Risk identification methods
Contents |
Abstract
"risk" -Noun “A situation involving exposure to danger”
With every action performed there is a potential risk, regardless of the size, however, the chance of the risk being a problem can be mitigated. For every type of organization, it is most likely that they have in one way or another, implemented the use of risk management. Risk management is a crucial tool in order to identify and quantify the positive and negative risks, as well as avoiding risk outputs and even being able to reduce the risks before they are present. This should be followed by coordinated and economical application of resources to minimize, monitor, and control the probability or impact of unfortunate events [1] or to maximize the realization of opportunities [1]. Risk identification is a crucial part of any project, and one of the steps involved in risk management, which is the identification, evaluation, and prioritization of risks (defined in ISO 31000 as the effect of uncertainty on objectives).
The goal of risk identification is to gain prescience of events that, if they occur, can have an impact. This could be negative impacts on which could lead to the ability to succeed is diminished or it could be causing a decline in the efficiency. It could however also be positive risks that can potentially lead to increase in efficiency or effectiveness. In this article the overall risk framework is mentioned, and the essence of the article is how risk identification is, in accordance with the type of assessment necessary to support the risk-informed decision-making process [2].
The first step of risk identification is to identify the goals and objectives, thus creating a shared understanding of what is crucial for a successful completion across all team members. This creates the necessary knowledge and the scope, which is necessary in order to identify and assess risks.
There are several methods to identifying risks, which will all be enlightened briefly in this article. For a more detailed explanation of the methods, please see the wiki page for that specific method.
[[1] Threat Assessment and Risk Analysis, An Applied Approach 2016, Gregory Allen, Pages 55-61] [[2] Hubbard, Douglas (2009). The Failure of Risk Management: Why It's Broken and How to Fix It. John Wiley & Sons. p. 46.]
Introduction
As mentioned above risk identification is a part of risk management, but what is risk management?
“Risk management comprises coordinated activities to direct and control an organization with regard to risk”
Risk management serves the purpose to ensure there are enough measures taken to protect the environment and assets from harmful consequences. In order to keep control of the risks, companies establish a risk management framework. This risk management framework should comply with the risk management principles, to be complete and underly the principles of risk management (3).
The risks should be precisely understood and managed in a systematic and effective way, it means that there are techniques used to minimize and prevent accidents from happening, which could cause harm and unwanted situations (4).
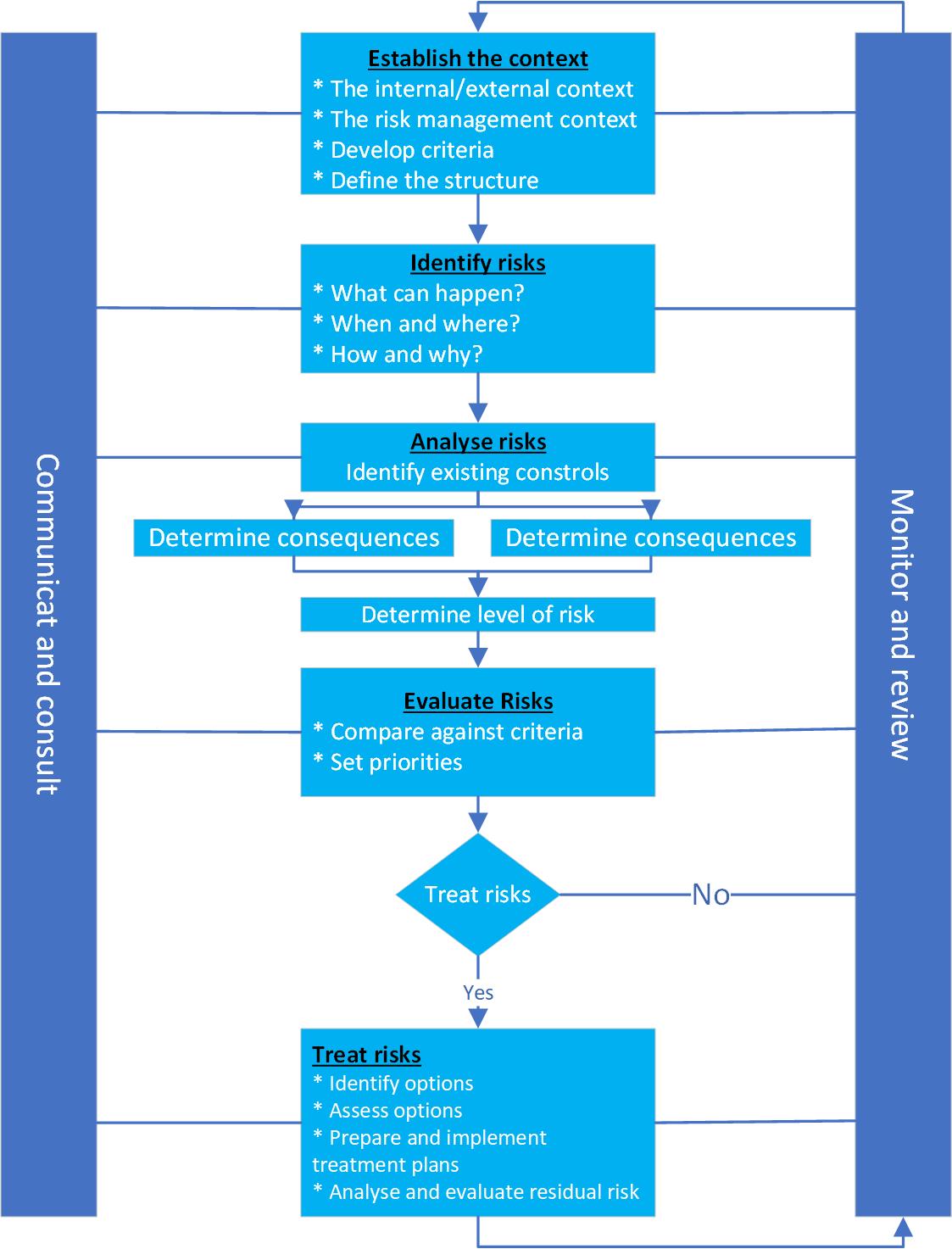
In risk management according to ISO 31000, risk management process are used to control and manage the risk, see below:
