Risk profiles in project management
In construction projects, there are always uncertainty and unexpected situations that may occur. The future cannot be predicted, but preparations can be made for surprises and it can be developed ability to respond to them when they happen. Risk management is a learning process through time, and the risk management is much more inefficient if the duty has not been good from the beginning of the project. During the beginning, there are often high level of uncertainty, so this part of the project life cycle requires greater effectively risk managing. A good risk management approach requires a systematic methodology, knowledge and experience.
This report will address risk profiles. Risk profile can be identified as the acceptable level of risk a company is prepared or willing to accept. The first part of the report will explain risk profiles much more thoroughly, and identify some decision-making criteria’s; risk-neutral, risk averse and risk-seeking. This terms are explained in the report. Then, the structure of a risk profile will be discussed. This will include points that must be investigated to achieve a full risk profile. At the end risk profiles and its limitations will be discussed.
Contents |
Purpose
Companies or organizations are exposed to risk and threats, a risk profile will outline the type of risks, numbers of risks and potential effects of the risks. With this information the organization or company can evaluate the impact on the operation and estimate an additional cost that may come. A risk profile also includes the company’s willingness to take risks and tries to make a plan of how those risks may affect the overall decision-making strategy and how to respond on that effect. It can then be used to reduce the potential threats and risks. The risk profile plays a big role in determining an investment asset allocation for a portfolio. [1]
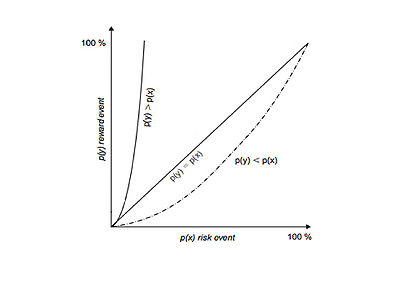
A risk profile can be expressed in a graph as shown in figure 1. The x-axis shows a downside risk event, this can for example be a loss due to an accident. The y-axis shows an upside risk event, this can for example be a profit on a contract. Figure 1 represent a model of risk propensity for known knowns. Known knowns is a cognitive condition of risk, where the risk source is identified and the occurrence of a risk event can be assigned a probability given the risk source. A risk profile represented by a graph as in figure 1 can also be given for known unknowns, which is a cognitive condition of risk where the risk source is identified but the probability of the occurrence of the risk event cannot be assigned. For unknowns unknowns, cognitive condition of uncertainty where the risk source is not identified, and therefore the risk event cannot be known, cannot be drawn in a model of risk propensity. This is simply because decision-makers cannot have an appetite for something they do not know about. [2]
Usually, a greater risk for an investment is associated with a greater return. That is why some decision-makers have a larger “appetite” for risks that they are willing to accept, looking for a greater return. This type of behaviour from a decision-maker can be divided into three main groups; risk-neutral, risk averse and risk-seeking. Risk-neutral is represented in figure 1 as the straight line at 45 degrees, here the decision-maker are indifferent between the chances of reward event and risk event occurring; p(y)=p(x). Risk averse is represented as the upper line in figure 1. Here, the decision-maker’s willingness to invest decreases rapidly as the probability of a risk event increases; p(y)>p(x). Risk averse decision-makers do not make the investment, or they are not prepared to pay additional to reduce either the magnitude of losses associated with the downside risk event or the probability of it occurring.
The lower line in figure 1 represent risk-neutral. When a decision-maker is risk-neutral they can be called for gamblers. Here, p(y)<p(x). The willingness to gamble slowly reduces as the probability of a risk event increases. [2]
To be able to make a risk profile, it is important to identify the risks. In construction projects, risks can be identified within the following categories; management, technical, schedule, cost, environment, safety and health. An example for a risk within the management category can be that a proper mix of people with the right experience and skills are not assigned to the project, or that a effective risk assessment has not been preformed or the results from it is not understood and then acted upon. A risk within technical can be that the technology that is to be used in the project has not been demonstrated in required operating environment. For schedule and cost, an example may be that the schedule or the funding profile do not match the acquisition strategy or planning.
