Risk Management Overview
(→Abstract) |
(→ISO 31000) |
||
| Line 129: | Line 129: | ||
Above-mentioned can be conceptualized, measured and described in a more and understandable way than the ISO 31000, for instance, the SRA glossary <ref name="CriticArticle" />. | Above-mentioned can be conceptualized, measured and described in a more and understandable way than the ISO 31000, for instance, the SRA glossary <ref name="CriticArticle" />. | ||
Therefore it is important that risk managers not blindly follow the ISO 31000, but try to explore as broad a literature search as possible, for instance, the SRA glossary. | Therefore it is important that risk managers not blindly follow the ISO 31000, but try to explore as broad a literature search as possible, for instance, the SRA glossary. | ||
| + | |||
| + | |||
| + | The ISO 31000 "''provides generic guidelines, it is not intended to promote uniformity of risk management across organizations.''" | ||
== Conclusion == | == Conclusion == | ||
Revision as of 10:27, 12 February 2018
Contents |
Abstract
Projects are part of a dynamic and fast changeling world. Therefore there is a degree of uncertainty and unpredictability in projects. In order to minimize uncertainties and unforeseeable events related to a project, risks are identified and managed throughout the project lifecycle. A risk is an uncertain event that can have e negative effect on one or more objects in a project such as time, cost, performance or scope [1] [2].
In order to control and manage risks, the Risk Management Process (RMP) is used. RMP is divided into four main categories Identify risks, Assess risks, Treat risks and Monitor risks. However, RMP is a continuous process, which happens throughout the lifecycle of a project. [2] [3]
The different natures of risks can be categorized with D. Rumsfeld's Unknown-Knowns and assessed with the risk matrix (both residual- & inherent risk). When treating the risk the Risk managers can choose to Avoid, Reduce, Share or Accept the risk. The risks can be monitored by using a risk register, where risks and countermeasures can be mapped.
Risk management is an impotent tool to use in project management and helps managers get an overview of potential obstacles that can occur or prevent a team from achieving their goals. Risk management is highly impotent discipline and is therefore present in all projects, however, it's importance is often neglected. [2]
This Wiki-article will describe the Risk Management Process, Risk Matrix, Rumsfeld's Unknown-Knowns, inherent- and residual risks. At last limitations and advantages of Risk Management will be discussed and a brief overview of other relevant reading material.
Please note that this article only covers the risk (threat) management of a project and does not look into opportunities management (risks with a positive effect).
Introduction
Risk definition
Risk can be defined as follows: "Risk is an uncertain event or condition that it occurs, has a positive or negative effect on one or more project objectives such as time, cost and quality, or effect of uncertainty on objectives" All activities in an organization involve risks. These risks can be managed by identifying it, analyzing it and then evaluating whether the risk should be modified by risk treatment in order to satisfy the organization's risk criteria. During this process, risk managers communicate with stakeholders and monitor the risk. The controls are modified in-order to ensure that the amount of risk treatment is minimized. [p. V][2]
Risk identification (RI) is the "process of finding, recognizing and describing risks" [p. 4][2]. RI involves the identification of risk sources, event, causes and potential consequences. The identification can involve historical data, theoretical analysis, expert opinions, and stakeholder needs [p. 4][2].
However identifications are only the first step, managers also need to analyze the risk to the most significant ones can be dealt with on an ongoing basis [p. 219][4].
Rumsfeld's Unknown-Knowns
The different nature of risks can be categorized with former US Defense Secretary, Donald Rumsfeld's definition. Rumsfeld categorizes risks as the following [5] :
- Known-Knowns describes the things we know we know. An example could be the fact that we know that there are some risks in every project or maybe learning's from a previous project.
- Known-Unknowns describes the things we know are uncertain. For example, the delays because of a third party fail to deliver on deadline or human errors administration wise or misunderstandings.
- Unknown-Unknowns describes the things that we in no way could have seen or expected. This could be a sudden death, war or terrorist attack.
