Risk Log
(→Risk Identification) |
(→Risk Assessment) |
||
| (18 intermediate revisions by one user not shown) | |||
| Line 5: | Line 5: | ||
This article will try to explain '''" How to create Risk Log"''' for an ongoing project by using conventional management tools, mainly Risk management tools and some of the proposals for the subheadings which can be used to create the template for risk log. Moreover, the article will try to show the correlation of different aspect of risk management in the relation of Risk log. Risk log involving various input activities done by Project managers Such as risk identification, Assessment, treatment and monitoring the status of risk at different stages of the project. It is one of the most important alive document that is reviewed and revised throughout the life cycle of the project and in the end, it becomes the historical document for the project and is used for future projects. | This article will try to explain '''" How to create Risk Log"''' for an ongoing project by using conventional management tools, mainly Risk management tools and some of the proposals for the subheadings which can be used to create the template for risk log. Moreover, the article will try to show the correlation of different aspect of risk management in the relation of Risk log. Risk log involving various input activities done by Project managers Such as risk identification, Assessment, treatment and monitoring the status of risk at different stages of the project. It is one of the most important alive document that is reviewed and revised throughout the life cycle of the project and in the end, it becomes the historical document for the project and is used for future projects. | ||
| + | ---- | ||
---- | ---- | ||
===Risk Identification=== | ===Risk Identification=== | ||
| − | Throughout the life cycle of projects, various risks may arrive with different impact on the project in terms of Time, Scope and cost variations. Moreover, the new risks may become foreseen ones as the project progresses and the level of impact on the project may change with the progress of the project. Sometimes the risk may have negative effect defined as ‘Threats’.<ref name=""> Joana Geraldi, C. T. (2017) "How to DO projects"</ref> The Risks should be documented in the Log describing its Service line as per the Work breakdown structure, date of identification and the different stage gate of the project in which it is identified. The Risk Log is the outcome of the risk identification process. In order to identify the risk various techniques and tools can be used | + | Throughout the life cycle of projects, various risks may arrive with different impact on the project in terms of Time, Scope and cost variations. Moreover, the new risks may become foreseen ones as the project progresses and the level of impact on the project may change with the progress of the project. Sometimes the risk may have negative effect defined as ‘Threats’.<ref name=""> Joana Geraldi, C. T. (2017) "How to DO projects"</ref> The Risks should be documented in the Log describing its Service line as per the Work breakdown structure, date of identification and the different stage gate of the project in which it is identified. The Risk Log is the outcome of the risk identification process. In order to identify the risk various techniques and tools are available and can be used, some of them are discussed.<ref name="Fong">Alashwal, A. and Fong, P., 2015, ”Empirical Study to Determine Fragmentation of Construction Projects.”</ref>. |
| − | + | '''Reviewing Documents''' | |
| − | + | Various documents related to the project are reviewed like lessons learned, schedules and any variation in cost estimates and variance related to schedule, scope, and cost.<br> | |
| − | + | '''Interviewing''' | |
| − | + | An interview is conducted with different stakeholders who are involved as consultants and to the experts. As they can identify the risk as per their experience and skills.<br> | |
| − | + | '''Delphi Technique''' | |
| − | + | [[File:DELPHIST.png|200px|thumb|center|'''Figure1:Delphi Technique''' ]]<ref name="Delphi">upload.wikimedia.org/wikipedia/commons/3/35/DELPHIST.png</ref>In this method, some questionnaires are sent to the team of experts and they send the feedback after their review and evaluation of the situation.<br> | |
| − | + | '''Root cause Analysis''' | |
