This idea is thought to implement Industry 4.0 concept in manufacturing companies, as it allows to cut down enterprise risks connected with enterprise strategy and the implementation of the certified information security system. [[File:Im33.PNG|650px|thumb|right|Figure 3: Basic principles and processes of implementation - inspired from "Information Security Management to Enterprise Risk Management", but made by Stefano di Lenardo <ref name="FM"> "https://www.springer.com/cda/content/document/cda_downloaddocument/9783319067728-c1.pdf?SGWID=0-0-45-1486617-p176729880 |
"/"From Information Security Management to Enterprise Risk Management" </ref> | "/"From Information Security Management to Enterprise Risk Management" </ref> | ||
]] | ]] | ||
| Line 182: | Line 182: | ||
As all the frameworks, this new design of risk management might find some obstacles, | As all the frameworks, this new design of risk management might find some obstacles, | ||
for instance, the risk analysis in this case could be too expensive, since the large amount of data and the preparation of new risk management. | for instance, the risk analysis in this case could be too expensive, since the large amount of data and the preparation of new risk management. | ||
| − | Furthermore, there are several obstacles to scaling Industry 4.0 beyond the initial, controlled pilot. Connecting disparate and distributed assets still takes too much time, is too complex, and involves too many standards. | + | Furthermore, there are several obstacles to scaling Industry 4.0 beyond the initial, controlled pilot. Connecting disparate and distributed assets still takes too much time, is too complex, and involves too many standards. Also beyond the automation of physical operations, the two biggest obstacles to deploying at scale are organizational rather than technical: |
| − | * Manufacturing managers are used to trusting instincts rather than data. | + | * Manufacturing managers are used to trusting instincts rather than data. a deep cultural change is needed in that managers must adopt a different style, in which they learn to systematically leverage data to optimize equipment reliability and overall supply chain performance. Any manufacturing analytics solution must be able to support this transition to “smart analytics.” |
| − | * Governance has become decentralized but must be balanced between centralization of technology investments and freedom of individual factories. The centralization of expensive technology investment is | + | * Governance has become decentralized but must be balanced between centralization of technology investments and freedom of individual factories. The centralization of expensive technology investment is essential for economies of scale, but factories must be autorized to pilot and adopt new tools. |
| − | More and more companies are transitioning to “analytics factories,” | + | More and more companies are transitioning to “analytics factories,” that support innovation by operational teams while accelerating the development of data-driven management skills. They are also innovating by, for instance, combining their traditional, though somewhat inflexible, Manufacturing Execution System (MES) operational backbone with more agile and flexible analytics on top of IoT platforms - allowing the benefits of data-driven operations. |
== Conclusion == | == Conclusion == | ||
| − | The aim of this article was to | + | The aim of this article was to give an overview of industry 4.0 and understand how risk management could be implemented to follow this “fourth revolution”. |
| − | It can be expected | + | It can be expected that new risks may occur due to changing conditions. The results of this analysis exhibits that the most of common risk factors in the manufacturing area are related to information security. These risks are associated with cyber-attacks, such as the loss of data integrity. |
Moreover, the content of risk management process will change and existing instruments must be adapted. In the case of performance, there is a forecast that KPI and KRI indicators should be found in order to increase sustainability and application of risk management in relation to the performance measurement of companies. | Moreover, the content of risk management process will change and existing instruments must be adapted. In the case of performance, there is a forecast that KPI and KRI indicators should be found in order to increase sustainability and application of risk management in relation to the performance measurement of companies. | ||
| Line 197: | Line 197: | ||
== Annotated bibliography == | == Annotated bibliography == | ||
| − | * ''' | + | * '''Aspects of risk management implementation for Industry 4.0''' This paper has been the starting point to understand the problem and try to solve it. Since it does not give an in-depth image of the Industry 4.0 and risk management, I aimed to better elaborate on these topics. |
| − | * ''' | + | * '''Management approaches for Industry 4.0: A human resource management perspective''' The article provides a very good description of Industry 4.0 and illustrates how management should face up the new technological challenges of Industry 4.0. |
| − | * ''' | + | * '''From Information Security Management to Enterprise Risk Management ''' This report explains how risks are spreading due to new technologies and gives some important details on cyber-security. |
== References == | == References == | ||
<references /> | <references /> | ||
Latest revision as of 22:52, 4 March 2019
Developed by Stefano di Lenardo
Contents |
[edit] Abstract
Nowadays, innovation is synonymous with progress and modernity in every area - from the social sphere, through the educational system, to the economic sphere in science and economy, looking for new solutions that contribute to competitive advantage in the market and thus raise the level of economic and social development and ensure a high quality of life. The vast majority of businesses, are determined to implement product, technical, technological and organizational innovation. But most of all they follow a trend of industrial automation, which leads to the birth of Industry 4.0.
