Risk Register Analysis
Developed by Jonas Samuelsen
A Risk Register is a tool in the risk management strategy, to keep track of risks to a "project, program or portfolio"(PPP). It is commonly used by the project or risk manager to maintain the simplest structure of possible events but can be used on every level of "project, program and portfolio management"(PPPM). The Risk register describes possible threats and opportunities to a PPP. [1] The simplest risk register consists of the cause of a risk, the event of a risk, and the effect of a risk. The register can be expanded to include the information critical to the PPP. The level of information is highly related to the scale of the PPP, where large complex PPP tends to have more information included in the risk register, then smaller and simpler project. The main reason for having a risk register is to have a standing register with action plans already established for known possible risk. If a risk occurs, the project manager or risk owner(explained in the plan section) can take action fast and effective to remove or reduce threats or maximize opportunities.
Contents |
Introduction
A risk register consists of three main elements. It follows the same basics as the risk management strategy. [2] First and foremost it consists of the risk, secondly, it consists of the cause of the risk, and third it consist of the action of the risk. When building up a risk register these three elements will be covered by the following three steps. The first step is called Identify. Here all possible risk will be identified. The second step is called Assess. The possible risks identified must be evaluated regarding probability and impact on the PPP. The third step is called Plan. The management response is planned to ensure the if a risk materializes, the PPP is not taken by surprise. In all Phases, expert knowledge should be consulted. This includes Senior management, other PPP managers that have experience from similar projects, and specialist within specific areas[3]. Creating and populating the risk register tends to be an iterative process since new information can occur in the process and earlier steps need to reevaluated to find the optimal solution. During the lifetime of a PPP, the risk register should be evaluated to ensure the identification of possible new risk or a change in already known risks. The register should as a minimum be evaluated just before the starting of a new phase of the PPP. It is important that threats and opportunities are communicated to stakeholders. This is a continuous process during the lifecycle of the PPP, to ensure that everyone involved knows how to respond if a risk materializes.
Identify
The first step in creating a risk register is the identification of project context. This should be done with respect to the risk management strategy. [2] The context of a PPP is depending on several factors. This includes but is not limited to the organization environment such as legislation and governance requirements, Stakeholders involved in the project and the complexity and scale of the PPP. When the context has been established, the identification of possible risk can begin. When identifying risks, the cause, event, and effect of the risk should be established. Possible risk should include any possible events that can have an effect on the PPP. It is important to state that the risk register should only consist of risk relevant to the specific PPP. The key is to keep the register as short and precise as possible, without neglecting actual risks. It is important also to identify the risk owner of the risk. The risk owner is the one responsible for the risk being dealt with, but may not be the one that actually taking action if the risk materializes. A risk actionee is the one directly dealing with the risk. The risk actionee will be discused in the planning section. An example could be a new construction of an underground metro line. The line is set to be built in an urban area. The Project manager foresees a possible risk of noise complaints from residents living in the vicinity of the construction. This could lead to a hearing regarding working hours or compensation to the residents. The immediate effect on the project could be that the construction must be paused until the hearing committee decides the outcome, and the project could be delayed.
Risk identification techniques
In the process of identifying risks, several tools can be used. Some of the tools include a review of lessons learned, Risk checklists, brainstorm. These tools can then be used by the individual manager, or in risk workshops. During a risk workshop, the project manager or the designated lead should be able to use and facilitate the various identification tools listed below.
- A review of lessons learned [4] from similar projects can be a useful tool since risks is a direct consequence of uncertainty. Be reviewing similar PPP and their risk registers, uncertainty regarding threats and opportunities which directly affected the PPP can be minimized.
- Risk checklist or in-house list of risks, general to the organization's context can be used. They contain risks that are common across the organization, and should not be disregarded. This is a useful tool to register the most common risks.
- Brainstorm is a good way harness the combined knowledge of a group and can often be more productive than an individual[5]. It can also be used as a tool to clarify stakeholders opinion on already identified risks.
After the identification, all risk should be expressed in an unambiguous way, so that the risk cause, event, and effect cannot be misunderstood.
Assess
During the assessment of the risks identified, all risk should be estimated and the sum of risk to the PPP should be evaluated. The estimations of each risk include the probability of the risk materializes and the possible impact of the risk. The proximity of the risk should also be estimated to identify when the risk could affect the PPP if business, as usual, is followed. To estimate the risk, historical data should be used to determine the possible outcome of a risk. This data can in combination with different risk estimation techniques be used to make an estimation of the probability and impact. When all risks have been estimated, the total evaluation of the PPP should be carried out. The evaluation's purpose is to determined if the sum of risks, their likelihood, and their probability is within the tolerance of the organization. To evaluate the sum of risk, different risk evaluation techniques can be used. When assessing portfolio risk, the prioritizing of the risk should also be included. This creates the foundation for the management to decide where to allocate the organizational resources[6].