| − | + | In this method, the causes for the risks are identified and these causes are further analyzed for extra risks.<br> | |
| − | + | '''SWOT Analysis (strength, weakness, opportunities, and threats)''' In this analysis situation is identified on the basis of internal factors (strength and weaknesses) and external factors (opportunities and threats)<br> | |
| − | + | ---- | |
| − | + | ---- | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
===Risk Assessment=== | ===Risk Assessment=== | ||
| − | Risks are assessed in terms of its occurrence, impact on the project and key stakeholders. The assessment of risks includes estimating the probability of incidence rate and the corresponding value for project objectives if the risk does occur. We must prioritize with an agreement to the assessment taking into the frame the time, cost and stakeholders and much we should accept it. In most of the cases, the risks are assessed with probability impact score, and this can be only done by an experienced person | + | Risks are assessed in terms of its occurrence, impact on the project and key stakeholders. The assessment of risks includes estimating the probability of incidence rate and the corresponding value for project objectives if the risk does occur. We must prioritize with an agreement to the assessment taking into the frame the time, cost and stakeholders and much we should accept it. In most of the cases, the risks are assessed with PIRA(probability impact risk assessment) score, and this can be only done by an experienced person. |
| − | In this process, the description of risk is needed in the context of its causes and implications to the project and these can be recorded in the log with nomenclature so that it can be compared later. The nomenclature should be very precise and proper causes should be mentioned with a realistic approach, also defining the implications and impacts in terms of capital is favorable as it | + | In this process, the description of risk is needed in the context of its causes and implications to the project and these can be recorded in the log with nomenclature so that it can be compared later. The nomenclature should be very precise and proper causes should be mentioned with a realistic approach, also defining the implications and impacts in terms of capital is favorable as it justifies the most. |
For instance the '''Example''': If ('''event''') occurs due to ('''driver'''), the consequences could result in ('''impact'''). | For instance the '''Example''': If ('''event''') occurs due to ('''driver'''), the consequences could result in ('''impact'''). | ||
| − | [[File:Driver.png|500px|thumb|center|''':''' ]] | + | [[File:Driver.png|500px|thumb|center|'''Figur2 : From Example OF uncertainity''' ]]<ref name="lecture"> MEP slides on uncertainty Course Project Management</ref> |
| − | The Risks can be rated as per its objective in relation to cost, time, scope and quality, on the other side with its likelihood of occurrence and recorded in the log with some numeric or colored representation. Figure | + | Like in the example above the project manager analyze the quality of data available. Moreover, the data is scrutinized in terms of reliability and the integration with the project.<br> |
| − | [[File:2222.png|400px|thumb|center|'''Figure | + | '''Quantitative risk analysis''' |
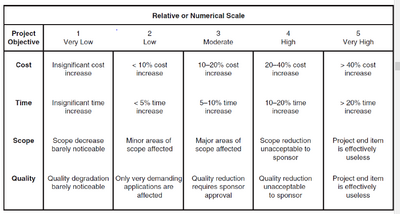
| − | Figure | + | The Risks can be rated as per its objective in relation to cost, time, scope and quality, on the other side with its likelihood of occurrence and recorded in the log with some numeric or colored representation. Figure 3 Shows the classic version of rating the risk on Numerical scale. |
| − | [[File:3333.png|600px|thumb|center|'''Figure | + | [[File:2222.png|400px|thumb|center|'''Figure 3:''' Relative Or Numerical scale for risk impact and likelihood.]] |
| + | By using this kind of analysis project managers can determine the situations which need urgent attention ant its exposure on the project. | ||
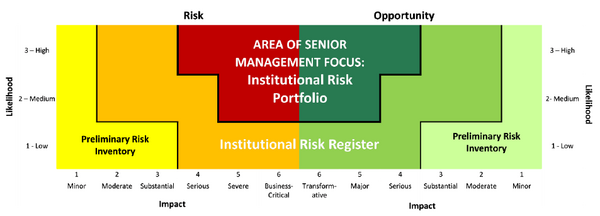
| + | Figure 4 shows the latest version of assessing the risk impact in conjunction with the stakeholder’s involvement. Like in the figure it shows that risks having a high probability of occurrence and critical impact on business are categorized in the red zone and are a concern for Senior management.<ref name=""/> | ||
| + | [[File:3333.png|600px|thumb|center|'''Figure 4:''' Double probability impact matrix]]<ref name="lecture"/> | ||