In a few words, Industry 4.0 can be defined as the information-intensive transformation of manufacturing in a connected environment of data, people, processes, services, systems and production assets with the generation, leverage and utilization of actionable information as a way and means to realize the smart factory and new manufacturing ecosystems.
However, new smart technologies and advanced automation require a huge amount of data, which lead the need of new prerequisites, in terms of security systems, in order to avoid any kind of risk. And risk management is the methodical process that involves understanding, analyzing and addressing these risks to make sure that organisations achieve their objectives.[1]
The aim of this essay is to conduct research on Industry 4.0 related to key aspects and presentation of a design of structure to implement risk management for the Industry 4.0 concept.
[edit] Background
[edit] Development of industry from 1.0 to 4.0
Before entering too much deeper into the risk management in Industry 4.0 concept, it is useful to first understand how precisely manufacturing has evolved since the end of 1800s. It is possible to distinguish four different industrial revolutions that the world has known or continues to undergo today.[2]
- The First Industrial Revolution - Mechanization
The first industrial revolution started between the late 1700s and early 1800s. During this period of time, manufacturing changed from focusing on manual labor performed by people and helped by work animals to a more optimized form of labor conducted by people through the use of water and steam-powered engines and other kinds of machine devices.
- The Second Industrial Revolution - Electrification
In the early part of the 20th century, the world experienced a second industrial revolution with the introduction of steel and use of electricity in factories. The beginning of use of electricity allowed manufacturers to considerably improve efficiency and aided make factory machinery more able to be moved easily. It was during this stage that mass production concepts - for instance the assembly line - were introduced as a way to greatly boost productivity.
- The Third Industrial Revolution - Automation
From the late 1950s, a third industrial revolution gradually started to become apparent, since manufacturers began integrating more electronic - and eventually computer - technology into their factories. During this period, manufacturers undertook experiencing a shift that put less emphasis on analog and mechanical technology and more on digital technology and automation software.
- The Fourth Industrial Revolution, or Industry 4.0 - Digitalization
In the past few years, a fourth - and actually last - industrial revolution has sprung up, known as Industry 4.0. Industry 4.0 gives importance to digital technology from recent decades to a whole new level with the help of interconnectivity through the Internet of Things (IoT), access to real-time data, and the introduction of cyber-physical systems (CBS). Industry 4.0 provides a more comprehensive, interlinked, and holistic approach to manufacturing, which authorizes business owners to better manage and understand every aspect of their operation, and enables them to leverage instant data to boost productivity, improve processes, and drive growth.[3]
[edit] Core idea of Industry 4.0
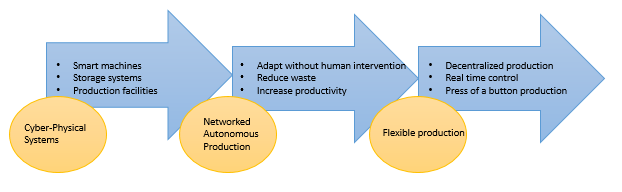
The core idea of industry 4.0 is to implement the Cyber Physical Systems (CPS) for production, i.e. using actuators and sensors, networks of microcomputers, linking the machines to the value chain. It also considers the digital enhancement and reengineering of products. The Figure 1 shows an abstract of industry 4.0 production style. In addition, it is denoted by highly differentiated customized products, and specific combination of product and services, and further the value added services with the actual product or service. After all, industry 4.0 is supposed to have three smart targets: machines, storage system, and production facility. That means minimizing the human interventions and grow productivity. It focus on decentralized and highly automated production, as shown in Figure 1.