Risk estimation techniques
When estimating risk, some of the main tools is Probability trees, expected value, Pareto analysis, and Probability impact grid. Some of these techniques will have the greatest impact in a combination of each other.
- The Probability tree is a technique where historical data is used to create a graphical illustration of possible outcomes of risks and to visualize the risks to stakeholders.
- The expected value is a technique where the impact of a risk, in monetary values is combined with the probability of the risk. Following the example from early with the metro line and the noise complains, it could be estimated using the expected value technique. The probability of complaints is 10%, and the cost of the delay is one million Euro. Then the expected value would be the risk probability, 10% · impact, one million Euro = 100,000 Euro.
- The Pareto analysis ranks the risk in an order after the impact. This can be done in combination with the expected value technique. Then the Pareto analysis can be used by the management to determine where to start or focus the effort.
- The Probability impact grid is a way to quantify possible risk. One axis consists of the probability and the other axis consist of the impact factor. The probability is divided into segments representing intervals of probability. An example could be to divide the probability it into segments of 10 %. Then 0-10% would have the value of 0.1, 11-20 would have the value of 0.2 and so on. The impact factor is based on budget of the PPP. An example could be range from below 50,000 Euro to above one million Euro. Then below 50,000 Euro could have the value 0.05, 500,000 Euro could have the value 0.5 and above one million could have the value 0.9. Then a risk with a probability with a probability of 15% and an impact factor of 0.5, end up with a value of 0.2*0.5=0.1. The Organization can have a strategy regarding the value of the Probability impact grid. It could be that risks with a value of 0.15 or greater are unacceptable for the organization.
Risk evaluation techniques
To evaluate the sum of risks, several tools can be used. Two important tools are the Monte Carlo analysis, and the expected monetary value. The Monte Carlo analysis is a simulation tool that utilizes multiple randomly generated variables, with some specified given interval(the probability). Each variable represents a unique risk and then the simulation runs multiple iterations for the sum of risks.[7] The expected monetary value sums all the expected value from the estimation process. The outcome of the Monte Carlo analysis or the expected monetary value can then be used to determine the actions of the organization.
Plan
When all risks have been identified and assessed, the planning for the prober responds begins. In the planning consist of the actions to be taken if a risk materializes, and who should take action and execute the action plan. Those who should take action is called risk actionees. The should carry out the appropriate risk responds defined during the planning phase. When planning the response to threats, there are 6 possible responses. Avoid, Reduce, Fallback, Transfer, Accept, and Share[1]. The appropriate response should reflect the probability and impact defined during the assess phase.
- Avoid is when a threat both have high probability and high impact, the organization can normally not sustain them. Then the appropriate response should be to avoid them. This involves some degree of direct changes in the PPP.
- Reducing means to decrease the probability or the impact of a threat, by proactive measures. This is often done when a threat has high to very high impact or probability. An example could be the electricity at a hospital. If there is a blackout, the respirators don't work. To reduce that impact, a backup generator is installed.
- Fallback is similar to Reducing, but can only take the impact into account. Fallback can be treated as a plan B, that can be executed in the case of a threat materializes.
- Transfer is also similar to the Reduce response but does normally only take financial impact into account. The most common Transfer is the insurance at an insurance company. This will normally be the appropriate response for threats with high or very high impact and low probability.
- Accepting is when the risk should not be dealt with directly. This is due to the assessment that the cost of dealing with the risk is higher than the impact of the risk. The risk should still be monitored and reevaluated during the lifetime of the PPP, to ensure that there has been no change probability or impact.
- Sharing is when to organizations share the threat or the opportunity. In this way, both positive and negative effects will be divide into both organizations. This could be in the construction of a new sports arena. Company A will build the arena for municipality B. The contract is formed out with a budget of 10 million Euro plus Pain and Gain. This means that if the project goes over budget, company A and municipality B splits the extra cost. On the other hand, if the project goes under budget, the savings are split as well.
When planning the response to opportunities, there are four possible responses. Exploit, Enhance, Reject, and share which has been described above.