[3]
When making a risk profile, the acceptable level of willingness risk needs to be established. For a company, it is very important to be proactive with its risk management system. If risks are properly accounted for, some of them may be minimized or totally eliminated. To do so, companies often create a compliance division. Compliance helps to ensure that the company and its employees follows regulatory and ethical processes. Many companies hire independent auditors, they help discovering risks and make sure that the risks get properly addressed before they become an external issue. If this fails, it may lead to big consequences as; lower revenues, falling stock price, a bad public image of the company and in worst case bankruptcy. [1] In some cases, accepting the risk can be an option. This occurs when the cost of managing a type of risk is accepted, as the risk is not enough to warrant the extra cost it takes to avoid the risk. For businesses it is normal to identify and prioritize risks using risk management techniques. Using the technique, the business can then minimize, monitor and control the risks, and then see if some risks can be accepted given that the cost of accepting is smaller than the cost of preventing. [1]
There is often friction between business leaders and information risk management security (IRMS) professionals when making a risk profile. The business leaders can often be more risk-seeking, embracing the need to take risks to achieve business goals. IRMS professionals are on the other hand often more risk averse, they minimize risks and tries to ensure their organizations information infrastructure are properly protected. Business leaders may see IRMS professions as an obstacle in their way to success, as IRMS processionals may see the business leaders as someone that are not informed enough to understand the value of their activity or work. To avoid friction and make the process of making a risk profile easier, the business leader and the IRMS professionals should try to develop together a risk profile that both can use as a guide for their respective activities at the beginning of the process. The risk profile is developed with numerous stakeholders in the organization, including business leaders, IRMS, data and process owners, internal and external audit, compliance and enterprise risk management(ERM).
ERM is an important concept within many organizations, their function can leverage information in the risk profile as it calculates overall risks and control, monitor and manage them. [4]
Structure of a risk profile.
The risk profile of an organization should be structured so it is easily understood and applicable, its value and intent is quickly demonstrated, and is useful and beneficial to the organizations leaders and stakeholders. To achieve this, the following points must be investigated. [4]
Guiding principles and strategic directives.
The organizations guiding principles and strategic directives has to be listed early in the profile so that the reader can understand its intent. The guiding principles has to provide accurate evaluation of threats, vulnerabilities and their risk, helping business leaders to make risk management decisions. They have to ensure that the risk-minimizing controls are functional and align with the organizations risk tolerance, and that both funding and resources are divided to ensure highest level of risk minimizing. [4]
Information risk profile development.
An important factor for a successful risk profile is transparency. If methods, source materials, intelligence and individuals involved is not provided in the document, it may damage the profiles credibility. This information may be added in the document as part of an appendix and include links to the material. [4]
Business-state representation of risks.
The risk profile should provide a current-state analysis of identified risks that have a high probability of occurrence and would have a big effect on the business if they were to occur. It should also include the organizations risk management expectations and requirements, their views on risk and security, current vulnerability and threat analysis and expectations from external parties. This part of the profile should have a language understood by both technology-and business-oriented staff. [4]
Future-state objectives and requirements
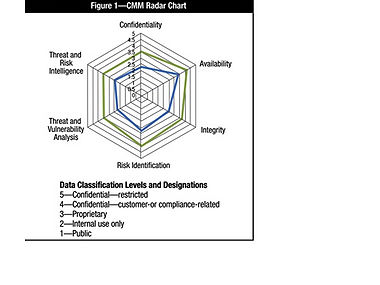
The future-state objectives and requirements consist of general information concerning risk tolerance and appetite, and an ideal state of the organizations risk management. It should include the key IRMS initiatives that has been decided and set in motion and those initiatives that are about to be set in motion. The key initiatives consist of a summary of the initiatives owners, a timeline for completion and expected level of risk minimizing at chosen states during the timeline and at the completion. The future-state objectives and requirements can be represented using a capability maturity model(CMM). This model makes it easy to identify the organizations areas that needs focus, service and investment, and the areas capability. One way to represent this model is by using a radar chart format shown in figure 2. This approach makes it easy to communicate the information in a understandable way. [4]
Key business processes and capabilities.
Organization have often many business processes and with that limited resources to protect them. The key business process and capabilities that can impact the risk profile in a negative way are important to identify at an early stage. A negative impact could affect the business operations, causing a material impact. These can be divided into two groups; production and business support functions. An example in production can be contract requirement, and an example in business support functions can be payroll and benefits. An easy source to list these processes and capabilities is to take it into the disaster recovery plan. In this plan they get ranked after their level of importance to the organization, the risk calculation often takes into account the recovery time and recovery point objects. [4]
Key data elements
The risk profiles include identification and definition of key data elements. Key data elements often include sensitive data as for example transaction data, non-public personal information, human resource information, customer data and financial data. This ensures that the risk profile can provide a clear understanding of the data element and its value to the organization. [4]
Identification of data owners and stakeholders
Identification of data owners and stakeholders is important as these are responsible for their risk management decisions. This could also help identifying the dependency that can affect the risk appetite for data assets, especially when one or several business processes are required. All data in an organization should be correlated to a data owner and stakeholder. [4]
Identification of business value
The identification of business value should be based on meaningful analysis and calculations, and not subjective opinion from data owners where the information often gets misunderstood. In risk management a general rule is that the cost to protect the information should not exceed its value. It can be difficult to find the value of information from identifying and monitoring the data assets. To make it easier, the value is found by identifying and monitoring the value of process instead. This process can be connected to the organizations activity. The risk profile does not, as explained, need to find the exact value from the data assets, but it does need to establish a general representation of the value, so that the level of control and classification can be identified. [4]
Data classification schema
The data classification schema classify data in containers, it should be simple and straightforward in order to be useful to the risk profile. Its job is to simplify information management. The data classification scheme should contain three to five levels of definition, and they should get stronger and more comprehensive control objectives and requirement as they ascend. In addition to the data classification schema it should also include a summary of the control requirements. [4]
Risk levels and categories.