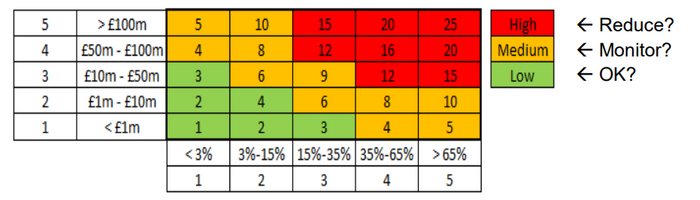
| − | To make it more accurate Probability Impact risk assessment is done based on numbers rating with coded colors it makes easier for Project managers to see the risk and act accordingly with prioritizing the critical ones. For example in figure | + | To make it more accurate Probability Impact risk assessment is done based on numbers rating with coded colors it makes easier for Project managers to see the risk and act accordingly with prioritizing the critical ones. For example in figure 5 we can see the impact is scaled on the basis of numbers set to a different range of cost incurred in risk to that of percentage range for the probability of occurrence assigned to different numbers. |
] | ] | ||
| − | [[File:4444.png|700px|thumb|center|'''Figure | + | [[File:4444.png|700px|thumb|center|'''Figure 5:'''Risk matrix ]]<ref name="fig">www.actuaries.org.uk</ref> |
| − | The rating can be done using this type of matrix | + | The rating can be done using this type of matrix by using a particular number and color assigned as per the different categories as shown in figures above.<br> |
| + | '''Expected monetary value Analysis''' | ||
| + | Similar to Impact matrix and evaluation is done in terms of the Probability and impact. | ||
| + | |||
| + | EMV(Expected Monetary value) | ||
| + | |||
| + | EMV= P x I | ||
| + | |||
| + | P= Probability | ||
| + | I= Impact<br> | ||
| + | '''Monte Carlo Analysis''' | ||
| + | |||
| + | It is a simulation technique analyzing the cost and schedule and does the simulation to give results for the risks. In this method, the activities path is determined and cost analysis for different connected activities are done. it uses the computer-based programme to evaluate the overall risk in the project. It helps in determining any fluctuation in the critical path due to the risk arrived and also gives the probable completion date due to the effect of the risk on the project.<br><ref name="grey">https://www.greycampus.com/opencampus/certified-associate-in-project-management/risk-identification-tools-and-techniques-in-capm</ref> | ||
| + | ---- | ||
---- | ---- | ||
===Risk Treatment and Monitoring=== | ===Risk Treatment and Monitoring=== | ||
| − | Risk treatment is | + | Risk treatment is "a measure that is modifying the risk” it may be a process, policy, device practice or other actions that modify the risk.<ref name="aven">Aven, T. (2010). “On the new ISO guide on risk management terminology. In Reliability Engineering & System Safety”.</ref> In the process of risk treatment more allocation of resource and activities are done into the budget and schedule. It is much favorable in dealing risk if a Risk Owner (Defined as ‘‘person or entity with accountability and authority to manage the risk’’ could be problematic for some risk management practitioners. Internal management allocation of responsibility for risk treatment initiatives does not transfer ‘‘ownership’’ of risk. It transfers obligations to perform tasks to a certain standard and within a certain time frame. While people understand the notion of task allocation and performance obligations, unnecessary confusion may be caused by the notion of risk ‘‘ownership.’’ Moreover, the ‘‘risk owner’’ should not only have the accountability and authority, but also the adequate resources to manage the risk.)<ref name="lajitha">Lajtha, A. D. (2012). ISO 31000 Risk Management— “The Gold Standard”.</ref>is allocated to overcome it, having specialization in respect of the actions needed to be performed. Moreover, the treatment should be effective in terms of cost and time and realistic within the project context and understood by all stakeholders involved. This also involves avoiding the risk by developing a plan, to mitigate the risk, to accept the risk or to make a contingency plan to be used in case of reoccurrence.<br> |