- Exploit is when an opportunity arises to changes a process and then get a resource gain. This could be in terms of equipment that has finished a task faster than expected. Instead of having the equipment standby, the equipment can be allocated to another task, and the overall project can save time.
- Enhance is to increase the impact or probability of an opportunity. This could be in terms of a rival leaving the market with only to competitors. There is now an opportunity to sell more products. To enhance the impact of the opportunity, they raise their prices slightly to increase their revenue.
- Reject is similar to the accepting of a treat. If the benefits of the opportunity are less then the cost, then the opportunity should be rejected.
Conclusion
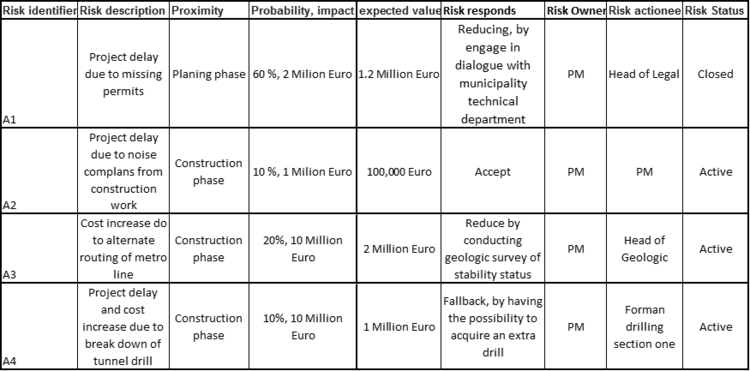
When all data has been acquired, risks have been identified, assessed and planned, then the complete risk register can be set up. It is now important to fill out the risk register with only the necessary data. All risks in the register should start with an identifier. This is to simplify and ensure that the correct distinction between the different risks. The Register could be populated according to table 1. When the Risk register is populated, the register should be distributed to the stakeholders engaged in the project. The communication of the register and changes should be done continuously through the lifecycle of the PPP. The Project manager, Risk owner, and risk responsible should evaluate the risk register from time to time. During the evaluation, the status and the composition of the risk should be considered. If the status or composition of a risk has changed, the risk has to be reassessed and replanned. The register should then be updated to account for the new situation.
An example of a populated risk register could be as table1. Here the most common attributes have been filled out. All risk has been assigned a risk identifier, in this case, A1-A4 for easy distinction besween the risks, and proper description has been established. When going through the risk register, it is then easy to evaluate the different risks.
Limitations
The risk register does only take into account specific forecast for known unknowns, with clear inputs and outputs. Therefore the management has to agile to account for unknown unknowns[8]. If the register should be of use, it has to be updated during the lifecycle of PPP. It a risk assessment in the register gets outdated, the response might not be the appropriated anymore.
References
- ↑ 1.0 1.1 Managing Successful Projects with PRINCE2. http://proquestcombo.safaribooksonline.com.proxy.findit.dtu.dk/9780113310593
- ↑ 2.0 2.1 Risk management strategy. http://apppm.man.dtu.dk/index.php/Risk_management_strategy
- ↑ PMI - A Guide to the Project Management Body of Knowledge . http://proquestcombo.safaribooksonline.com.proxy.findit.dtu.dk/book/software-engineering-and-development/project-management/9781935589679/firstchapter
- ↑ Lessons learned. http://apppm.man.dtu.dk/index.php/Lessons_learned_-_a_tool_for_sharing_knowledge_in_project_management
- ↑ Brainstorm. http://www.designkit.org/methods/28
- ↑ PKI - THE STANDARD FOR PORTFOLIO MANAGEMENT. http://proquestcombo.safaribooksonline.com.proxy.findit.dtu.dk/9781933890531
- ↑ Monte Carlo Simulation. http://apppm.man.dtu.dk/index.php/Monte_Carlo_Simulation_of_Risk
- ↑ Characterizing unknown unknowns. https://www.pmi.org/learning/library/characterizing-unknown-unknowns-6077
Annotated Bibliography
This article has been based on the Prince2 standard with additional appending views from the PMI standard. To get the full value of this article, the reader should be familiar with these standards for Project, Program and portfolio management.
Managing Successful Projects with PRINCE2
The PRINCE2 standard gives a detail description of the different tools used in this article. It is important to understand that not all tools from the PRINCE2 standard must be used during the risk register analysis. The composition of the risk register should be decided by the manager of any given project, Program or Portfolio.
The PMI standards
The PMI standards for project and portfolio management is similar to the PRINCE2 and gives a good overview of different tools for project management.