Managing threats and opportunities in risk treatment
(→Overview of The Risk Management Process) |
(→Overview of The Risk Management Process) |
||
| Line 46: | Line 46: | ||
# '''Communication & Consultation''' <br | # '''Communication & Consultation''' <br | ||
| − | /> The purpose of communication and consultation is to share relevant information with identified and relevant stakeholders. There must be close coordination between the stakeholders to ensure a shared understanding of the project's scope and criteria. The purpose of this phase is to bring stakeholders together with different expertise and ensure that there is enough information to facilitate sufficient risk overview and decision-making. However, it is also important to ensure that the different points of view are appropriately considered when defining risk criteria and when evaluating risks. Kommunication and consultation will result in a focus on the project's scope, context and criteria. <br | + | /> The purpose of communication and consultation is to share relevant information with identified and relevant stakeholders. There must be close coordination between the stakeholders to ensure a shared understanding of the project's scope and criteria. The purpose of this phase is to bring stakeholders together with different expertise and ensure that there is enough information to facilitate sufficient risk overview and decision-making. However, it is also important to ensure that the different points of view are appropriately considered when defining risk criteria and when evaluating risks <ref name=ISO31000_2018/>. Kommunication and consultation will result in a focus on the project's scope, context and criteria. <br |
/> <br | /> <br | ||
/> | /> | ||
Revision as of 20:04, 19 February 2023
Developed by Theis Rosenkvist Sørensen
Risk treatment is the final stage in the risk management process. It is used to control and monitor the uncertainties during the project. When managing a project, uncertainties are one of the most important factors to control in order to achieve a successful project. Uncertainties occur when certain events in a project are unpredictable and it will only be possible to guess about a future event. Risk management is used to identify risks in the project that help maintain stability and used to prevent unforeseen events that can be cost, resource or time consuming. By using risk management, it is possible to ensure that the project team achieves the goals they are solving by not encountering many unpredictable obstacles during the project.
The risk management process is a seven-step iterative process: Communication & Consultation, Establish Context/Scope/Criteria, Identify Risks, Analyze Risks, Evaluate Risk, Risk treatment and Monitoring & Review [1]. This is done throughout the projects lifetime. By managing the project using responses to threats and opportunities, it becomes possible to minimize the impact of the risk. If it can be done in a successful way, better risk management is achieved and it will thus be possible to reduce the impact of the uncertainties in the project. By using Rumsfeld matrix, it becomes possible to reduce the risk by establishing precautions that can prevent or reduce the uncertainties from arising.
When working with risk treatment, there are some limitations. One of the crucial limitations is the lack of knowledge sharing. The lack of knowledge sharing leads to a greater amount of uncertainties that could have been prevented. However, not all uncertainties can be prevented and even perfectly planned projects have their limitations. By having a greater amount of expertise, a higher level of risk treatment can be performed and will minimize the risk by identifying crucial uncertainties in the project.
This paper aims to highlight the importance of the risk management process and more specifically delve into risk treatment process.
Contents |
Introduction
The Risk Management Process
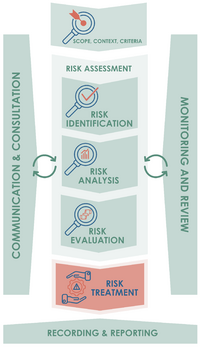
Risk management is a process that works to manage risks to ensure that it cause the least impact in the project. Risk management is based on assumptions and experience from previous projects. However, many assumptions are uncertain which can have an effect on the project's original scope. The Project Management Institute (PMI), describes risks as "An uncertain event or condition that, if it occurs, has a positive or negative effect on one or more project objectives" [2]. By successfully navigating the uncertainty, risk can be managed in a way that is most beneficial to the project scope.
The process involves a "systematic application of policies, procedures and practices to the activities of communicating and consulting, establishing the context and assessing, treating, monitoring, reviewing, recording and reporting risk" [1]. It should be noted that there can be many different applications of the risk management process, as it can be adapted to a particular project to achieve specific goals within the organization.
When operating the risk management process, take into account that the process is an iterative approach and it is important to go back and assess whether there have been changes in the previous stages that could create new potential risks that the project manager needs to adapt in their risk assessment. The stages are illustrated in Figure 1 [1].