(Contents and layout is from the course: 42172: Risk and decision making, day 2: Overview of risk principles.pdf In the illustration there are a total of 5 steps (see illustration below):
1. Establish the context
2. Identify risks
3. Analyze risks
4. Evaluate risks
5. Treat risks
On the side bars: “Communication and consult” and “Monitor and review”. Step 2-4 is risk assessment and we will not go through all steps, we will mainly take step 2-4, and briefly about step 5.¨
Risk identification is an imminent topic in in general. Risk is the potential of something that could go wrong and resulting in causing harm or loss. Talking about harm or loss, it could be either about living creatures or inanimate objects. To understand risk even more deeply, there are elements that should be understood, namely:
- A risk – Is the likelihood of an incident and its consequences asset
- An incident – Is an event that harms or even reduces the value asset
- An asset – Is anything that has a value to a group or a party
- A party – Is a company or an organization, even a group
- A likelihood – Is the chance of something that would occur
- A consequence – Is the impact of whatever incident on the asset that results in harm or reduced value
- Risk level – Is the level of a risk which derived from its likelihood and consequences
Risk identification
Risk identification means that you carry out some activities that helps identify, describe and document the risks and the possible causes of the risks. Usually in the present, it is not only about identify the risks, but also how to navigate around it and even trying to neutralize it, in short, actions should be taken. The risk identification goals are to provide with information about whatever events that could go wrong and impact or disrupt an aspect of businesses (5). There is not a right or wrong when identifying and categorizing risks, many companies and organizations have their own ways and methods of doing so. The purpose for identifying the risks is to know where they are and how they are spreading, all depending on what industry and type of organization you are working with, you are able to see whether we are seeing high risks in a specific part or product? All depending on in what type of project or organization the risks are needed to be identified, different methods apply.
Ways to identify risks: There are several ways to identify risks, below are a few methods mentioned, please notice that many of these methods not only identifies the risk, but is also containing the next steps in the risk assessment (6):
- Brainstorming, Silent Brainstorming: The idea is to gather a group, and everybody are given x number of minutes to sit and brainstorm individually what could go wrong, on whichever process you have decide to look upon. It can also be used to storm for causes or consequences of a current problem. Thereafter, you take turns to talk about what you have on the different processes, and thereby filling whatever holes there may be, of course the ones that are coming twice or more times, should just be there once. Brainstorming is a method to get any types of ideas, thinking outside of the box. It is a very free-minded method where you get many different types of inputs to the project.