One of the easiest examples of sensor networks is RFID (Radio-frequency Identification). Invented to solve logistic problems of army, RFID works via radio waves to read and capture information stored on a tag attached to an object. A tag can be read from up to several feet away and does not need to be within direct line-of-sight of the reader to be tracked. This means that it is possible to know what a pack contains exactly without opening it.[5]
In such an unknown business environment there are many challenges concerning the management approaches, for instance business model innovation, since success in industry 4.0 is due to the innovation capability of enterprise. If organization requires to be smart, they need bright employees, and climate for learning and innovation, which needs appropriate management practices. Management plays a fundamental role for industry 4.0, since the requisite of Industry 4.0 is to develop capabilities across different dimensions in the organizations. There is need to develop capabilities to successfully manage business models, and product portfolio, to access potential market and customers, to intensify value chain processes and systems, legal matters, cultural management -because of globalization- and mostly risk management.
[edit] Risk Management Process
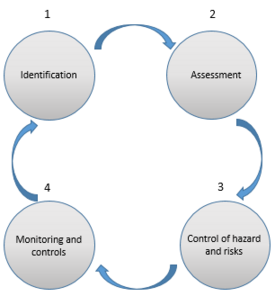
First of all, it is important to define what risk management is and how it works. Risk management in a project management context is a comprehensive and systematic way of identifying, analyzing and responding to risks to achieve the project objectives [6]. The Risk Management Process can be divided into four main categories Identify risks, Assess risks, Treat risks and Monitor risks.
[edit] Identification
During this first process, potential risk events and their characteristics that can have a negative effect on the project are identified. It is possible to repeat this step, as risks can change or new risks are discovered, all over the project's life cycle. The identification process can consist of a variety of different stakeholders, project management team, experts, senior managers, etc.
[edit] Assessment
The second process is "Assessment", which is used to measure and prioritize risks. In this section the probability of each risk and the corresponding impact for the project is verified. Then these two data are used to prioritize the risks. This process is also continual all over the project. Also, for assessing the risks it is possible to use the Risk matrix.
[edit] Control of hazard and risks
It consists of a range of choices for attenuating the risk, evaluating options, and arrangements for implementing action plans. The cost of treating the risk should be obviously assessed and compared with a potential loss by risk. Based on the type and nature of the risk, it is possible to consider these options:
- Avoid - The risk is bypassed by stopping the activity that brought the risk. Alternatively, it can be choose a project that still meets business objectives or a more safety approach or process.
- Reduce - The probability or effect of the risk is reduced to a tolerable level. However, it is advisable to eliminate the risk, according to cost and time.
- Share or Transfer - The risk is shift away from the risk-owner. For example, by outsourcing the activities that the risk is chained to, making agreements with service suppliers or buying insurance that covers that risk.
- Accept - risks with very low probability and effects can often be accepted. Moreover, a risk may be accepted if the cost of the treatment overcomes the benefit. By accepting the risk, all the actions to treat the risk are stopped. The risk is simply still monitored and evaluated steadily, due to potential changes.
[edit] Monitoring and controls
The purpose of this step is to develop activities to track and monitor risks. The most used approach to risk monitoring is the risk register, which is started at the beginning of a project and continuously reviewed and updated. A risk register should at least contain the following information:
- Risk identification number
- Risk Owner
- Description of Risk
- Results of assessment (Probability/Impact) and assessment date
- Mitigating Actions
- Date for next risk review[7]
It is important to outline that risks should be monitored, reviewed and controlled steadily. Risk control is carried out by constantly monitoring the identified risks and identifying and analyzing the new risks. Risks and the effectiveness of controls and mitigations should be assessed throughout the project life cycle.