- Unknown-Knowns describes the things we should have known, but we for various reason (mostly complexity) don't. An example could be when a terrorist attack happens on American solid, to some extent, this is an Unknown-Known for the CIA [p. 219-220][4].
Risk Matrix
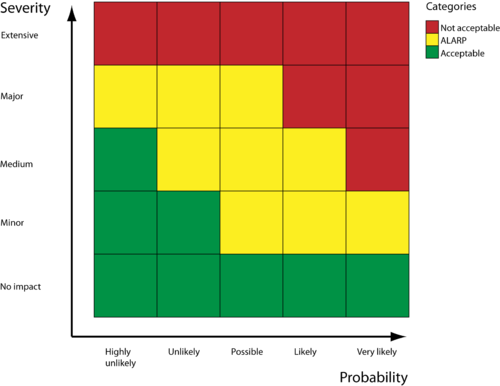
When the risk elements to be managed is identified, the next step is to ensure that either the likelihood is reduced or the impact of that activity occurring.
The risk matrix is one of the most used tools for risk evaluation. The matrix can be used to determine the size of a risk & whether or not a risk is sufficiently controlled.
The risk-matrix is compiled of two dimensions Probability (also called likelihood) and Severity (also called impact). Likelihood is the measure of how likely a given event is, and impact is the effect the risk can do. The combination of these two dimensions gives a collective risk rating in the matrix. Usually, the risk-matrix consists of 3 different risk ratings: Low (Acceptable), Medium and high (Not acceptable), however, some matrices also have a 4. level very high [6].
The horizontal and vertical scale can have different values or tags, however, in this case, both impact and probability have a scale from 1-5. An example of a risk rating could have a probability of 3 (possible) and an impact of 2 (Minor) would have a collective risk ration of medium [p. 223][4].
The numeric scale of 1-5 can be hard for managers to visualize and use, therefore more subjective values like unlikely and likely is often used, as seen in the table below.
| Scale (1-5) | Likelihood (Subjective values) | Impact (Subjective values) |
|---|---|---|
| 1 | Highly unlikely | No impact |
| 2 | Unlikely | Minor |
| 3 | Possible | Medium |
| 4 | Likely | Major |
| 5 | Very likely | Extensive |
It is important to notice that the risk matrix is only used to rank risks, and not as a decision tool itself. How to treat the individual risk the matrix does not answer - other tools and a deeper analysis should be used for this. The tool, however, can be used to prioritize and categorize the risks.
Residual - & Inherent risks
Identified risks can be categorized into two different categories, depending on, if controls fail or not. The residual risk is the identified risk as it is today, with the controls in place. An example could be the risk of "financial loss if the bank is robbed", however, we have a control in place and hired security people. The inherent risk is the risk we face if the controls for the residual risk fail. For instance, all the security people get food poisoning, and the bank's protection is therefore gone. Naturally the Impact/Probability for the inherent risk should be grater or equal to the ratings in the residual [2] [7].
Risk Management Process (RMP)
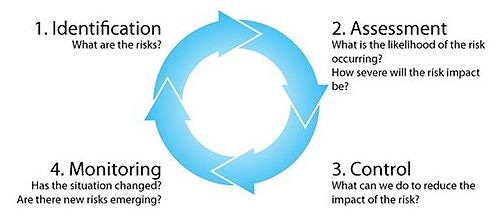
The risk management process can be divided into four main categories Identify risks, Assess risks, Treat risks and Monitor risks.
Identify risks
The first process is "Identify risks", here potential risk events and their characteristics that can have a negative effect on the project is identified. The identification of risk is a repeatable process since new risks can change through its life or new risks are discovered. The identification process can consist of a variety of different stakeholders, project management team, experts, senior managers etc.
Assess risks
The second process is "Assess risks", which is used to measure and prioritize risks. In the assessment of risks the probability of each risk occurring & the corresponding impact for the project, if the risk does occur. The probability and impact are then used to prioritize the risks. This process is also repetitive throughout the project. The #Risk Matrix, as described earlier, can be used for accessing the risks.