- FMEA: Is a risk assessment tool which stands for Failure Mode and effects analysis; this method could be seen as more of a method which is used for medical devices or machinery, automotive and much more, but more component-based projects. The idea is to create a table where you have different column, such as components and assigns them point according to the risk to the customer, the likelihood of the risk to happen and the consequences of the risk.
- HAZOP: stands for Hazard and Operability Study, it works by studying item by item of a whole plant. Each of these items are measured for disturbances, and these disturbances are categorized by cause and consequence which are studied. Existing safeguards and measures are identified and registered.
- Event tree: are used to visualize and categorize the results of a hazard identification. It is a way of creating an overview of the hazard and the possible and potential causes. This can be used in case of the hazard also as a elimination method. This is mainly focused on “errors” that can lead to the hazard and maybe not focusing on external unforeseen factors.
- SWIFT: stands for structured what-if technique. This technique is a mixture of brainstorming, check lists and has the documentation method of FMEA/HAZOP. It is a method which is strong in many different types of cases if the check lists are performed systematically and are well rounded. It has the free rein of the brainstorming but can be stronger if the structural setup is at point.
- RCA: stands for Root Cause Analysis and are usually used when finding the cause of an incident/risk. This is also a method of identifying a risk but are usually used when the incident has happened and looking back.
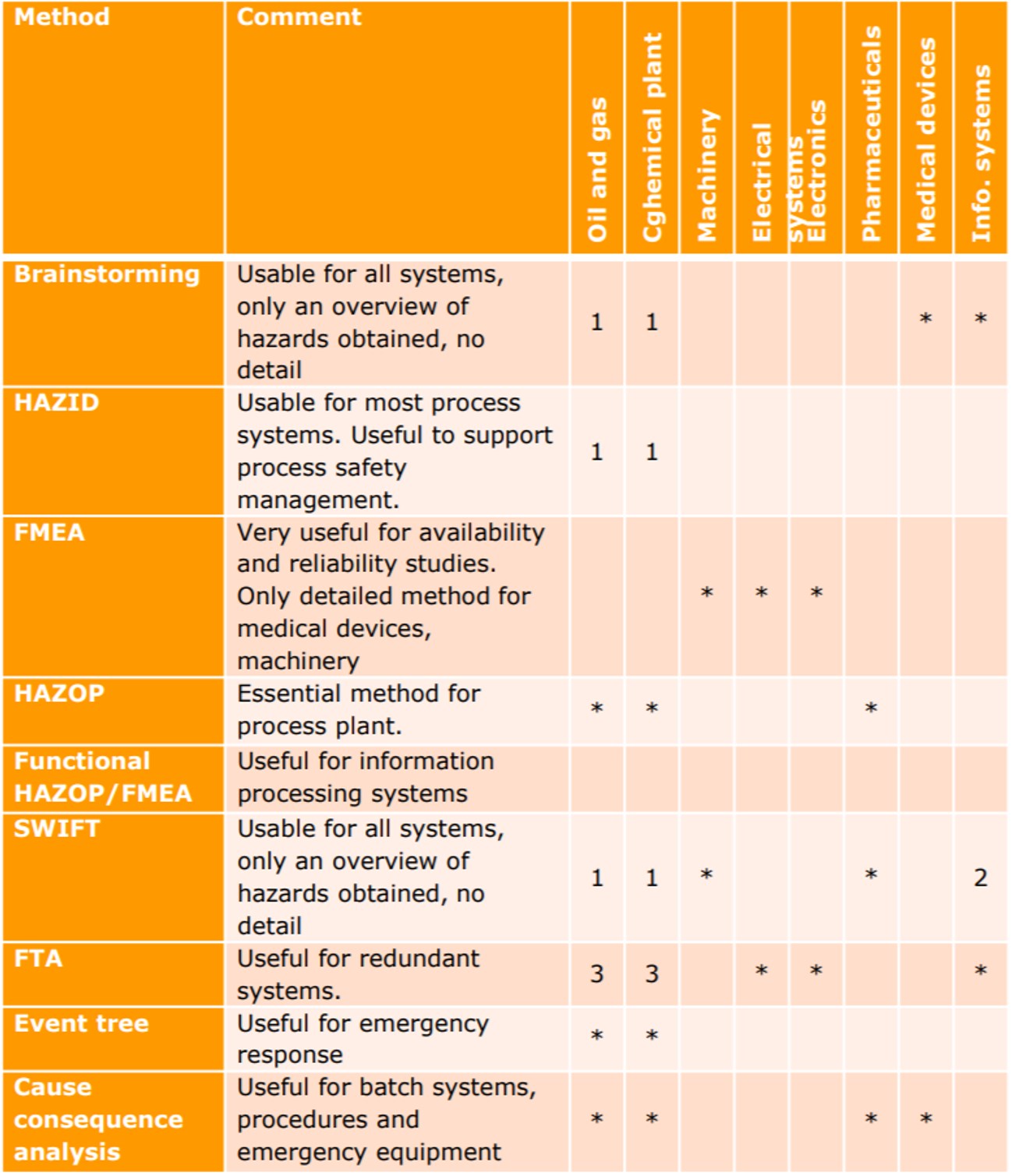
Not all of the methods are applicable in every setting. Below is a table showing where the methods are applicable and which type of system they are best at.
Risk analysis, evaluation, assessment and treatment
In the next step, risk analysis you are assigning a level of impact/likelihood of the risk to happen, usually by a scale 1-10 or 1-5. In this part you also register the consequence of the risk. Hereafter are you evaluating on the risk, you decide how much of an impact the risks have compared to each other, this is used for example to learn where the hazardous or critical risks are, also to know where to put your resources and to decide which risks would need a treatment. Last but not least is the risk treatment, here you apply the treatments of the risks and records the decisions made and responsibilities (3).
