Risk analysis
Developed by Johannes Michael Bührmann
- main article: Risk Management
Contents |
Summary
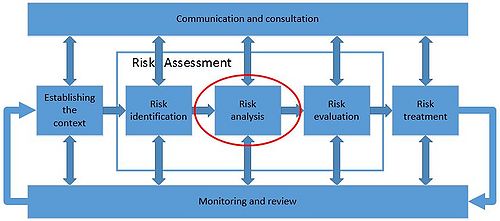
This article will describe the element of risk analysis within risk management, what it is used for and list several elements which can be used in the process of managing risk in projects, portfolios and programs.. Since risk analysis is a subpart of Risk Management, several correlations might be present between the two.
Several methods used for Risk Analysis will be mentioned and explained briefly, but (in order to allow the full use of the wiki) not be described in detail. Some of them might not seem directly applicable but can all be used during the possible iterations within the analysis.
The user of risk analysis essentially choose the most appropriate method(s) for calculating the given information and delivers a collective overview of the situation, as an artisan chooses the right tool for the job and produces the individual parts for the product. Using “known knowns” and “known unknowns” (from the Cynefin framework) along with estimates made by either extrapolation based on prior knowledge or by experts, the analysis generates a better understanding enabling the user to conduct a valid risk evaluation.
Definition
Risk analysis lies at the heart of Risk Management and functions very much like the Central Processing Unit (CPU) of a computer.
The term "Risk" is most often defined as a probability of losing something of a specific value. Mathematically speaking; the probability of an event occurring multiplied by the potential value-loss = the risk.
In order to compute this risk the person(s) doing the analysis must as a minimum receive information on the probability of an event occurring and the value of the potential loss. The definition of risk analysis, as defined by the International Organisation for Standardization is as follows:
In their ISO Guide 73-2009, it is stated as the “Process to comprehend the nature of risk and to determine the level of risk” In the ISO 31000 standard it is described as the process which “provides an input to risk evaluation and to decisions on whether risks need to be treated, and on the most appropriate risk treatment strategies and methods” .
Both are correct since the process mentioned is the computational part of Risk Management where different aspects, variables and factors are used to estimate the risk involved with a specific feature, action, decision, condition etc. The outcome of this computation is a quantified number or percentage which can then be used as an evaluation criterion, determining either which option to select or if it is safe to proceed down the investigated path.
Main features of risk analysis
There are three different analysis method groupings within risk analysis; Qualitative, Semi-Quantitative and Quantitative.
- Qualitative
- Qualitative analysis methods are based on opinions and estimates. They compute the risk scenario based on few numbers and many interpretations. Outcome of these methods are usually given in levels of significance like “high”, “medium” and “low” or other "word scales" which are not specifically determining any actual number. An example of a qualitative result is the risk of terror when travelling abroad, made by the ministry of foreign affairs.
- Semi-quantitative
- The outcomes of the semi-quantitative analysis methods are based on numeric ratings using evaluation scales for probability and consequence and usually combining them using a formula, resulting in a comparable value for the risk level.
- Quantitative
- The quantitative analysis uses estimates of probability and consequence values to generate an approximation of the risk involved, represented by one specific value. The specific values, depending on the method of gathering, from different analysis can then be combined into one overall risk factor.
Because risk analysis works much like the processor in a computer it needs to receive a minimum of information as input before it can calculate an output which allows the user to gain a better overview and basis for making changes or taking decisions. A risk analysis is often generated for the sake of factual argumentation and credibility of decisions. Normally input are generated in the step before the analysis; "Risk identification" but some can also be derivatives generated during the analysis. Many of the models described later can be used to generate input during the identification stage. Output of the analysis step is usually used within the "Risk evaluation" in order to understand the risk in question.
| Input: | Output: |
;Purpose
|
;Assessment of the risk with the following aspects
|
;Type of risk
| |
;Information available
| |
;Existing control features
| |
;Effectivity of existing control features
|
;Description of the confidence in:
|
;Consequences
| |
;Likelihood / Probabilities
| |
;Risk criteria
| |
;Causes of risk
|
;Limitations
|
;Sources of risk
| |
;Factors influencing any of the above
| |
;Interrelations / Interdependence
|
Benefits of analysing risk
Analysing risk has become an integrated part of working with forecasts as well as decisions in projects, programs and portfolios, simply because it generates the big picture needed to make an informed decision. The drivers of analysing risk are the focus on lowering costs and expenses, avoiding loss of anything valuable and reducing variability in outcomes. The reason why risk is analysed with so many different methods to choose from, is because several different categories of risk exist, and yet there is a universal consensus that risk is best avoided, mitigated, minimised or negated.
Models used in order to analyse risk
All but one of the following models are described in Annex B of the ISO 31010 standard.
- Brainstorming is a very intuitive method which uses associations and connections made by possibly several people around a central subject to uncover problematic and opportunistic aspects affecting the subject. This qualitative information is then used to gather as much quantitative information as possible in order to complete the further analysis. It can e.g. be used to imagine future risks or possible control features to known risks.
- Structured or semi-structured interviews:
- The structured or semi-structured interview can be used for gathering information from numerous sources. These interviews do not have to be done face to face since questionnaires are also considered within this model. Applicable in the phases before and after Risk Analysis.
- The Delphi technique is essentially a brainstorming process where the participants are kept anonymous but are able to see the collected work of all participating in the process. It is used to reach some kind of consensus around the subject in question. Applicable in the phases before and after Risk Analysis.
- Check-lists:
- Check-lists are built from previous experiences and often list known risks, control features and/or hazards gathered through prior assessments or lessons learned.