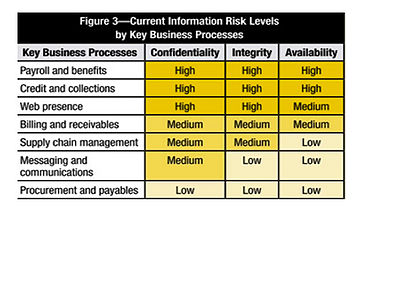
In order to organize and communicate information risk in a simple format, a framework provided by risk levels and categories can be used. The risk levels and categories should be simple and understandable. The risk levels represent a scale of levels of impacts resulting from different risks if they were to be realized, the categories define the type of impact. An example of level setting and categorization represented in a heat map is shown in figure 3 below. [4]
The information risk levels are defined as:
- High:
- Severe material compliance. There will be financial and/or legal consequences which will lead to a significant impact on the critical business processes, and both the costumers and their trust may be lost. The reputation of the business brand will be damaged.
- Medium:
- Significant material compliance. There will be financial or legal consequences which will lead to a substantial impact on the key business processes, and both the costumers and their trust will be weakened along with the reputation of the business brand.
- Low:
- Negligible or no material compliance. There may be financial or legal consequences which will lead to a minimal impact on the critical business processes. The customers trust and the reputation of the business brand will experience an insignificant change.
And the risk categories are defined as:
- Confidentiality:
- Acknowledgement of sensitive information to unapproved people.
- Integrity:
- Impact of the accuracy of information and data
- Availability:
- Effect on the ability to access information and data. [4]
Limitations
As seen, a risk profile is very important for a construction projects to prepare for risk and threats that the project may be exposed to. Some decision-makers may prioritise risk tolerance too heavily over capacity for risk. [5] A greater risk often implies a greater return, and the type or behaviour from the decision-makers will have a great impact on the risk management. If the decision-maker is a risk-seeker, he may underestimate the risks, and then experience severe material compliance. If the decision-maker is a risk averse, he may be too conservative, using a lot of expenditure on risk preventing that may not be needed. There are no correct answers, but there are some answers more correct than others. Models are really helpful and makes the process easier. When using information risk management security professionals, there may be some conflict with the business leaders, as mentioned. To avoid this there is important to keep an open communication line from the start, and to show some understanding for each other.
References
- ↑ 1.0 1.1 1.2 [1]
- ↑ 2.0 2.1 Winch, Graham, M., 2010, Managing Construction projects, second edition
- ↑ SLAC (2009). RESEARCH SUPPORT BUILDING AND INFRASTRUCTURE MODERNIZATION, RISK MANAGEMENT PLAN.. https://www-ssrl.slac.stanford.edu/lcls/reviews/rsb_project/2009_rsb_may18-19/supporting_docs/rsb_risk_management_plan.pdf. (04-2009)
- ↑ 4.00 4.01 4.02 4.03 4.04 4.05 4.06 4.07 4.08 4.09 4.10 4.11 4.12 [2]
- ↑ [3]
- ↑ Norman, T (2014). How do advisers sort the good risk-profiling tools from the bad?. https://www.moneymarketing.co.uk/how-do-advisers-sort-the-good-risk-profiling-tools-from-the-bad/. (24-11-2014)
Annotated bibliography
- 1. Investopedia, “Risk Profile".
- Summary: This link identifies risk profiles
- 2. Winch, G. M., 2010, Managing Construction projects, second edition
- Summary: Gives an explanation of risk profiling, identifies different types of decisions-makers; risk-neutral, risk averse and risk-seeking. Gives a model of risk propensity.
- 3. John P. Pironti, Isaca, 2013 “Key Elements of an Information Risk Profile".
- Summary: This link shows the structure of a risk profile.