Knowledge and awareness
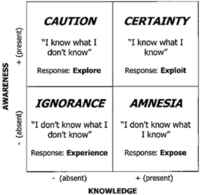
David Hillson describes the difference between risk and uncertainties. He states that "risk" has a set of possible outcomes that are known, but that the precise outcome is not known in advance. In contrast, uncertainties relates to a lack of knowledge about the possible outcomes and are thus an unknown event from an unknown number of possible outcomes [3].
Based on these descriptions, the relationship between risk and uncertainty can be described as:
"Risk is measurable uncertainty"; "Uncertainty is unmeasurable risk" [3].
Another way to distinguish the relationship between risk and uncertainty is by looking at the relationship between knowledge and awareness. Figure 2 illustrates four quadrants where knowledge and awareness are either present or absent. The figure is a similar concept to the Johari Window, which describes self-awareness and perception by others [3]. The top right corner of the quadrant certainty is illustrated, where both awareness and knowledge are present. An example could be a known number of square meters on which a building must be built or the appearance of the building so that it fits a certain cityscape. The top left corner illustrate caution, which describe the things that are uncertain. This could be, for example, the weather conditions next week. Under certainty we have amnesia which describes the lack of awareness or a blind spot regarding the knowledge we have. An example of this could be, bad planning, poor communication or acting on intuition and biases. The project manager can practice self-awareness to identify them. The last quadrant is Ignorance, where "we don't know what we don't know". An example of this could be the beginning of a war or an unpredictable natural disaster.
Donald Rumfeld's Unknown-unknowns
The knowledge and awareness figure created by Hillson and the Johari Window is a comparison to the known description used by the former U.S. Secretary of Defense Donald Rumsfeld at a press conference in 2002. He described the types of uncertainties as:
"Reports that say that something hasn't happened are always interesting to me, because as we know, there are known knowns; there are things we know we know. We also know there are known unknowns; that is to say we know there are some things we do not know. But there are also unknown unknowns – the ones we don't know we don't know" [5].
This statement became known as Rumsfeld matrix when the author Mikael Krogerus refers to it in his book "The decision book : fifty models for strategic thinking" [6]. Figure 3 illustrates the connection between Hillson's Knowledge and Awareness figure & Rumsfeld Matrix[4].
Overview of The Risk Management Process
The risk management process is a seven-step iterative process, which can be seen in figure 1. The process is described below in proper order.
- Communication & Consultation
The purpose of communication and consultation is to share relevant information with identified and relevant stakeholders. There must be close coordination between the stakeholders to ensure a shared understanding of the project's scope and criteria. The purpose of this phase is to bring stakeholders together with different expertise and ensure that there is enough information to facilitate sufficient risk overview and decision-making. However, it is also important to ensure that the different points of view are appropriately considered when defining risk criteria and when evaluating risks [1]. Kommunication and consultation will result in a focus on the project's scope, context and criteria.
- Scope, Context and Criteria
asdasd
- Risk identification
asdasd
- Risk Analysis
asdasd
- Risk Evaluation
asdasd
- Risk Treatment
asdasd
- Monitoring & Review
asdasd
Ref:
Hillson, David. "Effective Opportunity Management for Projects - Exploiting Positive Risk", 2003. Ch. 1. "The case for opportunity management". Marcel Dekker Inc.
Forsberg, K., & Mooz, H. RISK AND OPPORTUNITY MANAGEMENT. (1996). INCOSE International Symposium, pp. 586–598. Retrieved from https://doi.org/10.1002/j.2334-5837.1996.tb02057.x
[7].
Risk Treatment
The importance of risk treatment lies in the fact that risks are decisive for whether a project will be a success or not. By not managing the risks, the consequence can be fatal. Barry Boehm states the consequence as "If you don’t actively attack the risks, they will actively attack you" [8]. Risks can be both threats and opportunities as they can have either a positive or negative impact on the project. This section will describe the response strategies to threats and opportunities.
Threats
Threats are uncertainties and unexpected events that can effect the project negative and threaten the project scope. When reacting to threats as an approach to the Risk Management Process, it becomes possible to reduce the impact to zero by either avoiding, reducing or transferring the risks. Threats can be divided into five categories; Avoid, Transfer, Mitigate/Reduce, Accept, Escalate.
Avoid
Threat avoidance is when the project team seeks to eliminate the uncertainties by making it impossible for the risk to occur or protects the project from its impact by executing the project differently so that the objectives are achieved but avoids the risk so that it has no impact on the project [9].
Transfer
By transferring the risk, another stakeholder is identified who is better at managing the risk and is responsible for the right action being taken. They are therefore responsible for bearing the risk if it occur [2]. This can be done when the project manager acknowledge his lack in expertise and wants a third party to manage the risk.