Moreover, the last few years has seen the emergence of Enterprise Risk Management (ERM), which is often denoted as a new business trend that builds on the principles of traditional risk management. It is a more structured and disciplined approach that coordinates strategy, processes, people, technology and knowledge, with the intent of evaluating and managing the uncertainties the enterprise faces as it creates value.
[edit] Risk management and performance
It is essential for management the performance measurement, since it allows to recognize the difference between contemporary and desired performance and gives the possibility to understand if this difference is going to be reduced. The indicators which help to improve performance are the Key Performance Indicators (KPI) and the Key Risk Indicator (KRI). Through these indicators a specific risk can be constantly checked and they can alert system for upcoming activities. However, there is not any kind of scheme to merge these to indicators and exploit their potential. Indeed, the cooperation between KPI and KRI could allow to find fundamental data for upgrading the achievement of a business and risk management.
- KPIs, or Key Performance Indicators, measure the actions and events that lead to a result, and are considered to be critical to the success of your business as their data is crucial in creating strategies and aligning goals.
- On the other end of the metric spectrum is the KRI, or Key Result Indicator. A KRI measures the results from your business actions, which are critical in tracking progress and defining success.[8]
[edit] Structure to implement risk management
[edit] Risk identification
The purpose of risk identification is to find all the risks that can hinder the achievements of the business. And it is fundamental to identify the risks related to not getting an opportunity as soon as possible, since a risk that is not considered at this stage will not be recognized in remoter risk analysis. As it was mentioned before, industry 4.0 generates new several operational risks, affecting the manufacturing area:
- Manufacturing process management: information risk associated with data losses
- Maintenance: problem with availability and integrity of data for maintenance
- Operational methods and tools used: error data processing
- Machines and manufacturing technologies: sensitivity and vulnerability of data, problem related to cyber-attacks
- Human sources: low number of qualified workers
- Machine environments: attack from Internet network, problems related to electromagnetic compatibility and electromagnetic emissions affecting manufacturing machines[9]
Most of repeated risk factors in the manufacturing are connected with information security. So, it is fundamental to understand how to protect this manufacturing system against cyber-attacks, loss of data integrity or problems related to the availability of information; and the way to achieve that is implementing the information security management system (ISMS). Even if information security is accessible only to who has access, it is critical to consider also integrity and availability. The first one means protecting the reliability and plenitude of information and processing methods. And availability means the possibility to get every data in every moment. Implementing this standard should be the key to solve the problem of security inside companies which follow the Industry 4.0 model. The similarity with other ISO standards is important for building a certified integrated management system based on the management of quality, information and environmental requirements. On the other hand, the standard ISMS can be effectively integrated into ERM.
[edit] Design a structure
The next step is to incorporate and implement the crucial needs for ERM and ISMS. This idea is thought to implement Industry 4.0 concept in manufacturing companies, as it allows to cut down enterprise risks connected with enterprise strategy and the implementation of the certified information security system.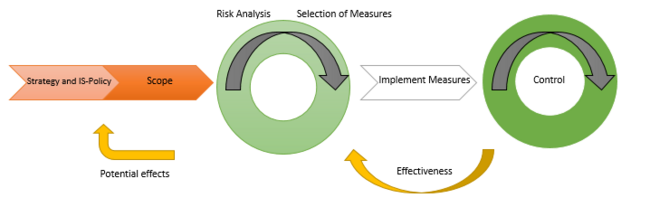
This approach is based on a well-planned analysis tool, called Deming PDCA cycle. PDCA (Plan-Do-Check-Act) is a method for making changes to work processes and improving standards. It is implemented to improve the quality and effectiveness of processes within product lifecycle management, project management, human resource management, supply chain management and many other areas of business. Its activities are:
- Plan-Organizational vision and objectives: Establish policy (including ISMS policy), objectives, processes and procedures relevant to managing risk and improving information security to deliver results in accordance with the organization’s overall policies and objectives.