Treat risks/Control
The third process is "Treat risks", here actions to reduce risks, are developed and determined. The treatment of risks can consist of adding additional resources (manpower, budget) into the schedule. However, the treatment should be customized to fit the individual risk and be as realistic and cost-effective as possible. The process also includes measures to avoid, mitigate or deflect the risk. Another possibility is to develop contingency plans which can be used if the risk occurs [p. 138][1].
Risk Treatment consists of a range of options for mitigating the risk, assessing options, and preparations for implementing action plans. As mentioned earlier the highest risks should be addressed first and so on and forth. Of course, the cost of treating the risk should be evaluated and compared whit potentially loss by risk. Depending on the type and nature of the risk, the following options are available [9]:
- Avoid - The risk is avoided by stopping to proceed with the activity that introduced the risk. Instead, an alternative activity that still meets business objectives is chosen or a less risky approach or process.
- Reduce - The likelihood or effect of the risk is reduced to an acceptable level. However in regards to time and expense, it is desirable to eliminate the risk [4].
- Share or Transfer - The risk is transferred away from the risk-owner. For instance by outsourcing the activities that the risk is tied to, making contracts with service providers or buying a insurance that covers that risk.
- Accept - The risk is simply accepted, risks with very low impact and likelihood can often be accepted. A risk can also be accepted if the cost of the treatment outweighs the benefit. By accepting the risk no further action is taken to treat the risk, the risk is of cause still monitored and evaluated on an ongoing basis, do to potentially changes [9].
Monitor risks
The fourth process is "Monitor risks", here actions to track and monitor risks are developed. One of the most common approaches to risk monitoring is to use a risk register, which is initiated in the start of a project and continually reviewed and updated. A risk register should as a minimum contain the following information:
- Risk identification number (Used for identification of risks)
- Risk Owner (Should be clearly defined and registered in the risk register)
- Description of Risk (Makes it easier to communicate risk)
- Results of assessment (Probability/Impact) and assessment date
- Mitigating Actions (Actions to address the risk)
- Date for next risk review [8].
It is impotent to note that risks should be monitored, reviewed and controlled on an ongoing base. The controlling of a risk is done by continuous tracking of identified risks while identifying and analyzing new risks. Risks and the effectiveness of controls and mitigations should be evaluated throughout the project life cycle [p. 142][3].
Limitations and advantages of RPM (discussion)
ARTA diagrams are included for risk treatment and control????? XXX
ISO 31000
Even though risk management indisputably is beneficial, most managers use the ISO 31000 standard, which has some critical flaws.
First, a considerable amount of scientific literature arguing for the ISO 31000 is outdated since it uses ideas of risk assessment and characterization as used in the 1970s and 1980s [10].
Furthermore, a significant proportion of management researchers and analysts agrees on risk basically captures two dimensions:
- something is at stake (health and lives, the environment and material assets)
- uncertainties.
Above-mentioned can be conceptualized, measured and described in a more and understandable way than the ISO 31000, for instance, the SRA glossary [10]. Therefore it is important that risk managers not blindly follow the ISO 31000, but try to explore as broad a literature search as possible, for instance, the SRA glossary.
The ISO 31000 "provides generic guidelines, it is not intended to promote uniformity of risk management across organizations."
Conclusion
It is important that managers use risk management, and spent time on improving and develop the risk management programme of companies. xxx
There will always be risks in projects, and how they are managed will have a large impact on the success of a project [p. 232] [4].
Litterature
References Credibility
This section contains a brief discussion of the used online sources credibility. This is done to ensure transparency and provide a high-quality list of sourcing which the reader can follow up on.
- [3]: Is written by the Office of risk management at Georgetown University and can, therefore, be seen as an academically valid source.