It is very important to control risk and it is done by Tracking the progress of actions taken for identified risks by reviewing the progress and evaluating their effectiveness. Again, the process of identifying new risks, monitoring and assessment should be repeated unless the issue created gets closed. It is mainly performed by weekly or monthly reviewing the progress and rating it in each review so that it is easy to identify the progress in project schedules. It is also very important to overlap the risk log with project schedules so that it is easy for a Project manager to see and react accordingly. | It is very important to control risk and it is done by Tracking the progress of actions taken for identified risks by reviewing the progress and evaluating their effectiveness. Again, the process of identifying new risks, monitoring and assessment should be repeated unless the issue created gets closed. It is mainly performed by weekly or monthly reviewing the progress and rating it in each review so that it is easy to identify the progress in project schedules. It is also very important to overlap the risk log with project schedules so that it is easy for a Project manager to see and react accordingly. | ||
| + | ---- | ||
---- | ---- | ||
===Risk Log Layout=== | ===Risk Log Layout=== | ||
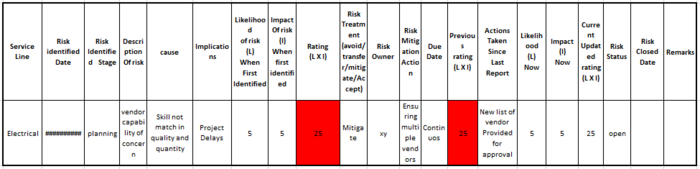
| − | There are many layouts available for the risk log and many companies make it as per their own need and style. However, the basic layout of most of them is alike with many headings and subheadings. In a bigger context for program and portfolio management, there are further headings. Main headings are | + | There are many layouts available for the risk log and many companies make it as per their own need and style. However, the basic layout of most of them is alike with many headings and subheadings. In a bigger context for program and portfolio management, there are further headings. Main headings are described below with example of risk log tempelate in Figure 6: |
• Project name<br> | • Project name<br> | ||
| Line 81: | Line 85: | ||
• Risk closed date<br> | • Risk closed date<br> | ||
• Remarks<br> | • Remarks<br> | ||
| + | [[File:Risk Log Tempelate.PNG|700px|thumb|center|'''Figure 6:'''Risk log Tempelate''' ]] | ||
| − | + | ---- | |
---- | ---- | ||
| Line 93: | Line 98: | ||
• Visualization of risk as an event not as distribution<br> | • Visualization of risk as an event not as distribution<br> | ||
| + | ---- | ||
---- | ---- | ||
| + | |||
===Conclusion=== | ===Conclusion=== | ||
| − | + | Being a project manager it is very difficult to remember all the tasks to be done. So it is favorable to write it somewhere in some kind of format which can be used as a document for risk management in projects. spite of various limitations, this document is base for the risk management processes. Risk management is only an analysis without risk Log. So it can be said that it is a foundation stone for managing risks by any business unit. Risk logs should be properly maintained and reviewed in progress meetings of the project with the required stakeholders so that a low scored risk should not turn into a big threat for the project. | |
---- | ---- | ||
| + | ---- | ||
| + | |||
===References=== | ===References=== | ||
<references /> | <references /> | ||
Latest revision as of 15:32, 3 March 2019
In Projects, the most unavoidable aspect is Uncertainty, even the most proficient Managers faces difficulty to handle it. Various techniques are used by them, like decision milestones to be expected outcomes, risk management for prevention of disasters and some of them uses computational procedures taken from previous projects to get indemnity of Desired deliverables, nonetheless, the project runs out of scheduled time, Increased Budget and compromise with the quality. Or sometimes it may fail.[1]
This variance in projects arrives due to unforeseen and foreseen risks which were not mitigated properly to overcome the consequences. Many Conventional tools and activities are used such as work breakdown structure, Schedules and cost estimate all are proposed to be related to Risk Management. Though, the key management tool is Risk Log/Register. It is a log sheet of identified risks, including results of analysis and planned responses. It is used in a range of project management activities; for example, it is one of the tools to control the project, to document lessons learned, or is used in procurement planning. [2] The Log for Risks is mainly used to document the Unforeseen risks which Come into the picture at the time of the project life cycle. And this document helps To Assess the risks for future projects and makes us prepared in advance for the unforeseen risks which now becomes foreseen risks for the next project and also it is a sheet of a lesson learned during the whole life cycle of project.