- Do-Processes: Implement and operate the policy, controls, processes and procedures.
- Check-Performance: Assess and, where applicable, measure process performance against ISMS policy, objectives and practical experience and report the results to management for review.
- Act-Improvement: Take corrective and preventive actions, based on the results of the internal audit and management review or other relevant information, to achieve continual improvement of the system.
Figure 3 exhibits the basic principle and processes of implementation. The article outlines the fact that the security policy must be expanded by risk management aspects to an integrated corporate policy. In this way it is possible to consider the requirements of all stakeholders and to determine appropriate risk objectives and strategies. The focus of an implemented integrated management system should be based on the functional and effective application of business process management, which means that analysis, description and optimization are the core functions to support and management of the processes. The output of the section is an inventory of risks which could be divided into different sections, such as planning risks, processes risks, technical risks.
[edit] Integration of performance and risk management
Risk management should become part of the corporate culture. The institution of business process management can allow to identify risks and choose to take up actions from the risk treatment and business continuity plan. In this way it is possible to appropriately integrate identified risk treatments and business continuity plans in to the manufacturing processes. The effectiveness of the company performance is systematically supported by the implementation, maintenance, testing and uploading of the measures. Risk management in industry 4.0 should embrace concepts from both the fields of BPM (Business Process Management) and PPM (Process Performance Management) and merge them with elements of risk management into a new idea. To do that, some assumptions must be exposed:
- Governance of business processes and examining process risks are essential for risk management based on real-time operational data in Industry 4.0
- To investigate the performance, risk and goal attainment of processes, approaches from BPM, PPM and RM have to be integrated and combined.
- Risks have to be assessed by means of clearly defined data structures and indicators in a designated calculation scheme building upon these structures.[9]
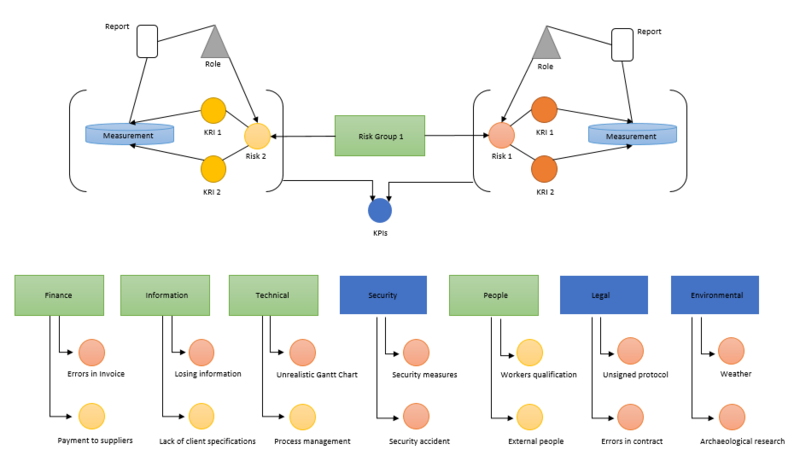
Potential damage types and their probability of happen can be forecasted more exactly, because of the wide-ranging volume of the data from processes. However, the possible scenarios could be very complex and other evaluation procedures might be needed. It is also imaginable an adaptation of the evaluation criteria. As outlined before, each risk can be monitored by the KRIs which influenced the KPIs in connection with the enterprise performance. The concept is in Figure 4, the risks identified were listed in a risk model. This model exhibits the important groups of identified risks and aides to classify them into categories. The different colors used in Figure 4 (to better illustrate the process) divide the risks into: operational (orange) and strategic (yellow) risks. Each risk group may also have a different colour (see Figure 4) f.i. for categorization, priority or responsibility. As shown in Figure 4 each risk group can be broken down into individual risks.