Mitigate
When mitigating the risk, action is taken to reduce the impact of a threat or reducing the probability of occurrence. Reducing the size of the risk in early stages will make it more acceptable to the project. "Early mitigation action is often more effective than trying to repair the damage after the threat has occurred" [2].
The goal of the threat is to acknowledge its existence and deal with it so that it does the least damage to the project. For this, an Impact matrix can be used for the threat, and can be used to take proactive precautions against the threat. The probability impact matrix can be seen in figure XX.
Accept
The acceptance of a threat is when one acknowledges the threat's existence without taking any action against it. By actively accepting a risk, a contingency plan can be made which is triggered when an event occurs. Threat acceptance can also include passive acceptance, which means doing nothing [2].
Escalate
Escalation is used when a project team agrees that the threat is outside the scope of the project or when the action exceeds the project manager's authority [2]. This could, for example, be change in laws that could have an effect on the project but the project team are not able to do any actions against it.
Opportunities
Opportunities are uncertainties and unexpected events that can effect the project positive and aid the project scope. Opportunities can be divided into five categories; Exploit, Share, Enhance, Accept/Ignore, Escalate.
Exploit The exploit strategy acts to ensure the identified opportunity occur (increase the probability to 100%). "Aggressive measures are taken which seek to ensure that the benefits from this opportunity are realised by the project" [9]. This strategy corresponds to the "avoid" response.
Share
The sharing strategy involves sharing the risk with a stakeholder who is better at securing the benefit of the risk opportunity [2]. This is done when the project manager acknowledge a higher value when sharing the opportunity to another stakeholder.
Enhance
The enhancing strategy seeks to increase the probability of the risk to occur. The opportunity of the risk also aims to increase the impact of the risk in order to maximize the benefit to the project [9]. "Early enhancement action is often more effective than trying to improve the opportunity after it has occurred" [2].
Accept/Ignore
Accepting or ignoring the opportunities is done when the risk has a minor impact on the project. The existence of the opportunity is acknowledged but no proactive action is planned [2].
Escalate
Escalation is used when a project team agrees that the threat is outside the scope of the project or when the action exceeds the project manager's authority [2]. This could, for example, be change in laws that could have an effect on the project but the project team are not able to do any actions against it.
Some project management theories exclude the Escalate strategy since in every project you cannot any take actions against them besides identify the risks and recognize that they are outside the scope of the project. This applies to both threats and opportunities.
Priority of Opportunities and Threats

When managing threats and opportunities it is important to prioritize the response strategy of the identified risks. In the previous section, the strategies are prioritized so that the strategies described first are the most important. It can also be seen in Figure XX, which shows the priority order of the responses [3]. When this approach is used, one will initially look at "Avoid" and "Exploit", as they have the greatest potential and impact on the project. The second priority is "Transfer" and "Share", here the search is for another stakeholder who can either manage the risk to maximize a opportunity or minimize a threat in order to control the impact of the risk. The third priority is "Mitigate" and "Enhance", which are used when it is not possible to avoid/exploit or transfer/share the risk. The last response strategy Accept/Ignore is used when the other response strategies have been considered and the risk is identified as being of minor importance/impact.
One way to do a qualitative risk analysis is by using a "Double Probability Impact Matrix" which is used to set up the identified risks and determine their likelihood and potential effect on the project objectives, allowing risks to be prioritised for further attention [9]. The "Double Probability Impact Matrix" will be described in the following section.
Probability Impact Matrix for Opportunities and Threats

The goal for risk treatment is to minimize the identified risks that have a negative impact, and to maximize the risks that have a positive impact. By using qualitative risk analyses, it is possible to determine their likelihood and potential effects on the current project objectives. The primary technique used is the Probability Impact Matrix, which makes it possible to prioritize the risks for further attention [9]. Each risk is assessed against some criteria and placed on a two-dimensional grid. The location of the risk on the matrix describes the significance of the risk, allowing the risk to be ranked. The "Probability Impact Matrix" is illustrated in figure 5, showing the areas of attention for threats and opportunities.
This approach is used to visualize both threats and opportunities in relation to their impact on the project. It may well be difficult to list the risks on the matrix, but by using this matrix the project manager can quickly get an overview of the identified risks he has to deal with. As can be seen in the figure, there is an "arrow of attention", which is the identified risks with the most positive/negative impact on the project. Hillson describe this area as "high-probability/high-impact risks are prioritised, since these are either "show-stopper threats" which must be avoided if possible or "golden opportunities" which must be exploited if possible" [9].