This article will try to explain " How to create Risk Log" for an ongoing project by using conventional management tools, mainly Risk management tools and some of the proposals for the subheadings which can be used to create the template for risk log. Moreover, the article will try to show the correlation of different aspect of risk management in the relation of Risk log. Risk log involving various input activities done by Project managers Such as risk identification, Assessment, treatment and monitoring the status of risk at different stages of the project. It is one of the most important alive document that is reviewed and revised throughout the life cycle of the project and in the end, it becomes the historical document for the project and is used for future projects.
Contents |
[edit] Risk Identification
Throughout the life cycle of projects, various risks may arrive with different impact on the project in terms of Time, Scope and cost variations. Moreover, the new risks may become foreseen ones as the project progresses and the level of impact on the project may change with the progress of the project. Sometimes the risk may have negative effect defined as ‘Threats’.[2] The Risks should be documented in the Log describing its Service line as per the Work breakdown structure, date of identification and the different stage gate of the project in which it is identified. The Risk Log is the outcome of the risk identification process. In order to identify the risk various techniques and tools are available and can be used, some of them are discussed.[3].
Reviewing Documents
Various documents related to the project are reviewed like lessons learned, schedules and any variation in cost estimates and variance related to schedule, scope, and cost.
Interviewing
An interview is conducted with different stakeholders who are involved as consultants and to the experts. As they can identify the risk as per their experience and skills.
Delphi Technique
Root cause Analysis
In this method, the causes for the risks are identified and these causes are further analyzed for extra risks.
SWOT Analysis (strength, weakness, opportunities, and threats) In this analysis situation is identified on the basis of internal factors (strength and weaknesses) and external factors (opportunities and threats)
[edit] Risk Assessment
Risks are assessed in terms of its occurrence, impact on the project and key stakeholders. The assessment of risks includes estimating the probability of incidence rate and the corresponding value for project objectives if the risk does occur. We must prioritize with an agreement to the assessment taking into the frame the time, cost and stakeholders and much we should accept it. In most of the cases, the risks are assessed with PIRA(probability impact risk assessment) score, and this can be only done by an experienced person. In this process, the description of risk is needed in the context of its causes and implications to the project and these can be recorded in the log with nomenclature so that it can be compared later. The nomenclature should be very precise and proper causes should be mentioned with a realistic approach, also defining the implications and impacts in terms of capital is favorable as it justifies the most. For instance the Example: If (event) occurs due to (driver), the consequences could result in (impact).
[5]Like in the example above the project manager analyze the quality of data available. Moreover, the data is scrutinized in terms of reliability and the integration with the project.
Quantitative risk analysis
The Risks can be rated as per its objective in relation to cost, time, scope and quality, on the other side with its likelihood of occurrence and recorded in the log with some numeric or colored representation. Figure 3 Shows the classic version of rating the risk on Numerical scale.
By using this kind of analysis project managers can determine the situations which need urgent attention ant its exposure on the project. Figure 4 shows the latest version of assessing the risk impact in conjunction with the stakeholder’s involvement. Like in the figure it shows that risks having a high probability of occurrence and critical impact on business are categorized in the red zone and are a concern for Senior management.[2]
[5]To make it more accurate Probability Impact risk assessment is done based on numbers rating with coded colors it makes easier for Project managers to see the risk and act accordingly with prioritizing the critical ones. For example in figure 5 we can see the impact is scaled on the basis of numbers set to a different range of cost incurred in risk to that of percentage range for the probability of occurrence assigned to different numbers. ]
[6]The rating can be done using this type of matrix by using a particular number and color assigned as per the different categories as shown in figures above.
Expected monetary value Analysis
Similar to Impact matrix and evaluation is done in terms of the Probability and impact.
EMV(Expected Monetary value)
EMV= P x I
P= Probability
I= Impact
Monte Carlo Analysis
It is a simulation technique analyzing the cost and schedule and does the simulation to give results for the risks. In this method, the activities path is determined and cost analysis for different connected activities are done. it uses the computer-based programme to evaluate the overall risk in the project. It helps in determining any fluctuation in the critical path due to the risk arrived and also gives the probable completion date due to the effect of the risk on the project.