The methods mentioned above can be used to first identify the risks, and thereafter can we analyze these risks with the methods describing the cause, consequence and the likelihood of the consequences. In some these methods we do not only identify them but can go through the whole process of risk assessment which contains: risk identification, risk analysis and risk evaluation. A method like brainstorming is only used to identify the risk, therefore, it is not considered a method for risk management/assessing the risk. The methods FMEA and HAZOP are both identifying, analyzing and assessing the causes and consequences of the risk/hazard. FMEA and HAZOP are component/item based which makes them inapplicable to all scenarios with risks, whereas brainstorming and SWIFT are both broadly applicable. When the causes and consequences are found, they can be rated (Evaluation) and thereafter the current safety measures are registered/taken into consideration, the question is now – are they good enough, or are the risks simply too big? (Assessment). If the answer is no, the next step is to find a way to mitigate the risk (Treat the risk).
Risk monitoring and review
Are crucial to do during the risk assessment, because causes and consequences as well as the likelihood can change over time. Therefore, it is important to update the risk cycle regularly to avoid outdated data from the risk assessment. Different things can affect the risk which leads to the monitoring and reviews being necessary.
There may be changes in:
• Organizational context (for example, objectives, the internal or external environment or risk criteria.)
• Risks and levels of risk.
• The effectiveness of risk treatments. (7)
The changes may be instant or gradual and all can have a high impact of the consequences, causes and treatments, therefore, after any type of change it is recommended to do-over the risk assessment or identify new risks.
(3) https://link-springer-com.proxy.findit.dtu.dk/content/pdf/10.1007%2F978-3-319-23570-7.pdf (4) https://link-springer-com.proxy.findit.dtu.dk/content/pdf/10.1007%2F978-1-84628-653-7.pdf (5)http://production.datastore.cvt.dk/filestore?oid=5a14390a5010df36af5627b6&targetid=5a14390a5010df36af5627ba (6) https://cn.inside.dtu.dk/cnnet/filesharing/download/d97e81d1-acbe-4c8a-ba62-dff5a267aef8 Course 42172: Risk and decision-making Day 2-3 Hazard Identification (7) https://cn.inside.dtu.dk/cnnet/filesharing/download/a433c6b6-31bc-46a0-8798-05d26522a7cf