It should be noted, this matrix is not a "fixed" model as some organizations find it more advantageous to divide the matrix into two models, one for threats and one for opportunities. Other organizations also have the opportunity side mirrored. However, this results in you not having the possibility to create an "arrow of attention" for the risks in the model. However, it is important to note that the risk management process is an iterative process and it is therefore necessary to revisit the model several times.
Discussion/conclusion
abc
This paper aimed to highlight the importance of the risk management process and more specifically delve into risk treatment process.
Annotated Bibliography
Articles
- Project Management Institute, Inc. (PMI). (2021). A Guide to the Project Management Body of Knowledge (PMBOK ® Guide) – 7th Edition and The Standard for Project Management. (pp. 114-125). Project Management Institute, Inc. (PMI). [2]
- DESCRIPTION
- Danish Standards Association (2018), DS/ISO 31000:2018, Risk management - Guidelines. [1]
- DESCRIPTION
- There are unknown unknowns. Retrieved February 10, 2023. [6]
- DESCRIPTION
- Hillson, D. (2002). Extending the risk process to manage opportunities. International Journal of Project Management, (pp. 235–240). [9]
- DESCRIPTION
Books
- Hillson, David. "Effective Opportunity Management for Projects - Exploiting Positive Risk", 2003. Ch. 1. "The case for opportunity management". [3]
- Description
- Krogerus, Mikael. "The decision book: fifty models for strategic thinking", 2012. [4]
- Description
Transcript
- Rumsfeld, Donald. "Defense.gov News Transcript: DoD News Briefing – Secretary Rumsfeld and Gen. Myers, United States Department of Defense (defense.gov)". February 12, 2002. [5]
- A transcript of Donald Rumsfeld gave to a question at a U.S. Department of Defense (DoD) news briefing on February 12, 2002.
References
- ↑ 1.0 1.1 1.2 1.3 1.4 1.5 Danish Standards Association (2018), DS/ISO 31000:2018, Risk management - Guidelines, Retrieved from https://sd.ds.dk/Viewer/Standard?ProjectNr=M296412&Status=60.60&VariantID=41&Page=0
- ↑ 2.0 2.1 2.2 2.3 2.4 2.5 2.6 2.7 2.8 2.9 Project Management Institute, Inc. (PMI). (2021). A Guide to the Project Management Body of Knowledge (PMBOK ® Guide) – 7th Edition and The Standard for Project Management. (pp. 114-125). Project Management Institute, Inc. (PMI). Retrieved from https://app.knovel.com/hotlink/pdf/id:kt012LZJB1/guide-project-management/opportunities
- ↑ 3.0 3.1 3.2 3.3 3.4 3.5 3.6 3.7 Hillson, David. "Effective Opportunity Management for Projects - Exploiting Positive Risk", 2003. Ch. 1. "The case for opportunity management". Marcel Dekker Inc.
- ↑ 4.0 4.1 4.2 Krogerus, Mikael. "The decision book: fifty models for strategic thinking", 2012.
- ↑ 5.0 5.1 Rumsfeld, Donald. "Defense.gov News Transcript: DoD News Briefing - Secretary Rumsfeld and Gen. Myers, United States Department of Defense (defense.gov)". February 12, 2002. Retrieved from https://archive.ph/20180320091111/http://archive.defense.gov/Transcripts/Transcript.aspx?TranscriptID=2636#selection-1053.10-1053.342
- ↑ 6.0 6.1 There are unknown unknowns. Retrieved February 10, 2023. Retrieved from https://en.wikipedia.org/wiki/There_are_unknown_unknowns
- ↑ Geraldi, Joana; Thuesen, Christian; Oehmen, Josef; Stingl, Verena. "Doing Projects", 2022.
- ↑ Forsberg, K., & Mooz, H. RISK AND OPPORTUNITY MANAGEMENT. (1996). INCOSE International Symposium, pp. 586–598. Retrieved from https://doi.org/10.1002/j.2334-5837.1996.tb02057.x
- ↑ 9.0 9.1 9.2 9.3 9.4 9.5 9.6 9.7 Hillson, D. (2002). Extending the risk process to manage opportunities. International Journal of Project Management, (pp. 235–240). Retrieved from https://doi.org/10.1016/S0263-7863(01)00074-6
Made by Theis Sørensen (s195768)