[7]
[edit] Risk Treatment and Monitoring
Risk treatment is "a measure that is modifying the risk” it may be a process, policy, device practice or other actions that modify the risk.[8] In the process of risk treatment more allocation of resource and activities are done into the budget and schedule. It is much favorable in dealing risk if a Risk Owner (Defined as ‘‘person or entity with accountability and authority to manage the risk’’ could be problematic for some risk management practitioners. Internal management allocation of responsibility for risk treatment initiatives does not transfer ‘‘ownership’’ of risk. It transfers obligations to perform tasks to a certain standard and within a certain time frame. While people understand the notion of task allocation and performance obligations, unnecessary confusion may be caused by the notion of risk ‘‘ownership.’’ Moreover, the ‘‘risk owner’’ should not only have the accountability and authority, but also the adequate resources to manage the risk.)[9]is allocated to overcome it, having specialization in respect of the actions needed to be performed. Moreover, the treatment should be effective in terms of cost and time and realistic within the project context and understood by all stakeholders involved. This also involves avoiding the risk by developing a plan, to mitigate the risk, to accept the risk or to make a contingency plan to be used in case of reoccurrence.
It is very important to control risk and it is done by Tracking the progress of actions taken for identified risks by reviewing the progress and evaluating their effectiveness. Again, the process of identifying new risks, monitoring and assessment should be repeated unless the issue created gets closed. It is mainly performed by weekly or monthly reviewing the progress and rating it in each review so that it is easy to identify the progress in project schedules. It is also very important to overlap the risk log with project schedules so that it is easy for a Project manager to see and react accordingly.
[edit] Risk Log Layout
There are many layouts available for the risk log and many companies make it as per their own need and style. However, the basic layout of most of them is alike with many headings and subheadings. In a bigger context for program and portfolio management, there are further headings. Main headings are described below with example of risk log tempelate in Figure 6:
• Project name
• Service Area
• Project Manager
• Risk Identified date
• Risk identified stage
• Description of risk: causes and implications on project
• Rating: in terms of likelihood and impact can be done in terms of number or colored
• Risk treatment: Avoid/Mitigate/Accept
• Risk Owner
• Risk mitigation actions
• Task owner
• Due date
• Previous rating
• Risk actions were taken since the last reporting
• Rating: in terms of likelihood and impact can be done in terms of number or colored
• Risk Status: open/closed
• Risk closed date
• Remarks
[edit] Limitations
Risk Log has several limitations and some of them are discussed here:
• PIRA assessment does not give clear predictions and mostly it depends on the experience. So, in some cases assessment may be wrong or overpredicted
• Assessment of risks should be done in conjunction with capital management So as it makes clear to Programme managers while dealing with it and planning for future projects.
• The proper description of risk and companies should have word database for different risks so that it is easy to sort risks
• Visualization of risk as an event not as distribution
[edit] Conclusion
Being a project manager it is very difficult to remember all the tasks to be done. So it is favorable to write it somewhere in some kind of format which can be used as a document for risk management in projects. spite of various limitations, this document is base for the risk management processes. Risk management is only an analysis without risk Log. So it can be said that it is a foundation stone for managing risks by any business unit. Risk logs should be properly maintained and reviewed in progress meetings of the project with the required stakeholders so that a low scored risk should not turn into a big threat for the project.
[edit] References
- ↑ De Meyer, A., Loch, C. H., & Pich, M. T. (2002). “Managing project uncertainty: From variation to chaos”. In V. 43, Issue 2 (pp. 60-67).
- ↑ 2.0 2.1 2.2 Joana Geraldi, C. T. (2017) "How to DO projects"
- ↑ Alashwal, A. and Fong, P., 2015, ”Empirical Study to Determine Fragmentation of Construction Projects.”
- ↑ upload.wikimedia.org/wikipedia/commons/3/35/DELPHIST.png
- ↑ 5.0 5.1 MEP slides on uncertainty Course Project Management
- ↑ www.actuaries.org.uk
- ↑ https://www.greycampus.com/opencampus/certified-associate-in-project-management/risk-identification-tools-and-techniques-in-capm
- ↑ Aven, T. (2010). “On the new ISO guide on risk management terminology. In Reliability Engineering & System Safety”.
- ↑ Lajtha, A. D. (2012). ISO 31000 Risk Management— “The Gold Standard”.