- [6]: Is written by CGE Academy which is a information site created by the company CGE - Risk Management Solutions. CGE is a multinational company which specializes in risk management solutions. The company has over 10.000 end users and a 21% growth over the last five years and it is fair to say that CGE is a reliable source considering Risk Management. (https://www.cgerisk.com/about-us/) Last modified 24-07-2017
- [7]: Nasdaq BWise is a global company which helps streamline risk management activities, furthermore the information from their webpage was compared with information from the ISO 31000 [2]. (http://www.bwise.com/about) Last modified 29-09-2015
- [5]: Wikipedia is often criticised for is reliability since everybody can edit the pages. However, since this source is used in combination with the book Project Management by H. Pearson [4] and since this article is a Wikipedia itself, this is not a huge issue. Last modified 02-02-2018
- [9]: Is written by Chartered Accountants, which is a New Zealand based, they provide business and finance support to over 100.000 members. They are a huge company and therefore must have a lot and specialized knowledge within their field. Furthermore the ISO 31000 [2] is used as a reference , on the page. (https://www.charteredaccountantsanz.com/about-us)
- [8]: Procurement Journey is a webpage written by the Schottish Government (http://www.gov.scot/About) and can be seen as a credible source. Last modified 2016
However, a more general critic of the use of online source could be based on the following:
- Information available on the Internet is not regulated for quality or accuracy.
- Almost anyone can publish anything they wish on the internet.
- The information on a given webpage can change over time.
- The information can be outdated.
- Information can be twisted to reflect a person or companies interests.
As earlier stated the used online sources are relatively credible (point 1-2). When considering the change and outdatedness (point 3-4) the webpages was last edited between 29-09-2015 and 02-02-2018, which is relatively new and relevant. Since all the internet pages used are on a factual and information level, and not analytical they risk of exposure to company interests are minimal (point 5). In conclusion, the used internet pages are credible sources.
References
- ↑ 1.0 1.1 J. Geraldi, C. Thuesen and J. Oehmen, "How to Do Projects", Dansk Standard, (2017):.
- ↑ 2.0 2.1 2.2 2.3 2.4 2.5 2.6 2.7 2.8 ISO, "31000 Risk management — Principles and guidelines", INTERNATIONAL STANDARD, (2009):.
- ↑ 3.0 3.1 3.2 Georgetown University, "RISK MANAGEMENT OVERVIEW", https://riskmanagement.georgetown.edu/overview, Visited 10-02-2018
- ↑ 4.0 4.1 4.2 4.3 4.4 4.5 H. Pearson, "Project Management", Pearson Education Limited, 4th. Edition (2010):.
- ↑ 5.0 5.1 Wikipedia, "There are known knowns", https://en.wikipedia.org/wiki/There_are_known_knowns, Visited 03-02-2018
- ↑ 6.0 6.1 6.2 CGE Academy, "Risk matrices", https://www.cgerisk.com/knowledgebase/Risk_matrices, Visited 05-02-2018
- ↑ 7.0 7.1 Nasdaq, "ASSESSING RISKS: INHERENT OR RESIDUAL", http://www.bwise.com/blog/assessing-risks-inherent-or-residual/obj5382859, Visited 08-02-2018
- ↑ 8.0 8.1 8.2 Procurement Journey, "Risk Management Process", https://www.procurementjourney.scot/risk-management-process, Visited 10-02-2018
- ↑ 9.0 9.1 9.2 Chartered Accountants, "Treat Risks", https://survey.charteredaccountantsanz.com/risk_management/midsize-firms/treat.aspx, Visited 09-02-2018
- ↑ 10.0 10.1 T. Aven, "The flaws of the ISO 31000 conceptualisation of risk", Proceedings of the Institution of Mechanical Engineers, Part O: Journal of Risk and Reliability, 5 (2017):.
Cite error: <ref> tag with name "iso31000sme" defined in <references> is not used in prior text.
Cite error: <ref> tag with name "RiskTreatBook" defined in <references> is not used in prior text.