- PHA is used when there is little information available and as the name states normally in the beginning of e.g. a project, in order to uncover potential hazards influencing the further development.
- HAZOP is a qualitative method which studies the current activities in order to access the risk involved. It usually examines existing operations like procedures and products as well as processes and the system around them.
- HACCP is mainly used in the industry which produces items for consumption where infections are of vital importance. The critical control points are then indicating areas within the production where errors can lead to loss of quality or worse.
- Toxicity assessment:
- Toxicity assessment is used when looking at risk related to the environment and how the introduction of a source of harm affects it.
- SWIFT is normally used at workshops by the facilitator to make the participants introduce risk into their chain of thought by using a set of specific questioning words along with the catchphrase “what if?” .
- When conducting a scenario analysis, one or several future scenarios are developed based on the participants’ thoughts and ideas on where the future might bring us. Then doing back-casting in order to determine the events needed to reach the scenario and evaluating the risks of these events.
- Business impact analysis (BIA):
- The BIA investigates the risks capable of disrupting the organisation’s operations as well as the current controls in place and how well they will handle the disruption.
- RCA is often used after an event has taken place with the aim of preventing it from happening again.
- By constantly questioning for the reason why an event occurred, turning the reason into an event and repeating the question the RCA attempts to discover the fatal event which set several chains of actions into motion.
- Failure modes and effects analysis (FMEA) / failure modes and effects and criticality analysis (FMECA):
- FMEA is essentially an error tool attempting to map out the different possible ways for processes, systems or components are able to fail and thus not fulfil the designed purpose.
- FMECA expands FMEA by ranking the outcomes against each other and thereby identifying the most critical failures.
- FTA is a method used to develop your typical trouble shooting guide where it is possible to locate the cause of an undesired event by deductive reasoning.
- ETA can be used to generate the probability of the control features working or not working with regards to a specific event happening. Contrary to the FTA, the ETA can be used before the event has actually happened as a hypothetical reasoning method. It can be used both quantitative and qualitative.
- Cause-consequence analysis:
- Cause-consequence analysis is combining FTA and ETA in order to analyse the various paths possible within a system following a critical event. It is used within critical safety systems as a reliability tool.
- Cause-and-effect analysis identifies potential causes of an event or problem by looking at the possible contributing factors and organising them in either a fishbone or tree diagram in order to consider all possible hypotheses.
- Layers of protection analysis (LOPA):
- LOPA analyses if the required control features are present to mitigate an undesired event or scenario. It is a semi-qualitative method used to provide a baseline when specifying independent protection layers.
- Decision tree analysis can be used as a forecast tool, assisting the decision makers with understanding the consequences and follow-up decisions to an initial event. It resembles a tool usable for career path decisions where you start with a lot of options and by deciding on one path, still having several options open.
- HRA is mainly used to evaluate the human influence on performance of systems or the human error factor.
- It is usable both quantitatively and qualitatively.
- The bow tie analysis generates a graphical representation which assists in generating the full picture of what has to happen prior to an event (causes) and what can happen afterwards (consequences). It is mostly generated in a brainstorming session.
- RCM identifies policies which need to be implemented in order to achieve the required safety by managing failures effectively and efficiently.
- Sneak analysis (SA) / sneak circuit analysis (SCI):
- SA and SCI are used for identifying design errors which may cause harm to production or personnel or just generate an undesired outcome.
- The Markov analysis is used when the future state depends only on present state of a system. It is a quantitative method which can be described with discrete or continuous states.
- Simulating complex systems can be the only way to grasp how uncertainties affect them. The Monte Carlo simulation is used for this.
- This is a probability theory using Bayes Theorem to sum up several probabilities in to one.
- FN curves:
- These curves are used in relation with casualties in a specified population affected by an event.
- Risk indices:
- This semi-quantitative measure generates a risk index derived from scorings of normal scales, and is used as a classification system.
- Consequence/probability matrix:
- As the name suggests it is a matrix combining qualitative or semi-qualitative consequences with probabilities in order to generate a risk rating. This matrix can then be used to rank different risks treatments or risk sources.
- The CBA is often used to see if it is worth it to go ahead with changes to status quo, and mainly on a financial level.
- By using several different criteria the MCDA assesses the overall positive value of a set of options, transparently and objectively. It aims to sort the options in order of preference.
- Fuzzy synthetic evaluation (FSE) approach:
- Described in the International journal of Project Management 31 (2013) it is an intuitive method which starts out identifying the risk factors, evaluating a specific risk using both quantitative and qualitative values and by combining them generating a matrix of numeric risk values. After determining the evaluation criteria each criteria is given a weight which is combined with the risk matrix into a fuzzy evaluation matrix. The risk index is then calculated and the overall risk evaluated after each risk is given a weight of it’s own.
Reference
ISO Guide 73-2009 – Risk Management Vocabulary (2009)
ISO 31000 - Risk management - Principles and guidelines (2009)
ISO 31010 - Risk management (2009)
International Journal of Project Management 32 (2014) - Vahid Khodakarami , Abdollah Abdi - Project cost risk analysis: A Bayesian networks approach for modelling dependencies between cost items
International Journal of Project Management 31 (2013) - Jialin Liu, Quanxi Li, Yuhan Wang - Risk analysis in ultra deep scientific drilling project – a fuzzy synthetic evaluation approach
Project Management Journal (April 2013) - Juliane Teller - Portfolio Risk Management and Its Contribution to Project Portfolio Success: An Investigation of Organization, Process, and Culture
Links
Only the following links are internal in the APPPM-wiki, All others are to Wikipedia.org and may be replaced when the APPPM-pages has been written, and added to this list.
Once all links are internal, this section can be deleted.