[edit] Limitations
As all the frameworks, this new design of risk management might find some obstacles, for instance, the risk analysis in this case could be too expensive, since the large amount of data and the preparation of new risk management. Furthermore, there are several obstacles to scaling Industry 4.0 beyond the initial, controlled pilot. Connecting disparate and distributed assets still takes too much time, is too complex, and involves too many standards. Also beyond the automation of physical operations, the two biggest obstacles to deploying at scale are organizational rather than technical:
- Manufacturing managers are used to trusting instincts rather than data. a deep cultural change is needed in that managers must adopt a different style, in which they learn to systematically leverage data to optimize equipment reliability and overall supply chain performance. Any manufacturing analytics solution must be able to support this transition to “smart analytics.”
- Governance has become decentralized but must be balanced between centralization of technology investments and freedom of individual factories. The centralization of expensive technology investment is essential for economies of scale, but factories must be autorized to pilot and adopt new tools.
More and more companies are transitioning to “analytics factories,” that support innovation by operational teams while accelerating the development of data-driven management skills. They are also innovating by, for instance, combining their traditional, though somewhat inflexible, Manufacturing Execution System (MES) operational backbone with more agile and flexible analytics on top of IoT platforms - allowing the benefits of data-driven operations.
[edit] Conclusion
The aim of this article was to give an overview of industry 4.0 and understand how risk management could be implemented to follow this “fourth revolution”.
It can be expected that new risks may occur due to changing conditions. The results of this analysis exhibits that the most of common risk factors in the manufacturing area are related to information security. These risks are associated with cyber-attacks, such as the loss of data integrity.
Moreover, the content of risk management process will change and existing instruments must be adapted. In the case of performance, there is a forecast that KPI and KRI indicators should be found in order to increase sustainability and application of risk management in relation to the performance measurement of companies.
[edit] Annotated bibliography
- Aspects of risk management implementation for Industry 4.0 This paper has been the starting point to understand the problem and try to solve it. Since it does not give an in-depth image of the Industry 4.0 and risk management, I aimed to better elaborate on these topics.
- Management approaches for Industry 4.0: A human resource management perspective The article provides a very good description of Industry 4.0 and illustrates how management should face up the new technological challenges of Industry 4.0.
- From Information Security Management to Enterprise Risk Management This report explains how risks are spreading due to new technologies and gives some important details on cyber-security.
[edit] References
- ↑ "https://www.theirm.org/the-risk-profession/risk-management.aspx"/"About Risk Management"
- ↑ "https://www.sentryo.net/the-4-industrial-revolutions/"The 4 industrial revolutions"
- ↑ "https://www.epicor.com/en-us/resource-center/articles/what-is-industry-4-0/"/"What is Industry 4.0—the Industrial Internet of Things (IIoT)?"
- ↑ "https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=7748365/"Management Approaches in Industry 4.0"
- ↑ "https://link.springer.com/chapter/10.1007%2F978-2-8178-0363-0_7/"Electromagnetic Fields, Environment and Health"
- ↑ "https://www.researchgate.net/publication/309727885_Risk_Management_in_Construction_Projects"/"Risk Management in Construction Projects"
- ↑ "https://www.procurementjourney.scot/risk-management-process"/"Risk Management Process"
- ↑ "https://www.dundas.com/support/blog/kpi-vs.-kri-the-difference-and-the-importance"/"KPI vs. KRI - The Difference and the Importance"
- ↑ 9.0 9.1 9.2 "https://reader.elsevier.com/reader/sd/pii/S2351978917304560?token=F83F866783D86D45BBC14332A042092BBDD1615C34061D37074110648C9C8294EDE6C50117DA38E45069E38F0344BB35/"Aspects of risk management implementation for Industry 4.0"
- ↑ "https://www.springer.com/cda/content/document/cda_downloaddocument/9783319067728-c1.pdf?SGWID=0-0-45-1486617-p176729880 "/"From Information Security Management to Enterprise Risk Management"